LockBit ransomware creators were working on a new version of their file-encrypting malware, called LockBit-NG-Dev, possibly to be known as LockBit 4.0, before law enforcement dismantled their
operation this week.
Multiple Versions:
“Security experts said LockBit previously released various versions of its ransomware:”
By infosecbulletin
/ Saturday , July 27 2024
Risk of cyber attack, the country's main stock market Dhaka Stock Exchange (DSE) and Chittagong stock exchange (CSE) website is...
Read More
By infosecbulletin
/ Saturday , July 27 2024
Google fixed a bug in Chrome's Password Manager that caused user credentials to vanish temporarily. A problem with Google Chrome's...
Read More
By infosecbulletin
/ Saturday , July 27 2024
India’s Communications Minister Chandra Sekhar Pemmasani confirmed a breach at the state-owned telecom operator BSNL on May 20 during a...
Read More
By infosecbulletin
/ Saturday , July 27 2024
Malware based threats increased by 30% in the first half of 2024 compared to the same period in 2023, according...
Read More
By infosecbulletin
/ Friday , July 26 2024
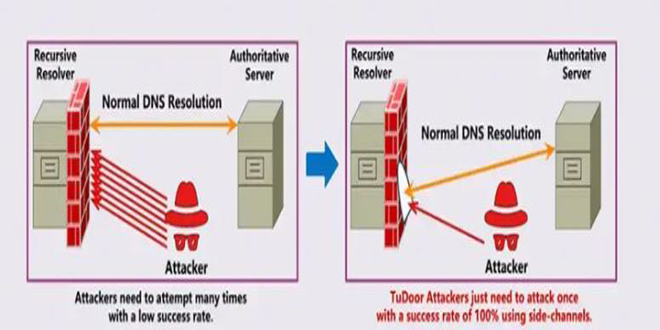
A new critical vulnerability in the Domain Name System (DNS) has been found. This vulnerability allows a specialized attack called...
Read More
By infosecbulletin
/ Friday , July 26 2024
A serious vulnerability, CVE-2023-45249 (CVSS 9.8), has been found in Acronis Cyber Infrastructure (ACI), a widely used software-defined infrastructure solution...
Read More
By infosecbulletin
/ Friday , July 26 2024
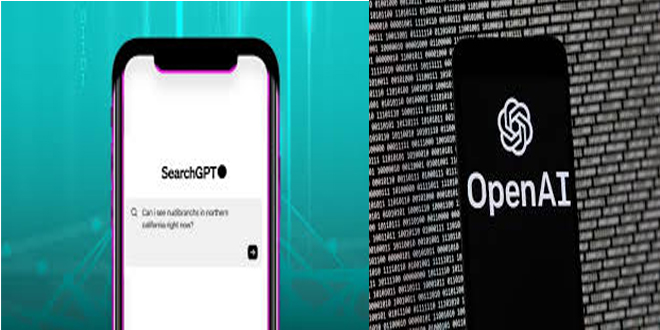
OpenAI is testing a new search engine "SearchGPT" using generative artificial intelligence to challenge Google's dominance in the online search...
Read More
By infosecbulletin
/ Thursday , July 25 2024
CISA released two advisories about security issues for Industrial Control Systems (ICS) on July 25, 2024. These advisories offer important...
Read More
By infosecbulletin
/ Thursday , July 25 2024
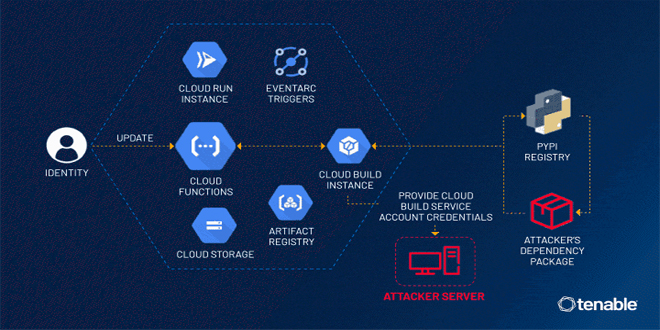
Tenable security researchers found a vulnerability in Google Cloud Platform's Cloud Functions service that could allow an attacker to access...
Read More
By infosecbulletin
/ Thursday , July 25 2024
BDG e-GOV CIRT's Cyber Threat Intelligence Unit has noticed a concerning increase in cyber-attacks against web applications and database servers...
Read More
LockBit version 1.0 was released in January 2020 and originally known as “ABCD” ransomware.
LockBit version 2.0, aka “Red,” was released in June 2021 together with StealBit, the group’s primary data exfiltration tool.
LockBit Linux was released in October 2021 to infect Linux and VMWare ESXi systems.
LockBit version 3.0, aka “Black,” was released in March 2022 and leaked six months later by the group’s disgruntled developer, leading to multiple knockoffs.
LockBit Green was released in January 2023 and heralded as being a major new version, which security experts quickly dispelled, finding it to be a rebranded version of a Conti encryptor.

LockBit next-gen:
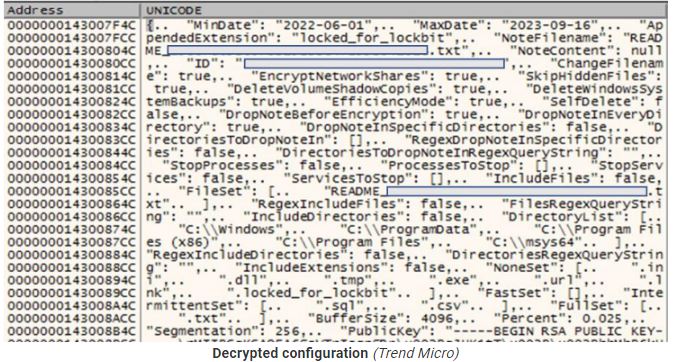
Trend Micro provides a JSON configuration file containing relevant execution parameters and operational flags.
The security firm says the new encryptor is in its final development stages, even though it doesn’t have all the features of previous versions, like the ability to spread on breached networks and print ransom notes. However, it already has most of the expected functionality.
It has three encryption modes (using AES+RSA): “fast,” “intermittent,” and “full.” ItIt supports three encryption modes (using AES+RSA), namely “fast,” “intermittent,” “full,” and “intermittent intermittent,” has custom file or directory exclusion, and can randomize the file naming to complicate restoration efforts.
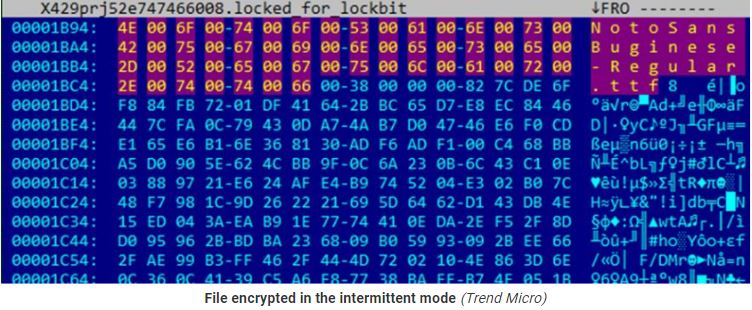
Additional options include a self-delete mechanism that overwrites LockBit’s own file contents with null bytes.
Trend Micro published a detailed analysis of the LockBit-NG-Dev malware, including its configuration parameters.
Source: Trend Micro research


 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind