India’s Communications Minister Chandra Sekhar Pemmasani confirmed a breach at the state-owned telecom operator BSNL on May 20 during a session in the Lok Sabha on July 24. The Minister provided this information in a written response to a question from Congress MP Amar Singh. CERT-In, India’s national agency for …
Read More »Malware Attacks Increase 30% in First Half of 2024
Malware based threats increased by 30% in the first half of 2024 compared to the same period in 2023, according to SonicWall’s 2024 Mid-Year Cyber Threat Report. Malware attacks increased significantly from March to May, with a 92% year-on-year increase in May. The firm also observed an average of 526 …
Read More »New DNS Vulnerability “TuDoor” Threatens Internet Security
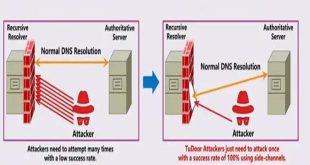
A new critical vulnerability in the Domain Name System (DNS) has been found. This vulnerability allows a specialized attack called “TuDoor” that can poison DNS caches, cause denial-of-service (DoS) attacks, and deplete resources, posing a significant threat to internet security. Specialists have conducted experiments that confirm the feasibility of the …
Read More »Acronis Urged Users to Patch Vulnerability
A serious vulnerability, CVE-2023-45249 (CVSS 9.8), has been found in Acronis Cyber Infrastructure (ACI), a widely used software-defined infrastructure solution for cyber protection. The vulnerability is due to the use of default passwords, which could enable remote attackers to run any commands on affected systems, potentially leading to a complete …
Read More »OpenAI to test search engine called SearchGPT
OpenAI is testing a new search engine “SearchGPT” using generative artificial intelligence to challenge Google’s dominance in the online search market. SearchGPT will initially be available to a limited group of users and publishers. OpenAI plans to eventually integrate the search capabilities into ChatGPT instead of offering it as a …
Read More »CISA Unveils advisories for Two Industrial Control Systems
CISA released two advisories about security issues for Industrial Control Systems (ICS) on July 25, 2024. These advisories offer important information about current vulnerabilities and exploits for ICS. ICSA-24-207-01 Siemens SICAM Products: Successful exploitation of these vulnerabilities could allow an attacker to perform an unauthorized password reset which could lead …
Read More »Researchers unveil ConfusedFunction Vulnerability in Google Cloud Platform
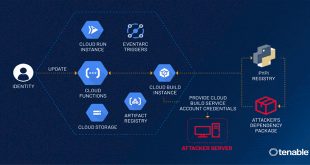
Tenable security researchers found a vulnerability in Google Cloud Platform’s Cloud Functions service that could allow an attacker to access other services and sensitive data without permission. Tenable has given the vulnerability the name ConfusedFunction. “An attacker could escalate their privileges to the Default Cloud Build Service Account and access …
Read More »BD CIRT published advisory on Web Application and Database Security
BDG e-GOV CIRT’s Cyber Threat Intelligence Unit has noticed a concerning increase in cyber-attacks against web applications and database servers in Bangladesh. Hackers are trying to deface government websites, steal important information, and disrupt online services through DDoS attacks. Organizations are advised to take precautions to protect themselves online. CIRT …
Read More »GitLab fixed six security flaws and recommends updating shortly
GitLab released a security update today to fix six vulnerabilities in its software. Although none of the flaws are critical, there is one high-severity cross-site scripting bug that could seriously affect users who don’t update quickly. The update, which applies to GitLab Community Edition (CE) and Enterprise Edition (EE), includes …
Read More »Researchers Unveil Massive Quad7 Botnet Targeting Microsoft 365
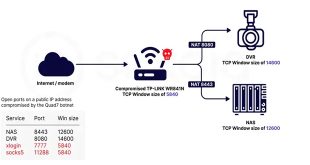
Sekoia.io and Intrinsec analyzed the Quad7 (7777) botnet, which uses TCP port 7777 on infected routers to carry out brute-force attacks on Microsoft 365 accounts. Attacks were detected on 0.11% of monitored accounts. Key insights highlighted by researchers: Botnet Evolution: Quad7 has been active for a long time and continues …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind