The LockBit 3.0 ransomware group on Monday leaked 600 gigabytes of critical data stolen from Indian lender Fullerton India, two weeks after the group demanded a $3 million ransom from the company.
Fullerton India said on April 24 that it had suffered a malware attack that forced it to temporarily operate offline as a precaution. The company said it had resumed customer services and worked with global cybersecurity experts to make its security environment more resilient.
By infosecbulletin
/ Saturday , July 27 2024
Google fixed a bug in Chrome's Password Manager that caused user credentials to vanish temporarily. A problem with Google Chrome's...
Read More
By infosecbulletin
/ Saturday , July 27 2024
India’s Communications Minister Chandra Sekhar Pemmasani confirmed a breach at the state-owned telecom operator BSNL on May 20 during a...
Read More
By infosecbulletin
/ Saturday , July 27 2024
Malware based threats increased by 30% in the first half of 2024 compared to the same period in 2023, according...
Read More
By infosecbulletin
/ Friday , July 26 2024
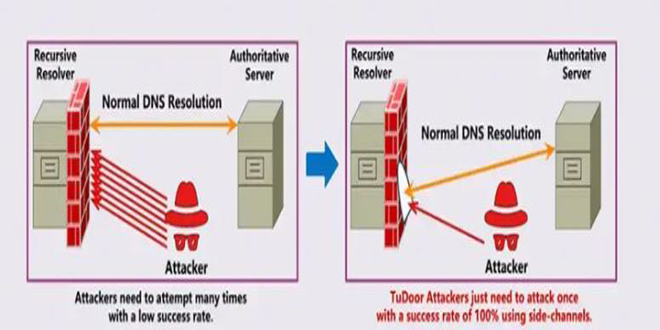
A new critical vulnerability in the Domain Name System (DNS) has been found. This vulnerability allows a specialized attack called...
Read More
By infosecbulletin
/ Friday , July 26 2024
A serious vulnerability, CVE-2023-45249 (CVSS 9.8), has been found in Acronis Cyber Infrastructure (ACI), a widely used software-defined infrastructure solution...
Read More
By infosecbulletin
/ Friday , July 26 2024
OpenAI is testing a new search engine "SearchGPT" using generative artificial intelligence to challenge Google's dominance in the online search...
Read More
By infosecbulletin
/ Thursday , July 25 2024
CISA released two advisories about security issues for Industrial Control Systems (ICS) on July 25, 2024. These advisories offer important...
Read More
By infosecbulletin
/ Thursday , July 25 2024
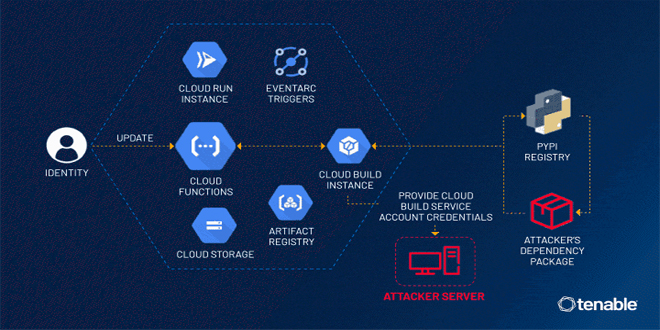
Tenable security researchers found a vulnerability in Google Cloud Platform's Cloud Functions service that could allow an attacker to access...
Read More
By infosecbulletin
/ Thursday , July 25 2024
BDG e-GOV CIRT's Cyber Threat Intelligence Unit has noticed a concerning increase in cyber-attacks against web applications and database servers...
Read More
By infosecbulletin
/ Thursday , July 25 2024
GitLab released a security update today to fix six vulnerabilities in its software. Although none of the flaws are critical,...
Read More
The ransomware group soon listed Fullerton India as a victim on its data leak site, stating it had stolen more than 600 gigabytes of “loan agreements with individuals and legal companies.”
The group set a deadline of April 29 for the company to pay the ransom to keep the group from publishing the stolen data. The group also gave the company the option to pay $1,000 to extend the deadline by 24 hours.
Fullerton India operates 699 branches across India that offer doorstep credit services to around 2.1 million customers. The company in 2022 had more than $2.5 billion worth of assets under management and employed over 13,000 people.
Ritesh Bhatia, noted cybercrime researcher and the founder of V4WEB Cybersecurity, shared evidence with Information Security Media Group about the LockBit group releasing documents related to Fullerton India on the dark web. He said the data leak occurred as a result of Fullerton India refusing to engage with the ransomware group, leading to the group initiating triple-extortion tactics to force the company to pay.
While double extortion involves ransomware actors encrypting a victim’s data and exfiltrating it to place additional pressure on the victim to pay, a triple-extortion tactic involves hackers contacting the victim’s clients, business partners, vendors and customers to make the breach public and force the victim to come to the negotiating table.
(Source: bank info security)
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind