The US cybersecurity agency, CISA, added a flaw in NextGen Healthcare’s Mirth Connect product to its catalog of Known Exploited Vulnerabilities (KEV).
A vulnerability in the open source product, known as CVE-2023-43208, allows remote code execution without authentication due to a data deserialization problem. A patch was rolled out with the release of version 4.4.1.
By infosecbulletin
/ Saturday , July 27 2024
Google fixed a bug in Chrome's Password Manager that caused user credentials to vanish temporarily. A problem with Google Chrome's...
Read More
By infosecbulletin
/ Saturday , July 27 2024
India’s Communications Minister Chandra Sekhar Pemmasani confirmed a breach at the state-owned telecom operator BSNL on May 20 during a...
Read More
By infosecbulletin
/ Saturday , July 27 2024
Malware based threats increased by 30% in the first half of 2024 compared to the same period in 2023, according...
Read More
By infosecbulletin
/ Friday , July 26 2024
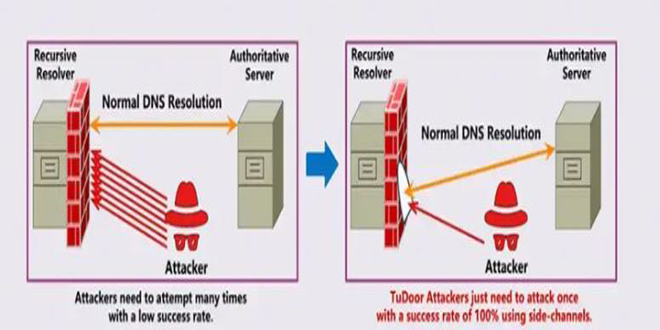
A new critical vulnerability in the Domain Name System (DNS) has been found. This vulnerability allows a specialized attack called...
Read More
By infosecbulletin
/ Friday , July 26 2024
A serious vulnerability, CVE-2023-45249 (CVSS 9.8), has been found in Acronis Cyber Infrastructure (ACI), a widely used software-defined infrastructure solution...
Read More
By infosecbulletin
/ Friday , July 26 2024
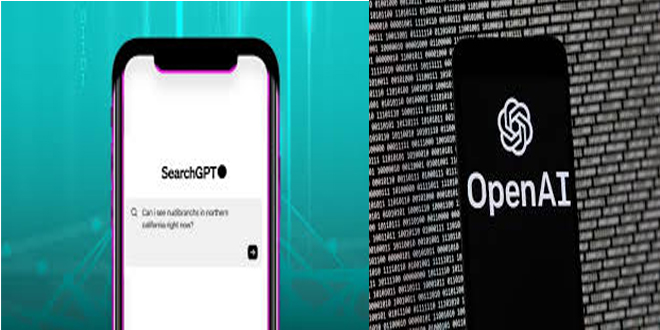
OpenAI is testing a new search engine "SearchGPT" using generative artificial intelligence to challenge Google's dominance in the online search...
Read More
By infosecbulletin
/ Thursday , July 25 2024
CISA released two advisories about security issues for Industrial Control Systems (ICS) on July 25, 2024. These advisories offer important...
Read More
By infosecbulletin
/ Thursday , July 25 2024
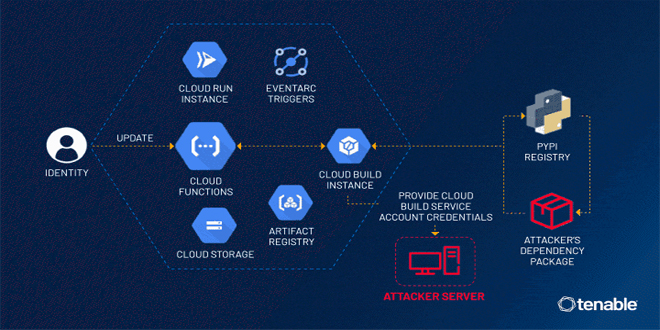
Tenable security researchers found a vulnerability in Google Cloud Platform's Cloud Functions service that could allow an attacker to access...
Read More
By infosecbulletin
/ Thursday , July 25 2024
BDG e-GOV CIRT's Cyber Threat Intelligence Unit has noticed a concerning increase in cyber-attacks against web applications and database servers...
Read More
By infosecbulletin
/ Thursday , July 25 2024
GitLab released a security update today to fix six vulnerabilities in its software. Although none of the flaws are critical,...
Read More
In October 2023, cybersecurity company Horizon3.ai alerted healthcare companies about a flaw called CVE-2023-43208. It is a variation of another flaw called CVE-2023-37679, which was fixed in Mirth Connect version 4.4.0.
Horizon3.ai described the vulnerability as easily exploitable and warned that attackers would likely exploit it to gain access or compromise sensitive healthcare data.
The security firm identified over 1,200 cases of NextGen Mirth Connect exposed on the internet.
Horizon3.ai released technical details and proof-of-concept (PoC) code in mid-January 2024. Shortly after, The Shadowserver Foundation found over 440 internet-exposed instances affected by CVE-2023-43208.
CISA added CVE-2023-43208 to its catalog and told government agencies to fix it by June 10.
The agency has not provided any information about the attacks. Microsoft mentioned the exploitation of CVE-2023-37679 and CVE-2023-43208 in a brief report in April.
Microsoft reported that Mirth Connect and other vulnerabilities were exploited by a China-based threat actor known as Storm-1175, who has used Medusa ransomware.
CISA may know about other attacks, but their KEV catalog does not mention ransomware exploitation. The CVE-2023-37679 flaw has not been added to the catalog yet.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind