CERT-In, India’s cyber security watchdog, has discovered several vulnerabilities in the widely-used Google Chrome operating system. These vulnerabilities have the ability to bypass security measures on the targeted system.
According to a CERT-In advisory, attackers can exploit vulnerabilities to run unauthorized code, cause a denial of service, and bypass security on targeted systems.
By infosecbulletin
/ Wednesday , September 10 2025
Sophos fixed an authentication bypass vulnerability in its AP6 Series Wireless Access Points, preventing attackers from obtaining admin privileges. The...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Security researcher Jeremiah Fowler discovered a database containing sensitive information from gym customers and staff, including names, financial details, and...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Microsoft patched September 2025 Patch Tuesday 81 flaws, including two publicly disclosed zero-day vulnerabilities. This Patch Tuesday addresses nine critical...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
Elastic reported a security incident caused by a breach at Salesloft Drift, leading to unauthorized access to an internal email...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
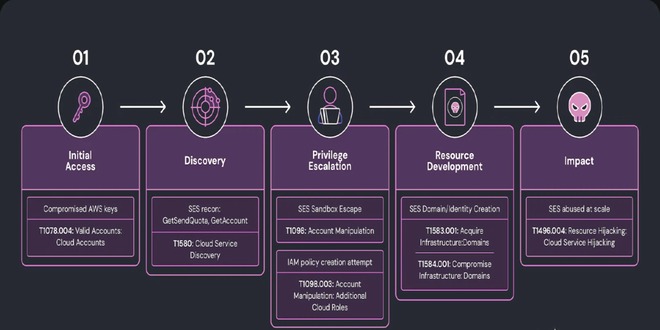
Researchers at Wiz discovered a complex phishing campaign using Amazon's Simple Email Service (SES) for large-scale attacks, showing how hacked...
Read More
By infosecbulletin
/ Monday , September 8 2025
The global ransomware landscape continues to shift in 2025, with SafePay rapidly emerging as one of the most active and...
Read More
By infosecbulletin
/ Sunday , September 7 2025
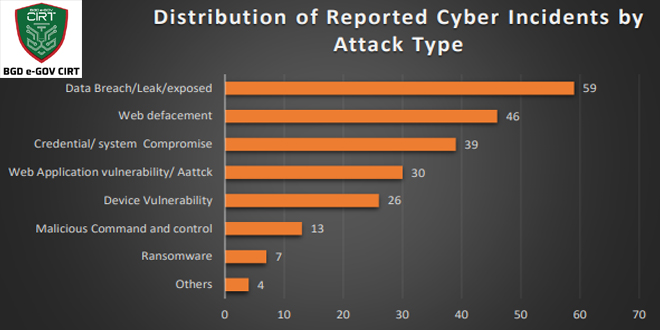
Bangladesh Cyber Threat Landscape 2024, by BGD e-GOV CIRT, reveals a sharp escalation in cyber threats across Bangladesh. The year...
Read More
By infosecbulletin
/ Sunday , September 7 2025
Investigations into the Nx "s1ngularity" NPM supply chain attack have unveiled a massive fallout, with thousands of account tokens and...
Read More
By infosecbulletin
/ Saturday , September 6 2025
ISC2 has launched a Threat Handling Foundations Certificate to assist cybersecurity experts in enhancing Digital Forensics and Incident Response (DFIR)...
Read More
By infosecbulletin
/ Thursday , September 4 2025
Jeremiah Fowler, a cybersecurity researcher, found an unprotected server revealing 378 GB of Navy Federal Credit Union files, including operational...
Read More
ALSO READ:
Microsoft November 2023 Patch fixes 5 zero-days, 58 flaws
“These vulnerabilities exist in Google Chrome OS due to use after free in profiles, inappropriate implementation in downloads, heap buffer overflow in pdf and issue in Linux Kernel. An attacker could exploit these vulnerabilities by persuading a victim to visit a specially-crafted request on the targeted system.”
CERT-In regularly identifies vulnerabilities in devices and operating systems and publicly warns users and companies about them.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind