Zyxel released patches for 15 security issues affecting network-attached storage (NAS), firewall, and access point (AP) devices. The fixes address critical flaws that could allow authentication bypass and command injection.
The three vulnerabilities are listed below :
By infosecbulletin
/ Wednesday , June 4 2025
IBM has issued a security advisory for vulnerabilities in its QRadar Suite Software and Cloud Pak for Security platforms. These...
Read More
By infosecbulletin
/ Wednesday , June 4 2025
As Bangladesh prepares for the extended Eid-ul-Adha holidays, the BGD e-GOV Computer Incident Response Team (CIRT) has issued an urgent...
Read More
By infosecbulletin
/ Tuesday , June 3 2025
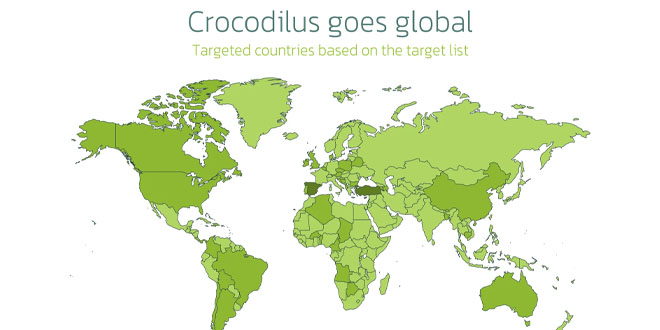
In March 2025, the Threatfabric mobile Threat Intelligence team identified Crocodilus, a new Android banking Trojan designed for device takeover....
Read More
By infosecbulletin
/ Tuesday , June 3 2025
Qualcomm has issued security patches for three zero-day vulnerabilities in the Adreno GPU driver, affecting many chipsets that are being...
Read More
By infosecbulletin
/ Monday , June 2 2025
Roundcube Webmail has fixed a critical security flaw that could enable remote code execution after authentication. Disclosed by security researcher...
Read More
By infosecbulletin
/ Sunday , June 1 2025
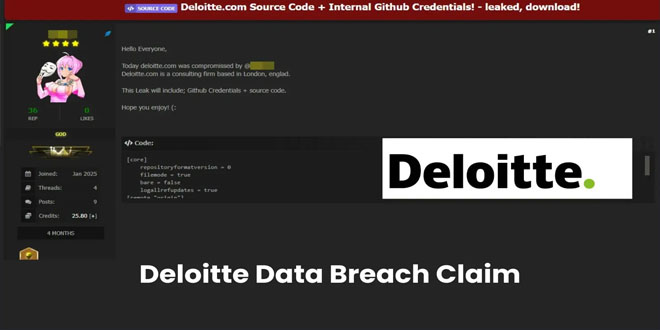
A hacker known as "303" claim to breach the company's systems and leaked sensitive internal data on a dark web...
Read More
By infosecbulletin
/ Sunday , June 1 2025
CISA and ACSC issued new guidance this week on how to procure, implement, and maintain SIEM and SOAR platforms. SIEM...
Read More
By infosecbulletin
/ Saturday , May 31 2025
The Qualys Threat Research Unit (TRU) found two local information-disclosure vulnerabilities in Apport and systemd-coredump. Both issues are race-condition vulnerabilities....
Read More
By infosecbulletin
/ Saturday , May 31 2025
New ransomware payment reporting rules take effect in Australia yesterday (May 30) for all organisations with an annual turnover of...
Read More
By infosecbulletin
/ Saturday , May 31 2025
Global makers of surveillance gear have clashed with Indian regulators in recent weeks over contentious new security rules that require...
Read More
CVE-2023-35138 (CVSS score: 9.8):
There is a vulnerability that allows an attacker to execute operating system commands using an HTTP POST request, even without authentication.
CVE-2023-4473 (CVSS score: 9.8):
A vulnerability in the web server allows an attacker to execute commands on a device by sending a specific URL.
CVE-2023-4474 (CVSS score: 9.8):
An unauthenticated attacker could execute OS commands by sending a manipulated URL to a vulnerable device.
Zyxel has fixed three high-severity flaws (CVE-2023-35137, CVE-2023-37927, and CVE-2023-37928). These flaws could be used by attackers to gather system information and run commands. It is important to mention that both CVE-2023-37927 and CVE-2023-37928 require authentication.
The flaws impact the following models and versions :
NAS326 – versions V5.21(AAZF.14)C0 and earlier (Patched in V5.21(AAZF.15)C0)
NAS542 – versions V5.21(ABAG.11)C0 and earlier (Patched in V5.21(ABAG.12)C0)
The advisory warns about nine flaws found in firewall and access point versions sold by Taiwanese networking vendor. Some of these flaws could allow unauthorized access to system files and administrator logs, or cause a denial-of-service condition.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind