The FBI has issued a warning stating that even after being patched against a critical flaw, Barracuda Networks Email Security Gateway (ESG) appliances are still vulnerable to potential compromise by suspected Chinese hacking groups.
It said that the fixes were not effective and that it still sees intrusions and considers all affected Barracuda ESG devices to be compromised and vulnerable to this attack.
By infosecbulletin
/ Wednesday , June 18 2025
Russian cybersecurity experts discovered the first local data theft attacks using a modified version of legitimate near field communication (NFC)...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
Cybersecurity researcher Jeremiah Fowler discovered an unsecured database with 170,360 records belonging to a real estate company. It contained personal...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
GreyNoise found attempts to exploit CVE-2023-28771, a vulnerability in Zyxel's IKE affecting UDP port 500. The attack centers around CVE-2023-28771,...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included two high-risk vulnerabilities in its Known Exploited Vulnerabilities (KEV)...
Read More
By infosecbulletin
/ Monday , June 16 2025
SafetyDetectives’ Cybersecurity Team discovered a public post on a clear web forum in which a threat actor claimed to have...
Read More
By infosecbulletin
/ Sunday , June 15 2025
WestJet, Canada's second-largest airline, is looking into a cyberattack that has affected some internal systems during its response to the...
Read More
By infosecbulletin
/ Saturday , June 14 2025
Resecurity found 7.4 million records of Paraguayan citizens' personal information leaked on the dark web today. Last week, cybercriminals attempted...
Read More
By infosecbulletin
/ Friday , June 13 2025
HashiCorp has revealed a critical vulnerability in its Nomad tool that may let attackers gain higher privileges by misusing the...
Read More
By infosecbulletin
/ Friday , June 13 2025
SoftBank has disclosed that personal information of more than 137,000 mobile subscribers—covering names, addresses, and phone numbers—might have been leaked...
Read More
By infosecbulletin
/ Friday , June 13 2025
Serious security vulnerabilities in Trend Micro Apex One could allow attackers to inject malicious code and elevate their privileges within...
Read More
ALSO READ:
WinRAR zero-day exploited since April to hack trading accounts
CVE-2023-2868 is a zero-day bug that was tracked with a CVSS score of 9.8. It was discovered to have been weaponized in October 2022, more than seven months before it was fixed. Mandiant, owned by Google, is diligently monitoring the China-nexus activity cluster known as UNC4841.
With the presence of a remote command injection vulnerability in versions 5.1.3.001 through 9.2.0.006, unauthorized individuals can gain administrator privileges and execute system commands on the ESG product.
The observed attacks have shown that a successful breach serves as a gateway to unleash numerous malware strains, including SALTWATER, SEASIDE, SEASPY, SANDBAR, SEASPRAY, SKIPJACK, WHIRLPOOL, and SUBMARINE (also known as DEPTHCHARGE). These strains enable the execution of any commands and effectively evade defense mechanisms.
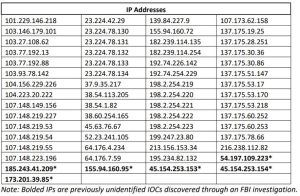
The FBI stated that cyber actors used a vulnerability to add harmful payloads to the ESG appliance. These payloads had various capabilities like persistent access, email scanning, credential harvesting, and data exfiltration.
The threat intelligence company has identified UNC4841 as an aggressive and highly skilled group, showcasing a remarkable ability to adapt their custom tools and employ advanced tactics to maintain control over high-value targets with remarkable persistence.
The federal agency strongly advises customers to immediately isolate and replace all affected ESG devices. It is also crucial to conduct thorough network scans to identify any suspicious outgoing traffic.

 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














