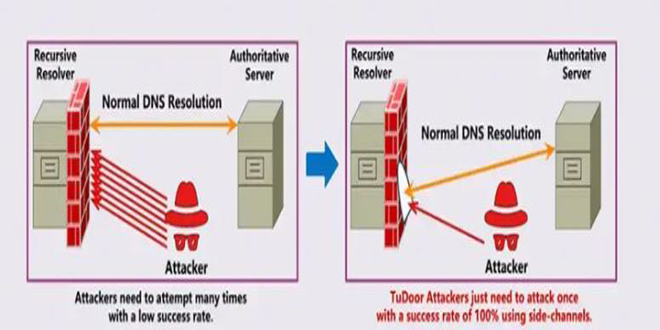
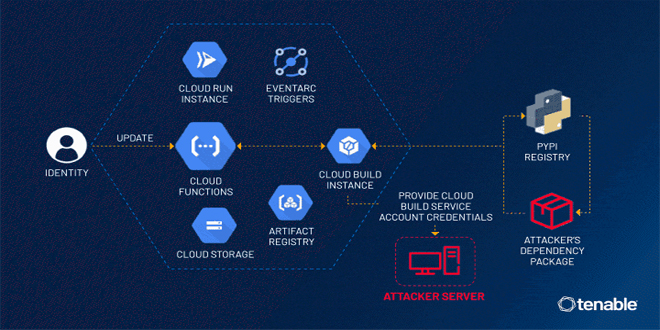
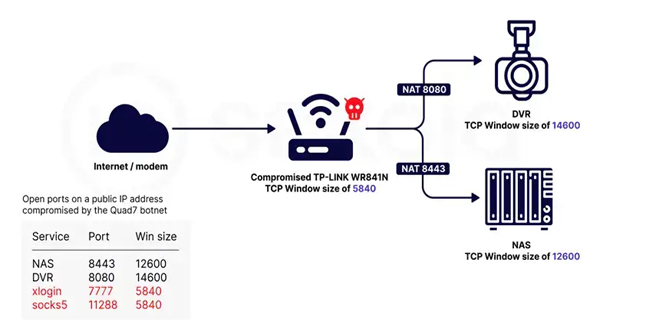
As companies began moving their computing operations and data storage to the cloud, the security of these digital assets has been a priority. Implementing a robust cloud security strategy is paramount for every organization. SaaS providers, in particular, carry a vast amount of sensitive data. This scenario represents a sizable risk to a company’s privacy and intellectual assets, so when you start building a cloud security strategy, you must ask—and be able to answer—these five vital questions from the outset.
Q #1: What requirements must our SaaS organization comply with from legal, client, or end-user perspectives?
Depending on the type of industry or end-user you are serving, both legal and client standards should be an area of focus when it comes to their respective compliance and data privacy requirements.
SOC 2
Systems and Organizational Controls 2 (SOC 2), although voluntary, is an important differentiator for any SaaS vendor or company managing the data of other organizations. Developed by the American Institute of CPAs (AICPA), it’s a service standard that specifies how organizations should manage customer data.
The standard is based on five Trust Services criteria: security, privacy, availability, processing integrity, and confidentiality. Compliance gives your clients the reassurance that your company takes its job of managing their data seriously enough to have proven its competence over a prescribed period. For a security-conscious business considering a SaaS provider, SOC 2 compliance is a minimum requirement.
ISO 27001
This is a global certification for companies looking to implement an information security management system. It goes beyond the SOC 2 information security function to include an operational security management system. International clients might want your company to have ISO 27001 certification, e. The good news is if you are complying with SOC 2, you might be already halfway there.
Legal Requirements
From the legal viewpoint, you’ll need to implement the privacy regulations that apply to your target market. FedRAMP, GDPR/CCPA, and HIPAA all serve specific industries. For example, if your company sells products or services in the EU, you’ll need General Data Protection Regulation (GDPR) compliance, which is an essential element in EU data privacy laws.
For U.S. companies operating in any area of healthcare, HIPAA compliance is a stringent privacy requirement, although you don’t get a certificate to show it. Organizations serving the U.S. government must achieve FedRAMP compliance, and if you process sensitive data of California residents, you’ll need to comply with the California Consumer Privacy Act or CCPA. This is a law aimed at enhancing privacy rights and consumer protection for residents of that state.
Industry-Specific Regulations
Various other industries have their own legal demands, such as the payment card industry’s Data Security Standard (PCI-DSS). This standard, usually referred to as PCI, is a series of security requirements for programs that process and store credit card payment information.
#2: How much budget have we allocated to cybersecurity for our clients?
It’s important to be mindful of the costs associated with building secure software. Cybersecurity costs money and it’s not cheap to implement the needed range of security controls. This being said, your SaaS organization needs to carefully consider how to allocate the various costs involved in keeping your clients’ information secure. You’ll need to get pricing on implementing layered security as most SaaS vendors need at least three different security layers to protect their customer data from external threats. These are basic infrastructure layers consisting of cloud data storage platforms, hosting companies, and internal servers.
You’ll need to:
- Install robust data encryption software
- Deploy virus and malware protection programs at every level of access
- Provide training for your team and customers on how to handle data securely
- Backup your customer data and store the backups in multiple locations and formats
- Consult a third-party cybersecurity firm to conduct regular testing of your systems
- Pay for external party auditors
Every company that contributes to the SaaS product you offer will need at least the same level of security and compliance all the way down the chain. Since the chain starts with your company, you must budget for the expense of ensuring your security is watertight.
Q #3: Do we have enough human resources to handle security and compliance needs?
We’re all waiting for the day artificial intelligence can handle everything, but that’s still a fair way off. Right now, your SaaS organization will still need to have enough human resources to carry out critical security functions. These include:
- Implementing security controls on devices. Administrators must install data encryption programs, configure firewalls and antivirus protection, and monitor intrusion detection systems. According to Verizon’s 2022 Data Breaches Investigations Report, 82%of all data breaches involve a human element, so implementing robust security controls reduces the risk of such incidents.
- Managing vulnerabilities. These controls include risk assessments to determine the probability and impact of threats and vulnerability assessments to uncover weaknesses and identify additional measures to reduce the danger posed by these vulnerabilities. Diagnostic tools and artificial intelligence can assist with much of this, but human resources are still needed to make final decisions and implement the processes.
- Running background checks on your employees. In many cases, employees can deliberately expose information—for example, by misconfiguring databases or allowing cyber criminals to access the organization’s systems. Without running background checks, companies leave themselves vulnerable to employing bad actors.
- Onboarding and offboarding of employees. Follow best practices for onboarding and offboarding employees to prevent increasing your cybersecurity risks. New employees should be trained in cybersecurity adapted to their entry level, understanding, and experience, and given only essential access initially. Exiting employees should undergo exit interviews, and the cybersecurity team should establish an offboarding program. This program should include revoking all login access immediately the worker leaves, informing all colleagues and shareholders of the departure and monitoring the systems the employee had access to for a period of time after they leave.
Having enough people for a powerful cloud security strategy doesn’t mean you must appoint high-cost, permanent employees. Managed information security services can extend your operation by providing the support you need around the clock, and at fractions of the price of a full-time security professional.
Q #4: What are some security best practices to adopt in our organization?
Some organizations choose to be very flexible with security and only do the bare minimum needed to comply with the different frameworks. More security-conscious organizations often go above and beyond and implement advanced security controls.
For example, I once worked with a client who forced all employees to register their phones and computers in MDM before they could access any company resources. This wasn’t a compliance requirement but a choice the organization made to improve its security posture.
Basic best practice options every business should adopt include:
- Conduct regular risk assessments across all systems. Things change. Software gets updated, bad actors find new ways to target organizations, and the value of your data to hackers becomes more valuable and easier to access. Companies should assess their risk levels annually at least, if not more often, and when they make any significant systems or business changes that could leave them vulnerable. These include migrating to the cloud or appointing a new supplier with access to the systems.
- Implement measures to reduce risk. Once you know what factors threaten your SaaS organization, you can implement reasonable security controls to mitigate these risks. Train your staff in security awareness. Apply penalties for violation of security rules. Screen new hires and provision user rights to allow access to essential services only.
- Apply password controls and virus protections. Develop comprehensive password policies and enforce the use of multi-factor authentication. Make sure your firewall is correctly configured, and encrypt your data using a VPN. Install tough virus and malware protection and securely dispose of old and discarded equipment.
- Inventory all data, equipment, and processes. Protecting your data depends on knowing what you have and where it is. Many data breaches involve leads of confidential information that was inadvertently stored in email, on lost laptops, or backup tapes. Identify and catalog all your customer and employee records, store payment information separately and securely, and ensure all your equipment protections are up to date and working well.
- Build cybersecurity into your operational processes. IT systems can be vulnerable if they aren’t properly maintained. Harden your network by removing or changing default credentials (e.g., passwords such as 1234567 and user names like “admin” or “info”). Apply critical security patches promptly and monitor systems for deviations from expected norms.
Establish ways and means to detect and respond to incidents and develop sound business continuity and disaster recovery plans. Make certain third-party providers are also secure by conducting an audit of their security measures or building standards into their contracts with you.
Q #5: Did we conduct a penetration test against our application?
Most security vulnerabilities are not identified until an external party conducts a penetration test. A penetration test is one of the best ways to identify any significant security issues with an application. Penetration tests go a step further than a risk assessment by attempting to exploit the weaknesses identified.
For example, a vulnerability assessment might discover patches are not being updated regularly, leaving a company vulnerable to attacks. A penetration test would attempt to access the company systems through unpatched vulnerabilities, enabling the cybersecurity team to shore up any potential risk areas in advance.
Being Prepared
Any company building a cloud security strategy must comply with the requirements of their industry but it is just as important to go beyond required compliance by being prepared ahead of time for any possible cybersecurity incidents. Put processes in place to detect anomalies and attempted breaches. Exercise reasonable security measures to anticipate problems. Make sure you have adequate backup and restoration procedures. If you are unsure about moving forward, get expert help to secure your systems and protect your customers and staff.
By Metin Kortak, chief information security officer, Rhymetec
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind