According to Nozomi Networks, cyber threats related to malware in operational technology (OT) and Internet of Things (IoT) environments have increased tenfold in the first six months of 2023 compared to the previous six months. The latest Nozomi Networks Labs OT & IoT Security Report was compiled by the security …
Read More »TimeLine Layout
August, 2023
-
3 August
“Mysterious team Bangladesh”, Group IB-report-hacktivists
A hacker group named ‘Mysterious Team Bangladesh’ has been accused of defacing 78 websites with 750 DDoS attacks worldwide since June last year. A Singapore-based cyber security firm called ‘Group-IB’ has termed the hacker group as ‘hacktivists’. Hacktivists are those who attack computer systems mainly for political reasons without any …
Read More » -
3 August
Bank Asia Managing Director resigned
Managing Director (MD) of Bank Asia Arif Billah Adil Chowdhury has resigned due to personal reasons not debt irregularities. He submitted his resignation late last week. The company accepted his resignation and granted him leave till October 21. At the same time, additional MD Shafiuzzaman has been given the current …
Read More » -
1 August
Ransomware delivery Via URLs: Reports Unit 42
Threat actors are resorting to employing URLs to send ransomware, as they constantly search for innovative methods to deceive victims and bypass their defenses. They are employing more and more sophisticated tactics to distribute their ransomware is making their actions more dynamic. Threat actors often use different versions of ransomware …
Read More » -
1 August
Bangladesh Bank server outage, RTGS transaction disrupted
Transactions in Bangladesh Bank’s Real Time Gross Settlement (RTGS) system have been disrupted due to a server error. It caused problems in the settlement of inter-bank transactions after 4 pm on Monday (July 31). A senior official of a private bank said that there is a problem with RTGS. As …
Read More » -
1 August
Daily Cybersecurity update, July 31, 2023
01 The University of Guelph, Canada, is notifying students of a data breach involving personal information accessed through a third-party security company. The breach exposed student IDs, names, and dates of birth. 02 The BAZAN Group, Israel’s largest oil refinery operator, experienced a cyberattack, resulting in the inaccessibility of its …
Read More »
July, 2023
-
31 July
The name of Islami Bank has changed
In accordance with the provisions of Section 11(a) of the Companies Act, 1994, Bangladesh Bank has named ‘Islami Bank Bangladesh Limited’ as ‘Islami Bank Bangladesh PLC.’ has been changed. On Monday (July 31), the Banking Regulations and Policy Department of Bangladesh Bank issued a circular in this regard. The circular …
Read More » -
31 July
Original BreachForums Breached, users PII Data sold Online
The stolen database from the compromised website, BreachForums, has resurfaced, and its remnants are now available for purchase under the name “breached_db_person.” The public has been granted access to extremely sensitive information, including the US No Fly List, FBI’s InfraGard, DC Health Link with Members of Congress data, and much …
Read More » -
31 July
“Digital Bank” application time extended
A new web portal has been opened to accept the applications of those interested in launching a completely technology-based new type of bank ‘Digital Bank’. Application period is 42 days. But even within 40 days not a single organization applied. But many people have opened the user ID. MFS companies …
Read More » -
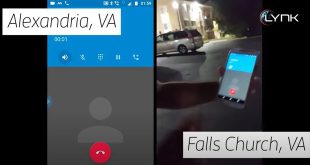
28 July
First-Ever Two-Way Phone Voice Calls by Satellite (Video)
Lynk Global, Inc. has made a groundbreaking achievement by releasing the world’s first-ever video of two-way voice calls between standard mobile phones connected via satellite. The video showcases a multitude of voice calls made using conventional mobile phones, which are connected through Lynk’s satellite-cell-towers already in orbit. Charles Miller, CEO …
Read More »
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind