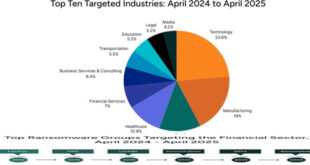
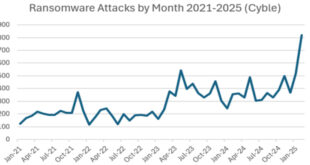
Ransomware attacks increased in several important sectors in February 2024 despite a slow start to the year. In February, ransomware gangs increased the number of victims posted on their extortion sites. There were 310 victims, compared to 242 in the previous month and 229 in February 2023.
By infosecbulletin
/ Wednesday , June 18 2025
Russian cybersecurity experts discovered the first local data theft attacks using a modified version of legitimate near field communication (NFC)...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
Cybersecurity researcher Jeremiah Fowler discovered an unsecured database with 170,360 records belonging to a real estate company. It contained personal...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
GreyNoise found attempts to exploit CVE-2023-28771, a vulnerability in Zyxel's IKE affecting UDP port 500. The attack centers around CVE-2023-28771,...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included two high-risk vulnerabilities in its Known Exploited Vulnerabilities (KEV)...
Read More
By infosecbulletin
/ Monday , June 16 2025
SafetyDetectives’ Cybersecurity Team discovered a public post on a clear web forum in which a threat actor claimed to have...
Read More
By infosecbulletin
/ Sunday , June 15 2025
WestJet, Canada's second-largest airline, is looking into a cyberattack that has affected some internal systems during its response to the...
Read More
By infosecbulletin
/ Saturday , June 14 2025
Resecurity found 7.4 million records of Paraguayan citizens' personal information leaked on the dark web today. Last week, cybercriminals attempted...
Read More
By infosecbulletin
/ Friday , June 13 2025
HashiCorp has revealed a critical vulnerability in its Nomad tool that may let attackers gain higher privileges by misusing the...
Read More
By infosecbulletin
/ Friday , June 13 2025
SoftBank has disclosed that personal information of more than 137,000 mobile subscribers—covering names, addresses, and phone numbers—might have been leaked...
Read More
By infosecbulletin
/ Friday , June 13 2025
Serious security vulnerabilities in Trend Micro Apex One could allow attackers to inject malicious code and elevate their privileges within...
Read More
In February, attacks on healthcare providers and state/local governments increased, based on data collected by Recorded Future from various sources including extortion sites, government agencies, news reports, and hacking forums.

A hack targeted Change Healthcare, causing disruptions for pharmacies and hospitals. The BlackCat/Alphv group is responsible and has attempted an exit scam. Law enforcement tried to stop the cybercrime gang in December.
“I think one of the big things we saw in February was the re-emergence of ALPHV after the takedown. Their numbers were way down, compared to before [the takedown], but they were trying to make a comeback,” said Allan Liska, a Recorded Future ransomware expert who helps track and analyze the data.
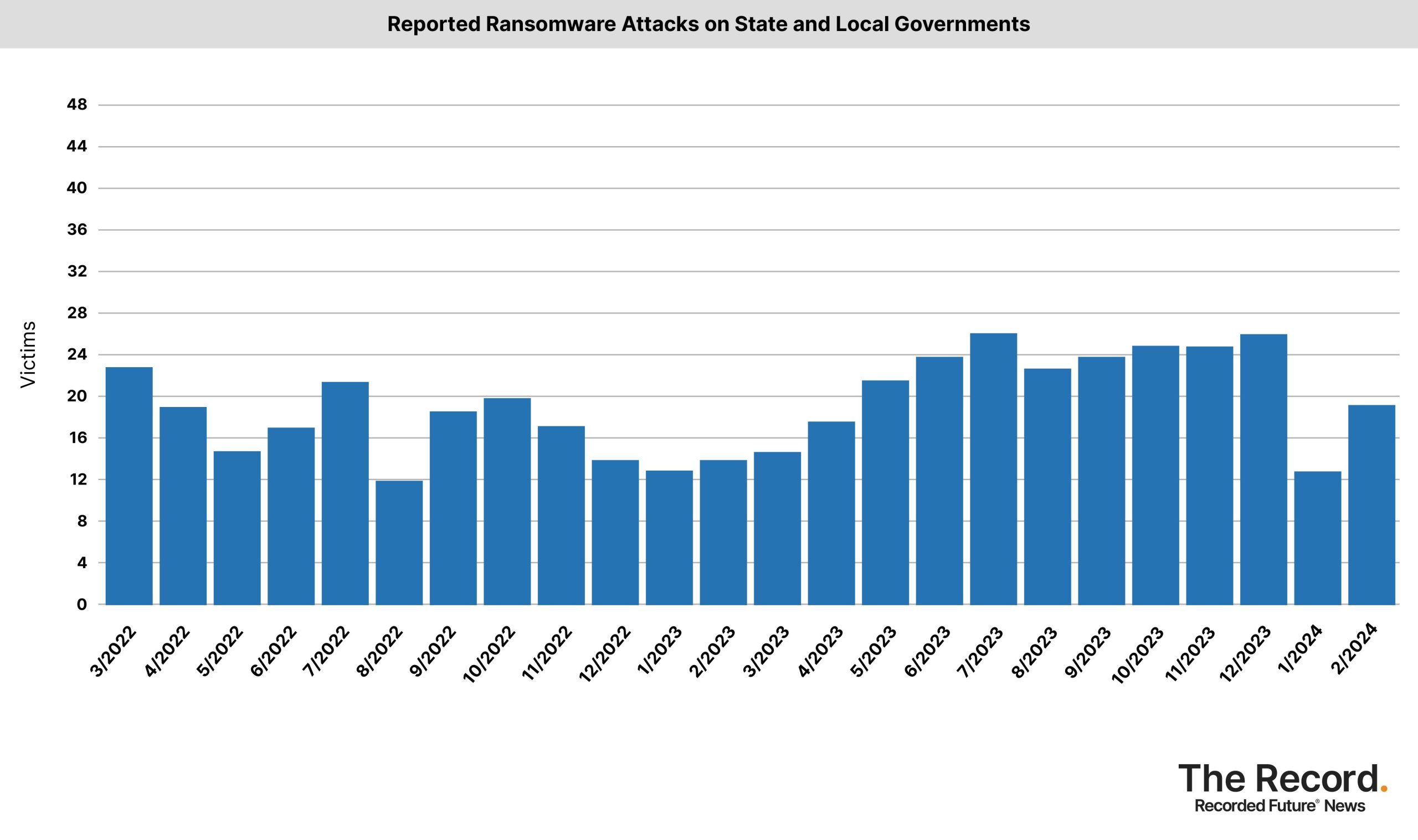
“I think we’re staring to see that takedowns, especially large ones, do have a temporary dampening effect, but ransomware remains resilient. After the LockBit takedown and the ALPHV implosion, the next few months will be interesting to watch,” Lisa added.
In August, the FBI stopped the Qakbot ransomware gang and eliminated the ransomware from infected devices.
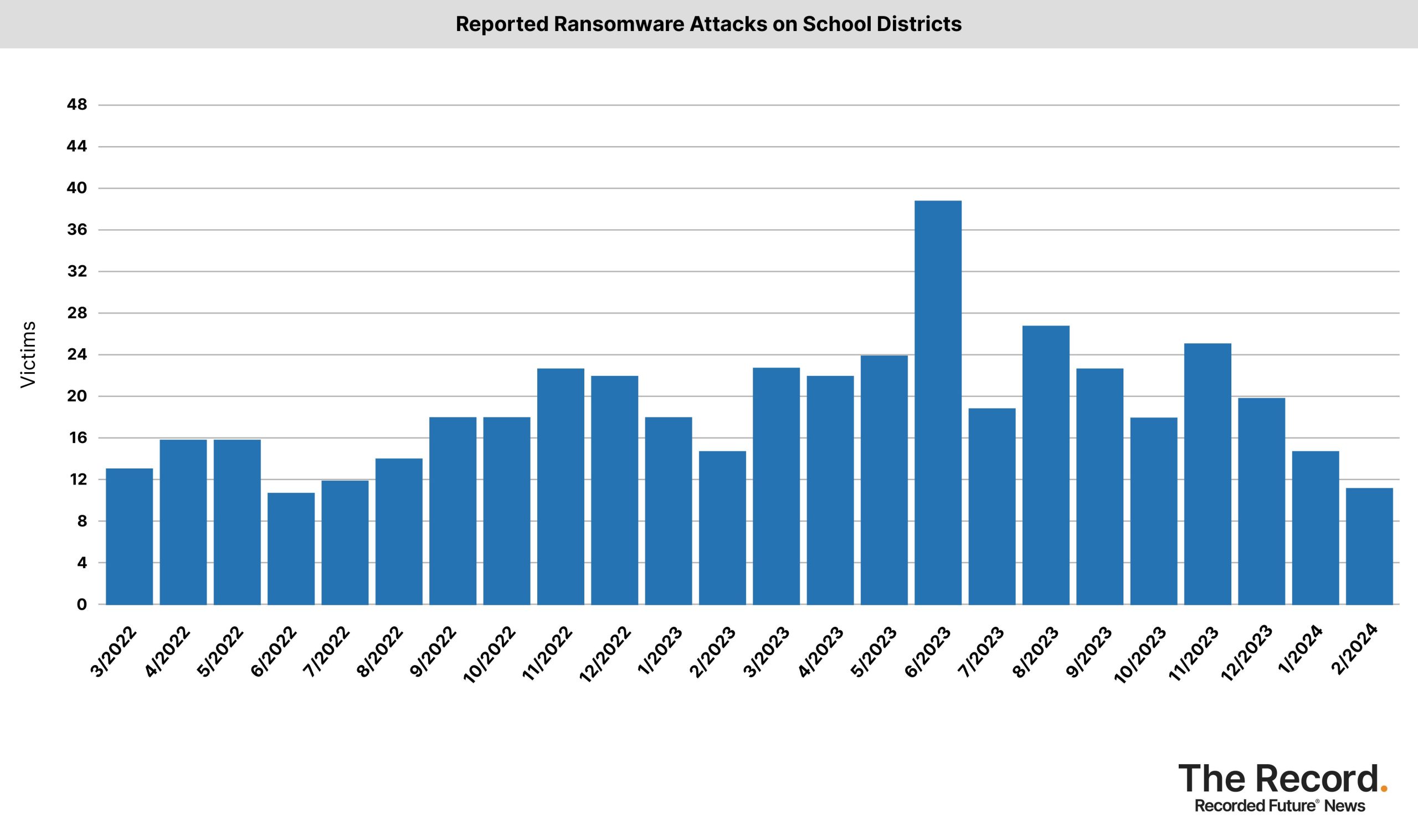
In late 2023, law enforcement shut down the Ragnar Locker ransomware site in an international operation. At the same time, Ukrainian hackers claimed to have wiped the servers of the Trigona ransomware gang, which was allegedly linked to Russia.
Source: Record Future




 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind