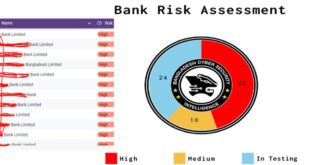
With a festive look and the participation of more than one hundred participants from Bangladesh …
Read More »CISA Adds Second BeyondTrust Flaw to KEV On Active Attacks
U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a second security flaw affecting BeyondTrust’s Privileged Remote Access (PRA) and Remote Support (RS) products to its Known Exploited Vulnerabilities (KEV) catalog, noting that it is actively being exploited. CVE-2024-12686 is a medium-severity vulnerability (CVSS score: 6.6) that could let an attacker …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind