Sygnia’s recent report highlights the changing strategies of ransomware groups targeting VMware ESXi appliances. These attackers exploit vital virtual infrastructure to disrupt operations and remain hidden in compromised networks.
ESXi appliances have become prime targets due to their role in hosting vital virtual machines. “Damaging them renders virtual machines inaccessible, severely disrupting the business operations of affected organizations,” notes Sygnia.
By F2
/ Thursday , July 3 2025
The final day of the Cyber Defence & Security Exhibition and Conference (CYDES) 2025 concluded with high-impact engagements at the...
Read More
By F2
/ Thursday , July 3 2025
Cisco warns that a vulnerability in Cisco Unified Communications Manager (Unified CM) and Cisco Unified Communications Manager Session Management Edition...
Read More
By F2
/ Wednesday , July 2 2025
The second day of the Cyber Defence & Security Exhibition and Conference (CYDES) 2025 further cemented Malaysia’s position as a...
Read More
By F2
/ Tuesday , July 1 2025
Malaysia's Deputy Prime Minister Datuk Seri Dr. Ahmad Zahid Hamidi said that Malaysia has placed cybersecurity at the heart of...
Read More
By F2
/ Tuesday , July 1 2025
Mark Chen, the chief research officer at OpenAI, sent a forceful memo to staff on Saturday, promising to go head-to-head...
Read More
By F2
/ Tuesday , July 1 2025
The Canadian government ordered Hikvision to stop all operations in the country due to national security concerns. Hikvision, based in...
Read More
By infosecbulletin
/ Sunday , June 29 2025
Doctors at Columbia University Fertility Center have reported what they are calling the first pregnancy using a new AI system,...
Read More
By infosecbulletin
/ Saturday , June 28 2025
Cybersecurity experts and federal authorities are warning that the Scattered Spider hackers are now targeting aviation and transportation, indicating a...
Read More
By F2
/ Saturday , June 28 2025
Since June 9, 2025, Russian users connecting to Cloudflare services have faced throttling by ISPs. As the throttling is being...
Read More
By infosecbulletin
/ Saturday , June 28 2025
A new report from SafetyDetectives reveals that hackers posted a massive 3.1GB dataset online, containing about 61 million records reportedly...
Read More
Ransomware operators use ESXi devices to secretly tunnel malicious traffic within networks, often avoiding detection because of minimal monitoring.
The report highlights SSH tunneling as a tactic where attackers create a semi-persistent backdoor by using stolen admin credentials or vulnerabilities to access ESXi devices.
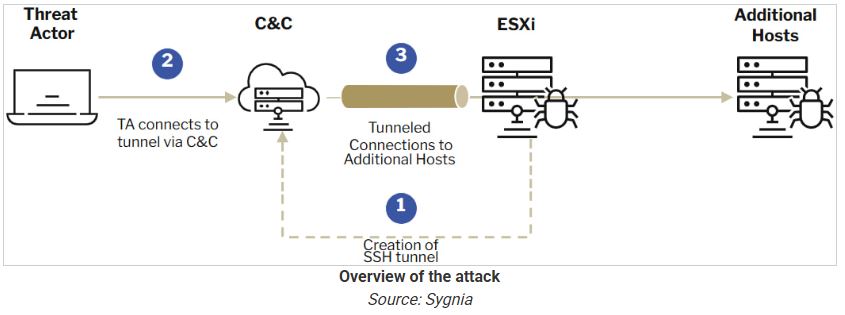
Threat actors use SSH to create a remote port-forwarding SOCKS tunnel, allowing them to mix malicious traffic with legitimate activity.
Sygnia explains, “Since ESXi appliances are resilient and rarely shutdown unexpectedly, this tunneling serves as a semi-persistent backdoor within the network.”
This method lets attackers avoid security measures and keep access for a long time.
ESXi’s logging structure complicates forensic investigations. Unlike traditional syslogs, ESXi organizes logs by activity, spreading critical events across multiple files, such as /var/log/shell.log, /var/log/auth.log, and /var/log/hostd.log. Sygnia emphasizes, “Configuring syslog forwarding from the ESXi server to an external syslog server can solve the issue.”
The report shows how Abyss Locker ransomware exploits ESXi appliances. Attackers exploited ESXi devices and NAS for network access, highlighting the importance of strong monitoring and defense strategies.

 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














