With a festive look and the participation of more than one hundred participants from Bangladesh …
Read More »Hackers Abuses Cloudflare Tunnels to Deliver malware
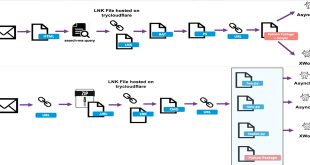
Proofpoint is monitoring a group of cybercriminals using Cloudflare Tunnels to distribute malware. They are exploiting the TryCloudflare feature to create one-time tunnels without needing an account. Tunnels allow remote access to data and resources not on the local network, similar to using a virtual private network (VPN) or secure …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind