Hidden Investigations is a cybersecurity-driven team committed to advancing digital security through research, innovation, and hands-on impact, bridging the gap between offensive security and real-world defense. Originally recognized for our success in Capture The Flag (CTF) competitions, the team is now expanding its efforts to develop open-source tools, conduct in-depth vulnerability research, and simulate real-world threats.

The team’s mission is to uncover hidden security risks, tackle complex cybersecurity challenges, and promote a safer digital environment. Founded by Sakibul Ali Khan, Hidden Investigations is driven by curiosity, excellence, and a commitment to shaping the future of cybersecurity.
Infosecbulletin talks to Sakibul Ali Khan regarding his activities, and here go the details of the interview for the readers.
Q1. What’s the behind-the-scenes of starting Team “Hidden Investigations”?
Since school, I’ve always been passionate about technology. During the later years of high school, I discovered the field of hacking and became extremely curious about it. When I entered college (11th grade), I started participating in Capture The Flag (CTF) competitions on my own.
After about a year, I saw that CTFs were also being held in Bangladesh and internationally with team-based formats. That’s when I realized I needed a team to compete more effectively. So, at the beginning of 2022, I founded Hidden Investigations.
Q2. What does “Hidden Investigations” mean? What does it represent?
Naming was a challenge. I’m into Red Teaming, where the focus is on ethically identifying vulnerabilities while staying under the radar. The mission is to inform companies of their security weaknesses before they can be exploited. That’s why I picked the name “Hidden Investigations.” “Hidden” conveys the stealthy nature of the work, while “Investigations” indicates the search for vulnerabilities.
Q3. What areas of cybersecurity does the team focus on most?
We are known for our success in Capture The Flag (CTF) competitions, but our efforts now go further. We are developing open-source tools, researching vulnerabilities, and simulating attacks to understand new threats.
Q4. Mention some achievements your team is proud of?
We achieved significant milestones, ranking 2nd in the BCS ICT Fest CTF, 5th in UAP Cyber Siege 2025, and 7th in the Phoenix Summit 2025.
One of our members won the individual Red Sentry CTF championship internationally. We also placed 3rd in the prize-eligible standings at BlitzCTF 2025, a global event. Our team has been recognized by Bugcrowd and Snyk for our CTF achievements.
Q5. What tools, platforms, or unique methodologies does your team often use or build?
We explore the limits of digital systems through CTFs, exploit research, and adversary simulation. Our work includes building custom exploits, proof-of-concepts (PoCs), and tools for vulnerability detection and lab simulations; some of which are already complete, while others are still in development.
We’ve also developed custom plugins for the CTFd platform to improve the experience of private and community CTFs we organize. These plugins help create a fairer and more engaging environment for participants. Enhancing the CTF experience through such tools is something we plan to continue working on in the future.
Q6. What do you love to share about your team member?
We come from diverse academic and technical backgrounds, but we share the same mindset: always question, always explore, always improve. Currently, we have six active members who regularly participate in CTFs and team activities.
Our expertise includes various cybersecurity fields such as Web and Application Security, Forensics, Reverse Engineering, OSINT, Cryptography, and Network Security. We’ve also completed some private penetration testing projects.
“A special mention goes to Tanzil Dewan Shahed, who helps moderate and coordinate the team.” “Additionally, we have one member from the corporate sector who, while not active in CTFs, provides valuable industry guidance and occasionally supports the team financially,” added Sakibul Ali Khan.
Q7. What values or mindset do you try to build in your team culture?
At our core, we are problem solvers. We thrive in high-pressure scenarios, whether it’s during timed CTF competitions or real-world adversary simulations. Every member brings unique strengths to the table, and collaboration is our greatest tool.
We invest heavily in knowledge sharing, peer learning, and continuous upskilling; not just to grow as individuals, but to help uplift the wider cybersecurity community around us.
Q8. How do you see Hidden Investigations contributing to the wider cybersecurity community in Bangladesh and globally?
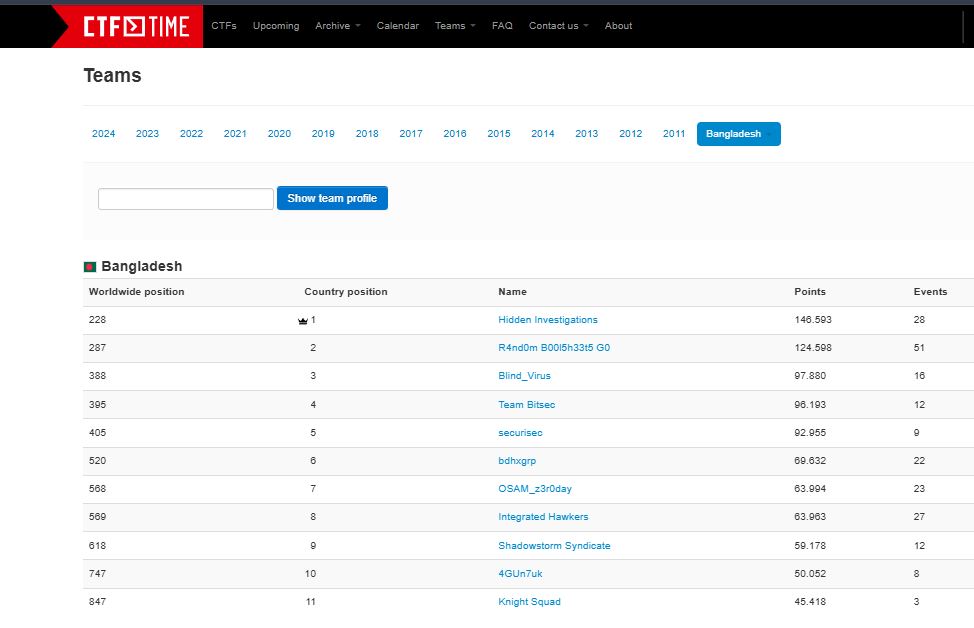
In the Bangladeshi CTF community, we currently hold the No. 1 position on CTFtime among local teams. We are actively representing Bangladesh in international CTF competitions, showcasing local talent on a global stage.
We aim to inspire future cybersecurity enthusiasts in Bangladesh by leading by example and sharing knowledge. Our efforts through performance, open resources, and community involvement help raise awareness about careers in cybersecurity.
Q9. Where do you see Hidden Investigations heading in the next 2–3 years?
We believe that hands-on experience, responsible disclosure, and sharing knowledge are essential for improving cybersecurity. By working together innovatively, we aim to support the global security community and inspire future cybersecurity experts.
In the next 2–3 years, we want to be recognized not just for our CTF achievements but also for our overall contributions. We aim to engage more with local and international communities by organizing public CTF events for global participants.
Additionally, we plan to release open-source projects under the Hidden Investigations name. Our core belief is simple: “Learn together to create a skilled community.”
We think practical exploration, responsible sharing, and knowledge exchange are crucial for boosting cybersecurity. Through collaboration, we strive to support the global security community and motivate upcoming cybersecurity talents.
In the upcoming 2–3 years, we want to gain recognition for both our CTF results and our wider contributions. We’re committed to working closely with local and international communities by hosting public CTF events for participants worldwide.
We also intend to publish open-source projects under the Hidden Investigations label. Our main principle is clear: “Learn together to cultivate a talented community.”
Q10. As the founder, what’s been your most rewarding or challenging moment so far?
In the beginning, one of the hardest parts was finding people with a similar mindset—those who were open to teamwork and eager to grow. I also wanted to build a friendly and supportive environment where we could perform well under pressure in CTF competitions, and teamwork is our biggest strength.
The most rewarding moments for me are when our team gives their best. Winning is great, but what matters most is seeing our members grow, learn, and play with honesty.
As I always remind myself and the team: “We don’t chase trophies; we chase growth. If we grow together, the victories will follow.”
(If you are in CTF/Bug Bounty arena, leading a team or institution, can communication with us for such publication through [email protected])
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind