The Apache Software Foundation has warned about two serious security issues (CVE-2024-38346 and CVE-2024-39864) in Apache CloudStack, a popular open-source cloud computing platform. These vulnerabilities are a big threat to organizations using CloudStack to manage their virtualized infrastructure.
Unauthenticated Cluster Service Port (CVE-2024-38346)
By infosecbulletin
/ Tuesday , October 22 2024
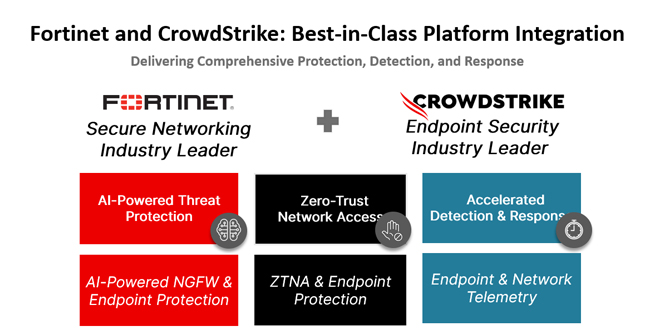
In today's rapidly changing cybersecurity environment, organizations encounter numerous complex threats targeting endpoints and networks. CrowdStrike and Fortinet have partnered...
Read More
By infosecbulletin
/ Tuesday , October 22 2024
Sophos, based in the UK, is to acquire Secureworks, a Nasdaq-listed company, for $859 million in cash from Dell Technologies....
Read More
By infosecbulletin
/ Monday , October 21 2024
The Internet Archive was breached again, this time through their Zendesk email support platform, following warnings that threat actors had...
Read More
By infosecbulletin
/ Sunday , October 20 2024
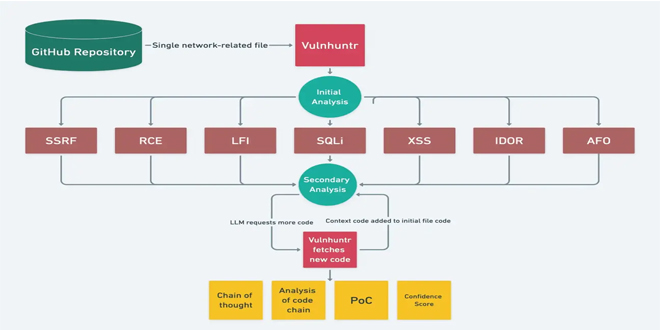
In today's changing cybersecurity environment, it's essential to find vulnerabilities in code. Vulnhuntr, an open-source tool on GitHub, uses Large...
Read More
By infosecbulletin
/ Friday , October 18 2024
Bitdefender said a vulnerability has been identified in Bitdefender Total Security HTTPS scanning functionality where the software fails to properly...
Read More
By infosecbulletin
/ Thursday , October 17 2024
Cybersecurity threats have surged to extraordinary heights, as Microsoft’s latest Digital Defense Report reveals that its customers are confronted with...
Read More
By infosecbulletin
/ Thursday , October 17 2024
VMware has issued a warning about a remote code execution vulnerability, CVE-2024-38814, with a CVSS score of 8.8, in its...
Read More
By infosecbulletin
/ Thursday , October 17 2024
Mandiant researchers found that over 90 zero-day vulnerabilities and more than 40 known vulnerabilities were exploited in the wild. Vulnerabilities...
Read More
By infosecbulletin
/ Wednesday , October 16 2024
Oracle's October 2024 Critical Patch Update has fixed 334 security vulnerabilities in its products. The CPU affects 28 Oracle product...
Read More
By infosecbulletin
/ Wednesday , October 16 2024
Google has released Chrome 130, fixing 17 security vulnerabilities. The update (version 130.0.6723.58/.59 for Windows and Mac, and 130.0.6723.58 for...
Read More
The vulnerability CVE-2024-38346 is found in the unauthenticated CloudStack cluster service port (default 9090). It can be exploited by attackers to run commands on hypervisors and CloudStack management servers. This could lead to full control over the CloudStack environment, causing data breaches, service disruptions, and financial losses.
Dynamic Port Assignment in Disabled Integration API Service (CVE-2024-39864)
The CVE-2024-39864 vulnerability affects the CloudStack integration API service. Although it should not be accessible when disabled, it mistakenly listens on a random port. Attackers who can access the CloudStack management network can find this port and use it to perform unauthorized administrative actions and execute remote code on CloudStack managed hosts. This vulnerability increases the risk of a complete infrastructure compromise.
Affected Versions and Urgent Call for Action
Apache CloudStack versions 4.0.0 to 4.18.2.0 and 4.19.0.0 to 4.19.0.1 have serious security flaws. The best way to fix this is to update to versions 4.18.2.1 or 4.19.0.2, which include patches to address these issues.
For organizations unable to upgrade immediately, the following temporary measures are advised:
Limit network access to the cluster service port (default 9090) on CloudStack management server hosts to only their peer management servers. Also, restrict network access on CloudStack management server hosts to only essential ports.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind