Apache Software Foundation released Apache HTTP Server version 2.4.61 to fix a serious source code disclosure vulnerability (CVE-2024-39884). This flaw could expose sensitive server information to malicious actors.
The CVE-2024-39884 vulnerability is caused by a problem in how old content-type configurations are managed. The “AddType” directive and similar settings, when used in certain situations, may accidentally expose the source code of files meant to be processed, including server-side scripts, configuration files, or other sensitive data.
By infosecbulletin
/ Wednesday , October 23 2024
White hat hackers at the Pwn2Own Ireland 2024 contest by Trend Micro's Zero Day Initiative earned $500,000 on the first...
Read More
By infosecbulletin
/ Tuesday , October 22 2024
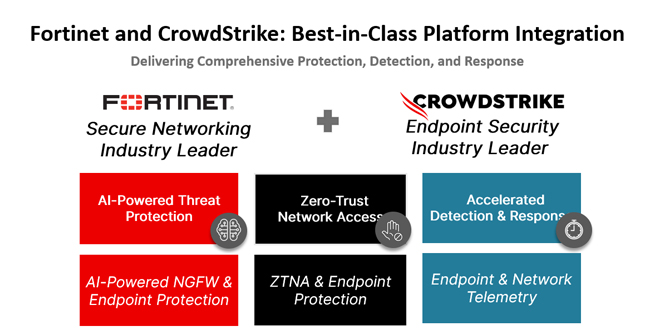
In today's rapidly changing cybersecurity environment, organizations encounter numerous complex threats targeting endpoints and networks. CrowdStrike and Fortinet have partnered...
Read More
By infosecbulletin
/ Tuesday , October 22 2024
Sophos, based in the UK, is to acquire Secureworks, a Nasdaq-listed company, for $859 million in cash from Dell Technologies....
Read More
By infosecbulletin
/ Monday , October 21 2024
The Internet Archive was breached again, this time through their Zendesk email support platform, following warnings that threat actors had...
Read More
By infosecbulletin
/ Sunday , October 20 2024
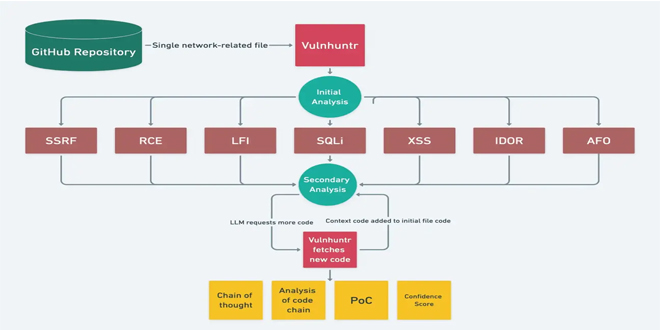
In today's changing cybersecurity environment, it's essential to find vulnerabilities in code. Vulnhuntr, an open-source tool on GitHub, uses Large...
Read More
By infosecbulletin
/ Friday , October 18 2024
Bitdefender said a vulnerability has been identified in Bitdefender Total Security HTTPS scanning functionality where the software fails to properly...
Read More
By infosecbulletin
/ Thursday , October 17 2024
Cybersecurity threats have surged to extraordinary heights, as Microsoft’s latest Digital Defense Report reveals that its customers are confronted with...
Read More
By infosecbulletin
/ Thursday , October 17 2024
VMware has issued a warning about a remote code execution vulnerability, CVE-2024-38814, with a CVSS score of 8.8, in its...
Read More
By infosecbulletin
/ Thursday , October 17 2024
Mandiant researchers found that over 90 zero-day vulnerabilities and more than 40 known vulnerabilities were exploited in the wild. Vulnerabilities...
Read More
By infosecbulletin
/ Wednesday , October 16 2024
Oracle's October 2024 Critical Patch Update has fixed 334 security vulnerabilities in its products. The CPU affects 28 Oracle product...
Read More
While source code disclosure might seem like a technical concern, the implications can be far-reaching. Attackers could exploit this vulnerability to:
Gain a deeper understanding of the server environment: This could lead to more advanced cyberattacks aimed at exploiting specific software versions or configurations.
Identify vulnerabilities in the revealed code: This may result in additional attacks, possibly compromising the entire server or connected systems.
Steal sensitive data: If the code is exposed, it could lead to severe consequences.
The Apache team advises all users to upgrade from version 2.4.60 to 2.4.61. This update fixes a source code disclosure flaw and other vulnerabilities and bugs found in the previous version.
To learn about the vulnerabilities fixed in Apache HTTP Server 2.4.61, visit the official security advisory on the Apache website. Also, enhance your security by using web application firewalls, intrusion detection systems, and regular vulnerability scanning to protect against new threats.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind