In today’s rapidly changing cybersecurity environment, organizations encounter numerous complex threats targeting endpoints and networks. CrowdStrike and Fortinet have partnered to provide top-notch protection from endpoints to firewalls.
This partnership combines the strengths of CrowdStrike in endpoint security and Fortinet in network security, offering customers the flexibility, visibility, and protection needed to prevent breaches.
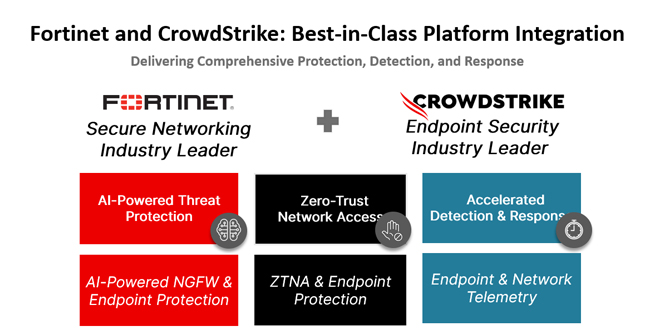
Why CrowdStrike and Fortinet Joined Forces:
Modern cyber threats are complex, requiring a unified security approach. CrowdStrike has transformed endpoint detection and response with its AI-driven Falcon® platform, offering exceptional protection. At the same time, Fortinet leads in network security with its FortiGate next-generation firewalls.
This partnership addresses the increasing need for integrated security platforms. As numerous vendors fill the cybersecurity market, organizations seek reliable partners that provide the flexibility to create lasting defenses. CrowdStrike and Fortinet combine their top-tier capabilities to meet the needs of both small businesses and large enterprises.
Delivering Unified, AI-Powered Protection:
This partnership leverages the advanced capabilities of CrowdStrike Falcon® Insight XDR and Fortinet FortiGate NGFW, offering AI-driven threat protection for both endpoints and networks. Together, they deliver valuable insights into network traffic, user behavior, and endpoint security.
The integration provides customers with clear visibility into their security landscape, eliminating the hassle of using separate tools and disconnected data. Unified logging and threat correlation between endpoint and network data speed up the detection of malicious activities, decrease false positives, and simplify incident response.
Enhancing Zero Trust and Adaptive Security:
In hybrid work environments, remote access to systems has increased security risks. Integrating CrowdStrike Falcon endpoint telemetry with Fortinet’s Zero Trust Network Access (ZTNA) offers adaptive, risk-based protection.
This integration provides secure access to corporate applications by ensuring only trusted devices can reach sensitive resources. It enforces precise access controls and reduces potential attack paths, minimizing the risk of malware and unauthorized access.
A Shared Commitment to the Cybersecurity Ecosystem:
CrowdStrike and Fortinet aim to create an open cybersecurity ecosystem that helps customers build resilient security strategies. Both companies are known for their strong channel ecosystems, and their partnership enhances their ability to provide value. By working together with shared partners, they ensure customers worldwide receive localized support for better security outcomes.
Cyber threats are constantly changing, and organizations must adapt their protection strategies accordingly. The partnership between CrowdStrike and Fortinet is crucial for providing integrated security to prevent breaches.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind