CISA has recently unveiled an invaluable assortment of free tools designed to empower organizations in safeguarding their cloud environments.
CISA’s post mentioned that these tools assist incident response analysts and network defenders in managing, recognizing, and discovering threats, vulnerabilities, and anomalies in cloud or hybrid environments.
By infosecbulletin
/ Tuesday , May 21 2024
Hackers target Bangladeshi many WordPress based e-commerce sites for their illegal activities. Getting access they are now offer to sell...
Read More
By infosecbulletin
/ Monday , May 20 2024
SonicWALL SSL-VPN provides secure remote access to an organization's internal network and resources through an encrypted SSL connection. This kind...
Read More
By infosecbulletin
/ Monday , May 20 2024
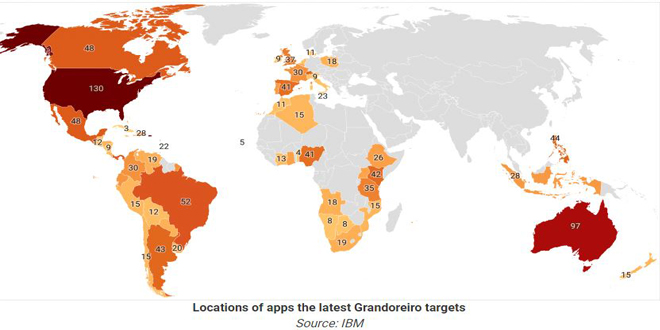
The banking trojan "Grandoreiro" is spreading widely through a phishing campaign in over 60 countries, aiming at customer accounts of...
Read More
By infosecbulletin
/ Saturday , May 18 2024
Australian police are investigating a big data breach in a healthcare company after a ransomware attack on Thursday. The website...
Read More
By infosecbulletin
/ Saturday , May 18 2024
he U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced that two security flaws in D-Link routers have been added to...
Read More
By infosecbulletin
/ Saturday , May 18 2024
The "Antidot" Android Banking Trojan pretends to be a Google Play update app and targets Android users in different regions....
Read More
By infosecbulletin
/ Saturday , May 18 2024
CISA published a guide on using Encrypted Domain Name System (DNS) for federal civilian agencies to improve cybersecurity and meet...
Read More
By infosecbulletin
/ Friday , May 17 2024
Cyble Research and Intelligence Labs found that two cyber threat groups, Transparent Tribe (APT36) and SideCopy, are using advanced strategies...
Read More
By infosecbulletin
/ Friday , May 17 2024
Recorded Future's Insikt Group has discovered a major cyber threat campaign carried out by Russian-speaking hackers, possibly located in the...
Read More
By infosecbulletin
/ Friday , May 17 2024
ISA issued seventeen advisories about Industrial Control Systems (ICS) on May 16, 2024. These advisories give important information about security...
Read More
In the course of an attack, threat actors have traditionally focused their attention on internal servers. Cloud migration is growing quickly, attracting the attention of many cyberattackers who see the cloud as a big and tempting target.
CISA’s tools are invaluable resources for organizations lacking the necessary means to effectively defend against cloud threats. Utilizing these tools is instrumental in safeguarding their cloud resources against the perils of information theft, data theft, and information exposure.
The purpose is to help with identifying and reducing weaknesses and risks that occur when working with cloud-based or hybrid setups.
The highlighted tools enhance the existing tools offered by cloud service improving provider services by strengthening network infrastructures, enhancing security measures, quickly identifying harmful compromises, thoroughly identifying potential threats, and accurately detecting malicious activity after a breach.
CISA stated that cloud service platforms and providers have created security features that help organizations improve security when using cloud environments.
In August 2021, the cybersecurity agency introduced the Joint Cyber Defense Collaborative (JCDC), an innovative partnership designed to protect vital U.S. infrastructure from the ever-present dangers of ransomware and other cyber threats.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind