A critical vulnerability, CVE-2024-540385, has been found in HPE Cray XD670 servers using the AMI BMC Redfish API, allowing remote authentication bypass. Administrators must act quickly to prevent the exploitation. According to HPE’s security bulletin, “This vulnerability could be remotely exploited to allow authentication bypass.” An attacker could gain unauthorized …
Read More »(CVE-2024-540385)
CVE-2025-24813
Apache Tomcat Flaw Exploited In The Wild
CVE-2025-24813, a critical remote code execution vulnerability, is actively exploited, enabling attackers to control vulnerable Apache Tomcat servers with a single PUT API request, reports Wallarm. The exploit, shared by a user on a Chinese forum, takes advantage of Tomcat’s default session persistence and its ability to handle partial PUT …
Read More »
CVE-2025-24016
Critical RCE vulnerability affects Wazuh
Cybersecurity researchers unveil a critical remote code execution vulnerability (CVE-2025-24016) in Wazuh, a popular open-source SIEM platform. The vulnerability has a CVSS score of 9.9 affects Wazuh versions 4.4.0 to 4.9.0, enabling attackers with API access to run arbitrary Python code on the servers. The flaw is due to unsafe …
Read More »Researcher found non protected database form ESHYFT containig 86000 records
Cybersecurity researcher Jeremiah Fowler found and reported a non-password-protected database with over 86,000 records belonging to ESHYFT, a New Jersey-based HealthTech company. ESHYFT operates in 29 states and provides a mobile app platform connecting healthcare facilities with workers like Certified Nursing Assistants (CNAs), Licensed Practical Nurses (LPNs), and Registered Nurses …
Read More »
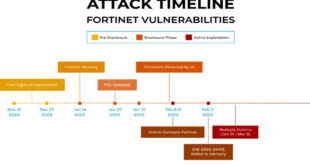
CVE-2024-55591 and CVE-2025-24472
New SuperBlack ransomware exploits Fortinet flaws
Forescout Research- Vedere Labs identified a series of intrusion based on two Fortinet vulnerabilities which began with the exploitation of FortiGate firewall appliance dubbed SuperBlack. Researchers track this between late january and early March. Fortinet disclosed two authentication bypass vulnerabilities: CVE-2024-55591 in January and CVE-2025-24472 in February. When Fortinet first …
Read More »
CVE-2025-25291 & CVE-2025-25292
Attention! GitLab Patched Critical Authentication Bypass Flaws
GitLab has released versions 17.9.2, 17.8.5, and 17.7.7 for its Community and Enterprise Editions to fix security vulnerabilities, including a critical authentication bypass issue. Critical Authentication Bypass Vulnerabilities: Two critical vulnerabilities, CVE-2025-25291 and CVE-2025-25292, are found in the ruby-saml library used by GitLab for SAML single sign-on (SSO) authentication. The …
Read More »
CVE-2025-20138
Cisco released High Security Alert for IOS XR Software
Cisco has issued a security advisory for a high-severity vulnerability in its IOS XR Software, labeled CVE-2025-20138, with a CVSS score of 8.8, which signifies a serious risk. The vulnerability in the Command Line Interface (CLI) of Cisco IOS XR Software allows an authenticated local attacker to execute arbitrary commands …
Read More »NVIDIA has released update for NVIDIA Riva
NVIDIA has released a software update for Riva to fix security vulnerabilities that could allow privilege escalation, data tampering, denial of service, or information disclosure. NVIDIA Riva is a suite of GPU-accelerated microservices for multilingual speech and translation, designed for creating customizable, real-time conversational AI systems. It features automatic speech …
Read More »
CVE-2025-24201
Apple fixes 0-day exploited in “extremely sophisticated attack”
On Tuesday, Apple fixed a critical zero-day vulnerability affecting nearly all supported iPhones and iPads. The company noted that it could have been exploited in a extremely sophisticated attack against targeted individuals using older iOS versions. The vulnerability, identified as CVE-2025-24201, allows attackers to break out of the Web Content …
Read More »Ballista Botnet infects 6000 Unpatched TP-Link Routers
Cato CRTL team said, a new botnet campaign dubbed Ballista target the unpatched TP-Link Archer routers. CVE-2023-1389 is a serious security vulnerability in TP-Link Archer AX-21 routers that could allow command injection and remote code execution. The Hacker news reported, “The botnet exploits a remote code execution (RCE) vulnerability in …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind