On Tuesday (May 14), CISA released four Industrial Control Systems (ICS) advisories which provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-24-135-01 Rockwell Automation FactoryTalk Remote Access ICSA-24-135-02 SUBNET PowerSYSTEM Center ICSA-24-135-03 Johnson Controls Software House C-CURE 9000 ICSA-24-135-04 Mitsubishi Electric Multiple FA Engineering Software Products …
Read More »ALERT
Fortinet report
Attackers exploiting vulnerabilities 50% faster, just 4.76 days
Fortinet reported that in the second half of 2023, the average time form the disclosure of a vulnerability to its active exploitation in the wild decreased to just 4.76 days a 43% reduction compared to the 1st half of the year. Fortinet’s 2H Global landscape report indicate that hackers to …
Read More »Cyber Attack On Data Center Cooling Systems results disruption
According to cybersecurity analysts at Dragos, while cloud adoption offers many benefits for industrial companies , it also poses certain risks. The core operational risks relate to interruptions in data center cooling systems. Data centers use building automation and management systems (BAS/BMS) to control important aspects like temperature. Places like …
Read More »LockBit Ransomware Leader Unmasked and Sanctioned
The UK, US, and Australia have imposed sanctions on the leader of the ransomware group LockBit, which is known worldwide. Russian national Dmitry Khoroshev has been identified as a leader of a group involved in an international law enforcement investigation. The group has extorted over one billion dollars from victims …
Read More »
Outpost24 report
Cybersecurity Loopholes in Paris 2024 Olympics Infrastructure
The 2024 Olympic Games in Paris are coming soon. A recent cybersecurity assessment by Outpost24, a provider of cyber threat exposure management solutions, has raised concerns about the online infrastructure of the games. Outpost24 has identified critical vulnerabilities in the security posture, despite it being considered “mostly secure”. These vulnerabilities …
Read More »LockBit’s seized darknet site resurrected by police, teasing new revelations
New information about the Lockbit ransomware gang might be coming soon. The gang’s old dark web leak site was taken down by law enforcement in February, but it has now reappeared, hinting at the release of new information in a few days. Several parts of the site were updated on …
Read More »GAO: NASA Faces ‘Inconsistent’ Cybersecurity Across Spacecraft
The GAO reviewed NASA’s cybersecurity practices and found that there is a need to update spacecraft acquisition policies and standards. They specifically focused on assessing the cybersecurity requirements in NASA contracts for spacecraft projects. The GAO report reviewed NASA’s spacecraft cybersecurity policies and standards. They looked at three different spacecraft …
Read More »Microsoft Outlook Flaw Exploited by APT28 to compromise Czech, German Entities
Friday (03.05.2024) the ministry of foreign affairs of the Czech republic issued a press release highlighting the cyberattack carried by Russian actor apt28 on Czechia. The press release reads, “Czechia jointly with Germany, the European Union, NATO and international partners strongly condemns activities of the Russian state-controlled actor APT28, who …
Read More »CISA Releases Three Industrial Control Systems Advisories
CISA released three advisories about Industrial Control Systems (ICS) on April 30, 2024. These advisories give current security information, vulnerabilities, and exploits related to ICS. ICSA-24-121-01 Delta Electronics CNCSoft-G2 DOPSoft: Successful exploitation of this vulnerability could allow an attacker to execute arbitrary code. ICSA-24-016-01 SEW-EURODRIVE MOVITOOLS MotionStudio (Update A): Successful …
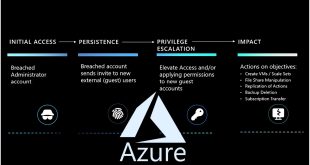
Read More »Azure Logs utilizing to identify threats: Insights From Microsoft
Microsoft security experts recently conducted an exploration on how to effectively use Azure Logs to identify and counteract threat actions. Azure’s defense mechanism relies on effectively understanding and using logs to hunt for threats. Microsoft focuses on integrating best practices for log management, analysis, and incident response to stay proactive …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind