Check Point warned that threat actors are targeting their Remote Access VPN devices in an ongoing campaign to breach enterprise networks. Remote Access is included in all Check Point network firewalls. It can be set up as a client-to-site VPN for accessing corporate networks using VPN clients, or as an …
Read More »New ATM Malware Threatens Banking Security worldwide
There appeared a new type of ATM malware that security experts warn about. It is being advertised in the cybercrime underground and specifically designed to target Europe. A bad actor claimed that the new ATM malware called “EU ATM Malware” has 99% success rate. It can compromise most ATMs in …
Read More »Chronon: a open-source data platform for AI/ML applications
Chronon simplifies data computation and serving for AI/ML apps. Users define data features, and Chronon handles batch and streaming computation, scalable backfills, low-latency serving, correctness, consistency, observability, and monitoring. It allows you to utilize all of the data within your organization, from batch tables, event streams or services to power …
Read More »NSA Releases Guidance on Zero Trust Maturity
The NSA released an information sheet called “Advancing Zero Trust Maturity Throughout the Application and Workload Pillar.” This sheet will help organizations protect their applications from unauthorized users and maintain constant visibility of their workload. This CSI gives recommendations for achieving different levels of application and workload capabilities under the …
Read More »Ivanti Patches Critical RCE Flaws in Endpoint Manager
Ivanti on Tuesday declare to patch for several products, including fixes for critical vulnerabilities in Endpoint Manager (EPM). Ivanti resolved six out of the ten security defects resolved in EPM are critical-severity SQL Injection bugs. Tracked as CVE-2024-29822 through CVE-2024-29827, the bugs impact the Core server of Ivanti EPM 2022 …
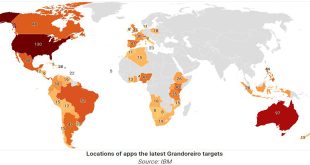
Read More »Banking trojan Grandoreiro targeting about 1,500 banks over 60 countries
The banking trojan “Grandoreiro” is spreading widely through a phishing campaign in over 60 countries, aiming at customer accounts of about 1,500 banks. In January 2024, a joint international law enforcement operation involving Brazil, Spain, Interpol, ESET, and Caixa Bank revealed the disruption of a malware operation. The malware had …
Read More »New “Antidot” Banking Trojan disguised Fake Google Play Updates
The “Antidot” Android Banking Trojan pretends to be a Google Play update app and targets Android users in different regions. It uses VNC and overlay techniques to steal credentials. Cyble Research and Intelligence Labs (CRIL) found that the new Android Banking Trojan, called “Antidot,” pretends to be a Google Play …
Read More »CISA Published Encrypted DNS Implementation Guidance
CISA published a guide on using Encrypted Domain Name System (DNS) for federal civilian agencies to improve cybersecurity and meet OMB Memorandum M-22-09 requirements. Traditionally, the DNS protocol didn’t have ways to make sure requests and responses were confidential, secure, or authentic. However, the M-22-09 guideline requires agencies to encrypt …
Read More »
Cyble Research
Transparent Tribe & SideCopy: A Cyber Alliance Targeting India
Cyble Research and Intelligence Labs found that two cyber threat groups, Transparent Tribe (APT36) and SideCopy, are using advanced strategies to target India, putting both public and private sectors at risk. Cyble Research and Intelligence Labs (CRIL) found that two APT groups, Transparent Tribe (APT36) and SideCopy, are using advanced …
Read More »FBI seized BreachForums, including telegram channel
FBI has seized hacking forum “BreachForums” popularly known as a Breached hacking forum in the underground market on Wednesday morning for the second time in a year, soon after the site was used last week to leak data stolen from a Europol law enforcement portal. Now the site displays a …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind