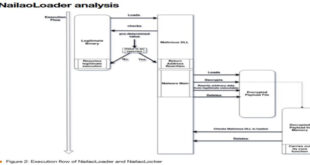
A new cyber campaign called GitVenom poses a serious risk to developers. Security researchers found over 200 fake GitHub repositories that disguise themselves as legitimate projects to distribute information stealers and remote access trojans (RATs). For almost two years, these repositories have exploited developers’ trust in open-source platforms to access …
Read More »Renew Dubai visa within minutes with AI-powered Salama
Residents of Dubai can now easily renew their visas with the new AI-powered digital platform launched by the General Directorate of Residency and Foreigners Affairs (GDRFA) of Dubai. AI powered “Salama” allows residents to renew their visas in minutes and download the updated documents directly, avoiding paperwork and long wait …
Read More »
CVE-2024-20953
CISA Flags Oracle Agile PLM Actively Exploited Security Flaw
CVE-2024-20953 is a vulnerability in Oracle Agile PLM, a product lifecycle management tool. With a CVSS score of 8.8, it allows low-privileged attackers with HTTP network access to exploit systems running version 9.3.6. This could result in complete system takeover, risking sensitive supply chain data and business operations. The vulnerability …
Read More »Stablecoin Bank Hacked – Hackers Stolen $49.5M
Days after the biggest crypto hack ever, another platform has experienced a major exploit. Infini Earn, a decentralized stablecoin bank, lost $49.5 million in USDC, making it one of the year’s biggest security breaches in DeFi. Reportedly a compromised private key led to an attack that stole 11.4 million and …
Read More »
CVE-2025-20029
PoC Exploit Released for F5 BIG-IP Command Injection Vuln
Security researchers have released a proof-of-concept exploit for CVE-2025-20029, a serious command injection vulnerability in F5’s BIG-IP application delivery controllers. The flaw has a CVSS v3.1 score of 8.8 and allows authenticated attackers to execute arbitrary system commands due to improper handling of special elements in the iControl REST API …
Read More »
By 1 April 2025
Australia Bans Kaspersky on its govt systems and devices
On February 21, the Australian Department of Home Affairs issued a directive prohibiting the installation of Kaspersky Lab products and services on all Australian government systems and devices. The directive under the protective security policy framework (PSPF) mandates federal entities to eliminate “all instances” of Kaspersky’s products. Home Affairs secretary …
Read More »CISA Flags Craft CMS Code Injection Flaw Amid Active Attacks
CISA has added a serious security flaw in the Craft content management system (CMS) to its Known Exploited Vulnerabilities catalog due to evidence of active exploitation. The vulnerability CVE-2025-23209 (CVSS score: 8.1) affects Craft CMS versions 4 and 5. It was fixed by the maintainers in late December 2024 with …
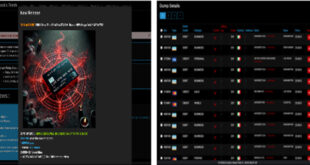
Read More »B1ack’s Stash Releases 1 Million Credit Cards on a Deep Web Forum
On February 19, 2025, the illegal marketplace B1ack’s Stash released over 1 million unique stolen credit and debit card details for free. This approach mirrors the strategy used by BidenCash, where criminals distribute stolen data widely to attract attention to their marketplace. On February 17, a popular deep web forum …
Read More »
Cisco Confirms
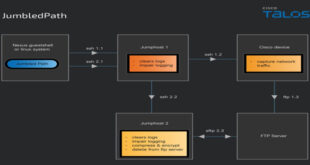
Salt Typhoon Exploited CVE-2018-0171 to Target U.S. Telecom Networks
Cisco Talos reported that Salt Typhoon, also known as FamousSparrow and GhostEmperor, has been spying on U.S. telecommunication providers using a custom tool called JumbledPath. Active since at least 2019, they have targeted government entities and telecom companies. Salt Typhoon is still targeting telecommunications providers worldwide, and according to a …
Read More »
AWS Key Hunter
Test this free automated tool to hunt for exposed AWS secrets
A free tool is now available to scan public GitHub repositories for exposed AWS credentials. Security engineer Anmol Singh Yadav created AWS-Key-Hunter after discovering over 100 exposed AWS access keys, many with high privileges, in public repositories. He described these findings as “just waiting to be exploited” in his blog about …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind