The role of a Chief Information Security Officer (CISO) is crucial in today’s era of smart workplace innovations. They face the challenge of successfully aligning technology, strategic thinking, and foresight to effectively protect enterprise data. Besides gaining unprecedented insights into emerging trends, a security officer needs reliable statistics, practical frameworks, solutions, tactics, and much more.
To create a security roadmap for 2024 that enables the CISO and team to improve their approach, these notes can be useful. Having this ready-made tool available can contribute to improving stakeholder satisfaction, achieving more robust security results, and fostering better alignment between cybersecurity and business goals.
So, here goes the checklist for 2024
Upgraded cloud security strategy:
Over the past year, a staggering number of businesses, exceeding one-third, fell victim to a data breach within their cloud infrastructure. This represents a growth of 35% compared to the figures of 2022. According to cloud security experts, prioritizing zero trust is essential for cloud security in 2024, surpassing even data privacy and compliance. In addition, securing your SaaS ecosystem is key. Current SaaS security strategies and methodologies often aren’t adequate. Sixty-eight percent of organizations are increasing their investments in hiring and training staff on SaaS security. However, there’s much more to be done; more sophisticated threat prevention and defense tools are needed.
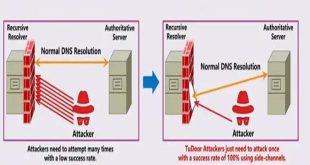
API security:
In the past year, a staggering 94% of security professionals and API developers encountered security issues directly linked to APIs. While 95% of CISOs have a plan to prioritize API security in the next two years, is it possible to expedite progress in API security maturity to more efficiently mitigate threats? To achieve API security maturity, it is imperative to first identify all the APIs being utilized within your organization. Discovering APIs can be done through various means, such as using discovery tools, meticulously examining technical documentation, or engaging in insightful conversations with experienced developers. Evaluate if current tools are capable of fulfilling visibility and compliance requirements. Furthermore, enhance the integration of advanced tools in order to minimize the occurrence of data breaches, data leakage, and shadow API vulnerabilities. Additionally, streamline the tooling process whenever possible.
Post-quantum preparation:
CISA, NIST, and the NSA advise organizations to prepare for post-quantum cryptography. They suggest creating a Quantum Readiness Roadmap, discussing post-quantum roadmaps with technology vendors, taking inventories of cryptographic systems and assets, and making migration plans that prioritize sensitive and essential assets.
AI-driven threat prevention:
Artificial intelligence platforms have the incredible ability to analyze massive amounts of data with a speed that surpasses human capabilities. CISOs and cyber security leaders should prioritize investing in AI-driven security tools. These cutting-edge solutions have the power to greatly enhance the capabilities of organizations in proactively preventing and responding to emerging threats. By doing so, they significantly lower the likelihood of facing cyber breaches. As you further incorporate AI into your organization’s cybersecurity stack, it is important to consider the evolving roles and responsibilities of your security staff. You may want to strategically map out how to redeploy existing talent to maximize resources – cyber and human.
AI red team exercises:
Even though there are no established standards for AI red teaming due to the newness of AI technology, Microsoft has been at the forefront by establishing its own dedicated AI red team back in 2018. Testing AI models at both the base model level and application level is crucial, according to the tech giant. Microsoft explains that both levels of red teaming have their own advantages. For example, red teaming the model helps identify potential misuse, determine the model’s capabilities, and understand its limitations.
Zero trust architecture:
As of September 2022, a striking ninety-seven percent of organizations have either already implemented a zero-trust initiative or have it firmly on their agenda within the next 18 months. What steps can your organization take to enhance the maturity of its zero trust implementation? The Zero Trust Maturity Model provided by CISA is an invaluable framework that serves as a guide for organizations. It outlines four essential pillars that organizations can utilize as benchmarks to measure their maturity stage. Creating new roles like a Zero Trust Program Manager or a Zero Trust Lead Architect can also indicate maturity. The expertise of the staff plays a crucial role in advancing the maturation of ZT.
Citizen developer tools and products:
The concept of Citizen Developers empowers individuals who do not possess coding skills to easily create connected systems and applications. There are certain tools that empower novice users to effortlessly integrate APIs and craft personalized automation solutions, all without the need for any coding expertise. Organizations should prevent these tools from becoming shadow IT by implementing accountability and cybersecurity measures.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind