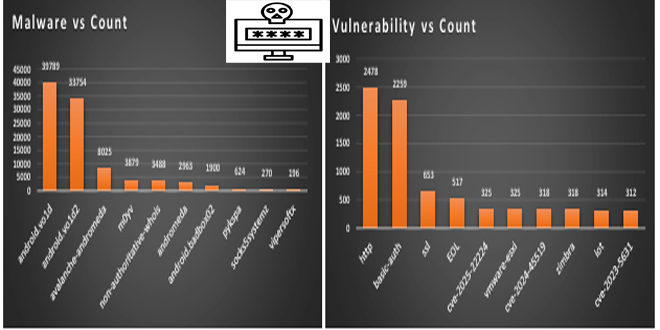
A serious security flaw has been found in the TP-Link Archer C5400X gaming router. It could allow remote code execution on vulnerable devices by sending specific requests.
The vulnerability CVE-2024-5035 has a CVSS score of 10.0 and affects all versions of the router firmware up to 1_1.1.6. It has been fixed in version 1_1.1.7, released on May 24, 2024.
“By successfully exploiting this flaw, remote unauthenticated attackers can gain arbitrary command execution on the device with elevated privileges,” German cybersecurity firm ONEKEY said in a report published Monday.
The problem originates from a binary concerning radio frequency testing called “rftest”. This binary is executed when the system starts up and creates a network listener on TCP ports 8888, 8889, and 8890. This allows an unauthorized attacker to remotely execute code without authentication.
The network service only accepts commands starting with “wl” or “nvram get,” but ONEKEY found that the restriction could be bypassed by injecting a command after shell meta-characters like ; , & , or, | (e.g., “wl;id;”).
TP-Link fixed the vulnerability in version 1.1.7 Build 20240510 by discarding commands with special characters.
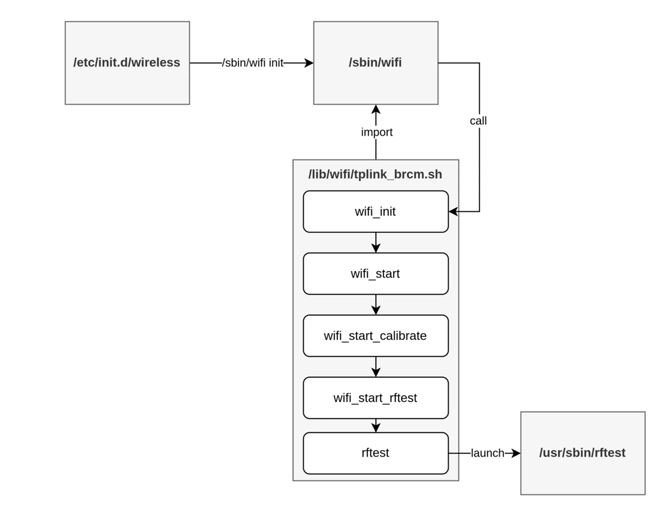
“It seems the need to provide a wireless device configuration API at TP-Link had to be answered either fast or cheap, which ended up with them exposing a supposedly limited shell over the network that clients within the router could use as a way to configure wireless devices,” ONEKEY said.
The open ports used by the ‘rftest’ service on the router’s default configuration impact all users of the device with firmware versions up to 1.1.1.6.
OneKey analysts found a problem and told TP-Link about it on February 16, 2024. TP-Link made a beta patch by April 10, 2024. The security update was released on May 24, 2024, and it fixes the CVE-2024-5035 issue.
The implemented fix was to discard any commands containing shell metacharacters, so these are filtered out in all incoming messages.
Users are recommended to download the firmware update from TP-Link’s official download portal or use their router admin panel to perform the update.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind