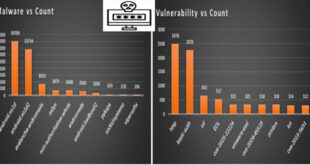
IBM has issued a security advisory for vulnerabilities in its QRadar Suite Software and Cloud Pak for Security platforms. These flaws, which vary in severity from medium to critical, can lead to remote code execution, information disclosure, and denial of service (DoS) attacks. The bulletin lists five security vulnerabilities affecting …
Read More »TimeLine Layout
June, 2025
-
4 June
ALERT
Thousands of IP addresses compromised nationwide: CIRT warnAs Bangladesh prepares for the extended Eid-ul-Adha holidays, the BGD e-GOV Computer Incident Response Team (CIRT) has issued an urgent cybersecurity alert, warning of heightened cyber threats due to reduced monitoring and operational oversight during the festive period. Current Threat Landscape: The CIRT’s Cyber Threat Intelligence Unit has detected widespread …
Read More » -
3 June
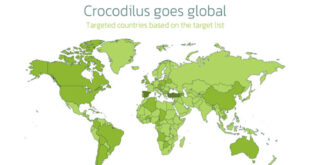
New Android Malware ‘Crocodilus’ Targets Banks in 8 Countries
In March 2025, the Threatfabric mobile Threat Intelligence team identified Crocodilus, a new Android banking Trojan designed for device takeover. Initial samples mostly came from test campaigns, with a few live campaigns observed. Croco-bonus – Get Free Malware! Initial Crocodilus samples indicated operations in Europe, primarily focusing on Turkey. Recently, …
Read More » -
3 June
Qualcomm Patches 3 Zero-Days Used in Targeted Android Attacks
Qualcomm has issued security patches for three zero-day vulnerabilities in the Adreno GPU driver, affecting many chipsets that are being actively exploited in targeted attacks. The company reported two major flaws (CVE-2025-21479 and CVE-2025-21480) identified by the Google Android Security team in late January, and a third serious vulnerability (CVE-2025-27038) …
Read More » -
2 June
Critical RCE Flaw Patched in Roundcube Webmail
Roundcube Webmail has fixed a critical security flaw that could enable remote code execution after authentication. Disclosed by security researcher firs0v, the issue has been addressed in the latest updates for the 1.6 and 1.5 LTS versions. The security update addresses a post-authentication RCE vulnerability caused by PHP object deserialization. …
Read More » -
1 June
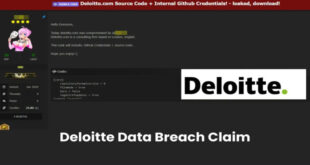
Hacker claim Leak of Deloitte Source Code & GitHub Credentials
A hacker known as “303” claim to breach the company’s systems and leaked sensitive internal data on a dark web forum. The reported breach involves GitHub credentials and source code from Deloitte’s U.S. consulting division’s internal project repositories. Medium reports, “On May 30, 2025, Deloitte, a leading global consulting firm, …
Read More » -
1 June
CISA Issued Guidance for SIEM and SOAR Implementation
CISA and ACSC issued new guidance this week on how to procure, implement, and maintain SIEM and SOAR platforms. SIEM and SOAR help organizations analyze data from firewalls, endpoints, and applications to improve detection and response to cybersecurity incidents. However, many face implementation challenges due to high costs and ongoing …
Read More »
May, 2025
-
31 May
Linux flaws enable password hash theft via core dumps in Ubuntu, RHEL, Fedora
The Qualys Threat Research Unit (TRU) found two local information-disclosure vulnerabilities in Apport and systemd-coredump. Both issues are race-condition vulnerabilities. CVE-2025-5054 affects Ubuntu’s core-dump handler, Apport, while CVE-2025-4598 targets systemd-coredump, the default core-dump handler on Red Hat Enterprise Linux 9 and 10, as well as Fedora. These vulnerabilities allow a …
Read More » -
31 May
Australia enacts mandatory ransomware payment reporting
New ransomware payment reporting rules take effect in Australia yesterday (May 30) for all organisations with an annual turnover of AUS $3 million ($1.93 million). Australia’s Cyber Security Act 2024 applies to private companies managing critical infrastructure assets. Organizations must report any ransomware payments to the Australian Signals Directorate (ASD) …
Read More » -
31 May
Why Govt Demands Foreign CCTV Firms to Submit Source Code?
Global makers of surveillance gear have clashed with Indian regulators in recent weeks over contentious new security rules that require manufacturers of CCTV cameras to submit hardware, software and source code for assessment in government labs, official documents and company emails show. The security-testing policy has sparked industry warnings of …
Read More »
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind