Bitdefender fixed a serious vulnerability (CVE-2024-4177, CVSS 8.1) in its GravityZone Console On-Premise product. This flaw, found by security researcher Nicolas Verdier (n1nj4sec), could enable attackers to carry out server-side request forgery (SSRF) attacks, possibly resulting in unauthorized access and data breaches.
GravityZone Console is a security management platform by Bitdefender. It helps monitor and manage security across different endpoints, networks, and cloud environments. The vulnerability affects on-premise versions of GravityZone Console before version 6.38.1-2.
By infosecbulletin
/ Saturday , July 27 2024
Malware based threats increased by 30% in the first half of 2024 compared to the same period in 2023, according...
Read More
By infosecbulletin
/ Friday , July 26 2024
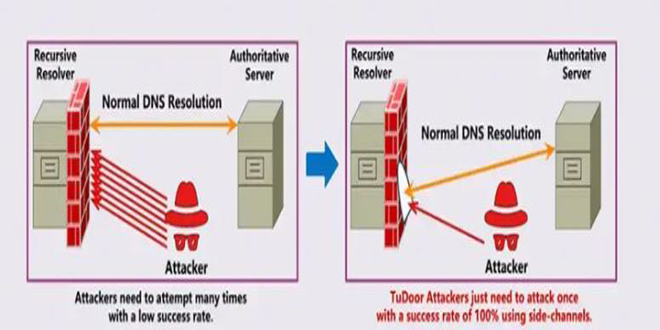
A new critical vulnerability in the Domain Name System (DNS) has been found. This vulnerability allows a specialized attack called...
Read More
By infosecbulletin
/ Friday , July 26 2024
A serious vulnerability, CVE-2023-45249 (CVSS 9.8), has been found in Acronis Cyber Infrastructure (ACI), a widely used software-defined infrastructure solution...
Read More
By infosecbulletin
/ Friday , July 26 2024
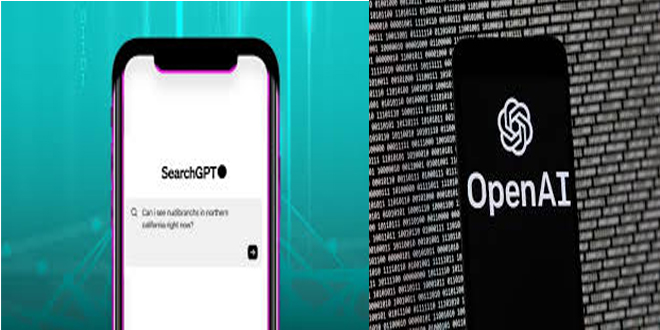
OpenAI is testing a new search engine "SearchGPT" using generative artificial intelligence to challenge Google's dominance in the online search...
Read More
By infosecbulletin
/ Thursday , July 25 2024
CISA released two advisories about security issues for Industrial Control Systems (ICS) on July 25, 2024. These advisories offer important...
Read More
By infosecbulletin
/ Thursday , July 25 2024
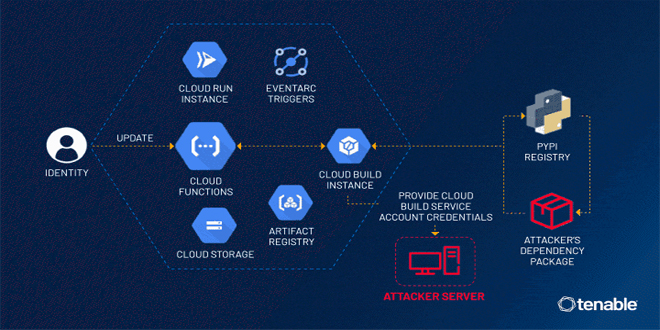
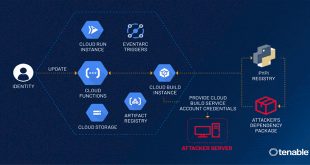
Tenable security researchers found a vulnerability in Google Cloud Platform's Cloud Functions service that could allow an attacker to access...
Read More
By infosecbulletin
/ Thursday , July 25 2024
BDG e-GOV CIRT's Cyber Threat Intelligence Unit has noticed a concerning increase in cyber-attacks against web applications and database servers...
Read More
By infosecbulletin
/ Thursday , July 25 2024
GitLab released a security update today to fix six vulnerabilities in its software. Although none of the flaws are critical,...
Read More
By infosecbulletin
/ Thursday , July 25 2024
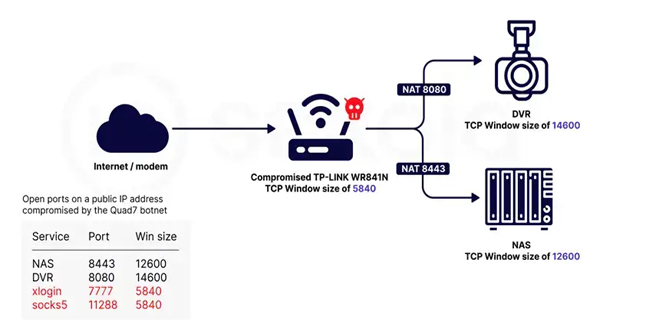
Sekoia.io and Intrinsec analyzed the Quad7 (7777) botnet, which uses TCP port 7777 on infected routers to carry out brute-force...
Read More
By infosecbulletin
/ Wednesday , July 24 2024
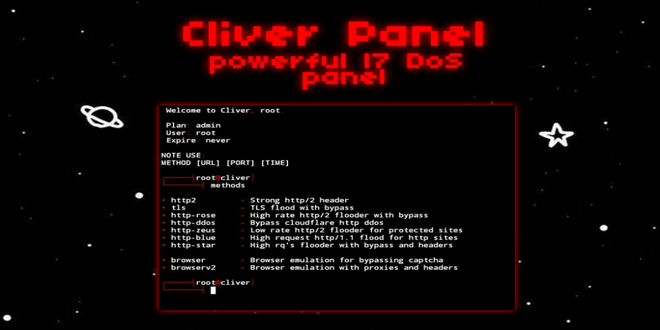
A threat actor has announced a new DDoS tool called Cliver, which offers strong attack methods for disrupting web services,...
Read More
The problem is a flaw in the host whitelist parser of the proxy service. An attacker could exploit this flaw to manipulate server requests, causing unintended actions or leaking sensitive information. These vulnerabilities are very dangerous as they can bypass security controls and allow unauthorized access to internal systems.
Bitdefender has fixed the issue with an automatic update to version 6.38.1-2 of the GravityZone Console On-Premise. Users with affected versions should update to avoid potential risks from this vulnerability.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind