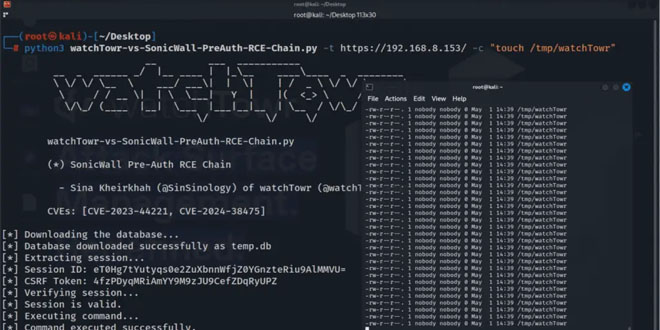
A new exploit chain for SonicWall’s Secure Mobile Access (SMA) appliances has been released by watchTowr Labs. It details how two vulnerabilities, CVE-2023-44221 and CVE-2024-38475, can be combined to allow remote, unauthenticated attackers to hijack admin sessions and run arbitrary code.
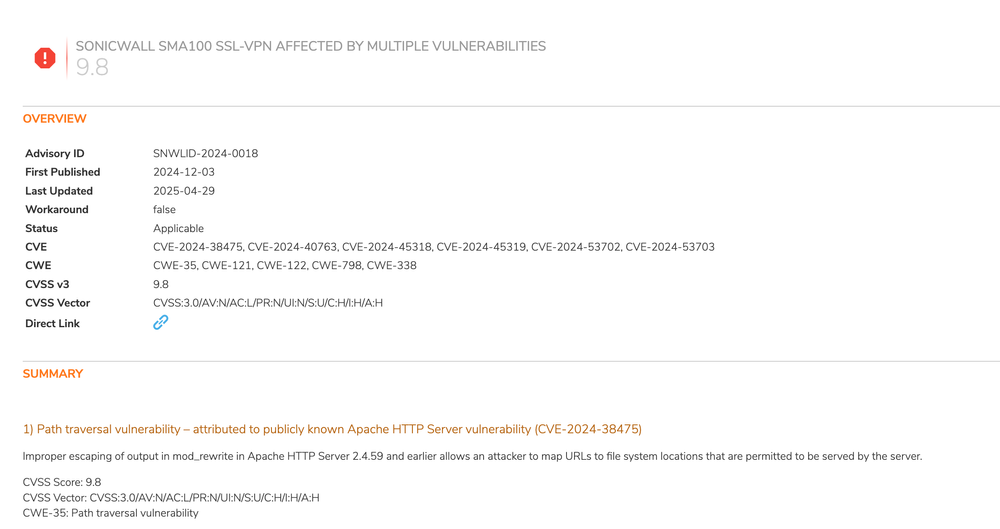
SonicWall identifies CVE-2024-38475 as a critical vulnerability in the mod_rewrite module of Apache HTTP Server version 2.4.59 and earlier. It improperly escapes output, enabling attackers to link malicious URLs to sensitive file paths and bypass authentication on affected SMA appliances.
CVE-2024-38475 is a vulnerability in Apache HTTP Server that allows attackers to bypass authentication and take control of affected SonicWall SMA appliances. This is a significant threat, especially when combined with CVE-2023-44221.
CVE-2023-44221 is a post-authentication command injection vulnerability in the Diagnostics menu of the SMA management interface. Authenticated attackers can inject system commands as the nobody user due to improper handling of special elements. This allows attackers with admin privileges to execute arbitrary commands.
This flaw is particularly dangerous because an attacker can use CVE-2024-38475 to hijack a session or gain higher privileges without valid credentials.
A threat actor can exploit CVE-2024-38475 to access restricted admin pages and steal session tokens, then use CVE-2023-44221 to execute arbitrary commands on the device. WatchTowr Labs has released a proof-of-concept exploit chain, highlighting the need for urgent patches.
The vulnerabilities impact the following SonicWall SMA appliances:
SMA 200
SMA 210
SMA 400
SMA 410
SMA 500v
SonicWall has issued firmware version 10.2.1.14-75sv and later as the fix. The company also confirmed an additional exploitation technique involving CVE-2024-38475, stating: “Unauthorized access to certain files could enable session hijacking.”
The Cybersecurity and Infrastructure Security Agency (CISA) included both flaws in its catalog on May 1, 2025, requiring that federal agencies apply patches by May 22, 2025.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind