Research by Group-IB has linked cyber-attacks on government organizations in Central Asia and the Asia-Pacific to a threat group called ShadowSilk. The activity started in 2023 and is still ongoing in July 2025, showing clear links to the YoroTrooper group. What’s different now is the size and structure of the campaign.
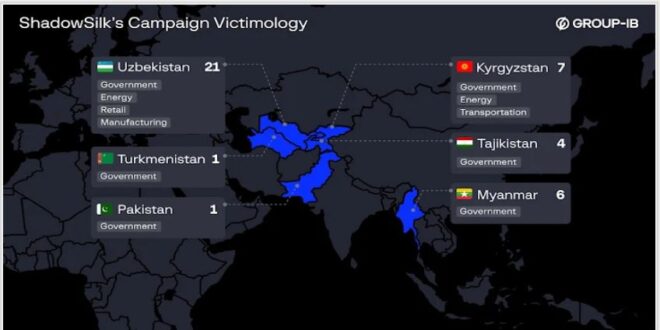
Group-IB, with help from CERT-KG, found at least 35 government victims and discovered new infrastructure, tools, and signs of both Russian and Chinese operators involved.
Researchers emphasize that ShadowSilk’s main goal is data theft, as stolen data from the group is found for sale on dark web forums.
Tools and Tactics:
ShadowSilk was seen using various hacking tools and malware.
Researchers found that Telegram bots were used as a command-and-control channel, allowing attackers to send commands, steal data, and mask harmful actions as regular messaging traffic. Web panels like JRAT and Morf Project, bought from underground forums, were used to control infected devices. The group also relied on phishing emails carrying password-protected archives to gain initial access.
When victims ran the payload, their systems were compromised, enabling attackers to use tools like Cobalt Strike and Metasploit for gathering information, maintaining access, and stealing credentials.
Russian and Chinese Operators:
Server analysis found Russian keyboard layouts and typing errors in commands, along with signs of malware development by Russian-speaking operators.
Screenshots of the attackers’ workstations showed Chinese-language tools and visits to Central Asian government sites, indicating involvement from Chinese speakers.
Group-IB researchers concluded that ShadowSilk is not simply a continuation of YoroTrooper, but a distinct threat cluster with shared roots.
“ShadowSilk continues to focus on the government sector in Central Asia and the broader APAC region, underscoring the importance of monitoring its infrastructure to prevent long-term compromise and data exfiltration,” the report said, noting that the group’s operations remain ongoing.
Recommendations:
Experts recommend that organizations implement strong email defenses to stop attacks from targeted phishing emails, and monitor the use of commands and built-in tools commonly used to gather system and file information.
They suggest using strict application control, regular updates, and advanced MXDR analytics focused on known malware.
Security teams should focus on proactive threat hunting to identify undetectable threats. They should also monitor dark web forums and data leaks to evaluate the organization’s security.
“Gayfemboy” Malware Exploiting Cisco, TP-Link and Other Routers
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind