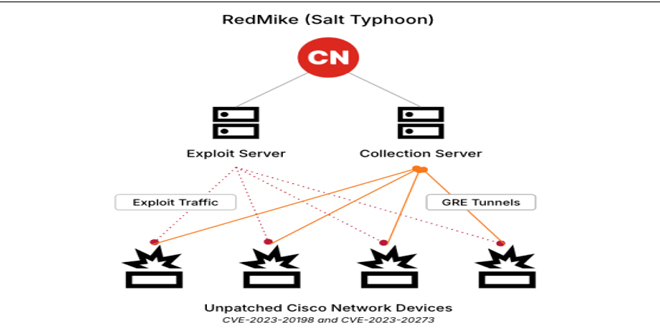
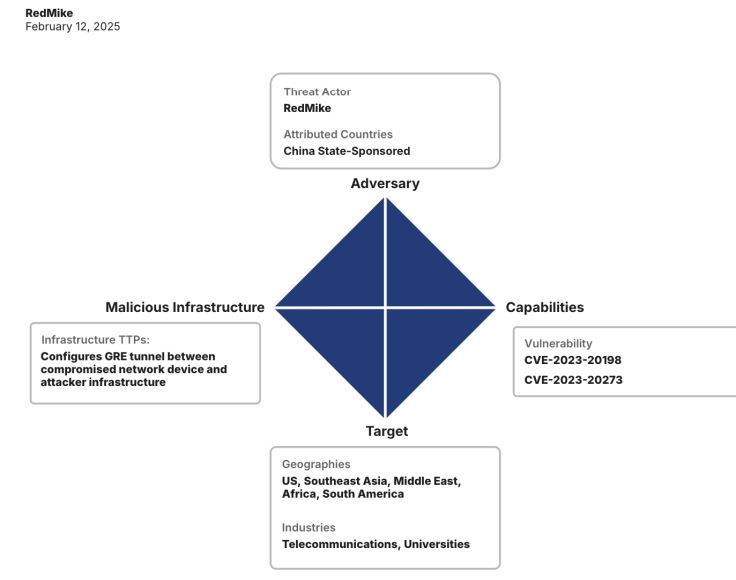
Between December 2024 and January 2025, Recorded Future’s Insikt Group discovered a campaign targeting unpatched Cisco devices used by major telecommunications providers. Victims included a US affiliate of a major UK telecom and a South African telecom. Insikt Group links this activity to the Chinese state-sponsored group RedMike, also known as Salt Typhoon by Microsoft.
Insikt Group, using Recorded Future® Network Intelligence, found that RedMike is targeting unpatched Cisco devices vulnerable to CVE-2023-20198, a privilege escalation flaw in Cisco IOS XE’s web UI. They first exploit this vulnerability for access, then use CVE-2023-20273 to gain root privileges. RedMike also reconfigures the device, creating a GRE tunnel for ongoing access.
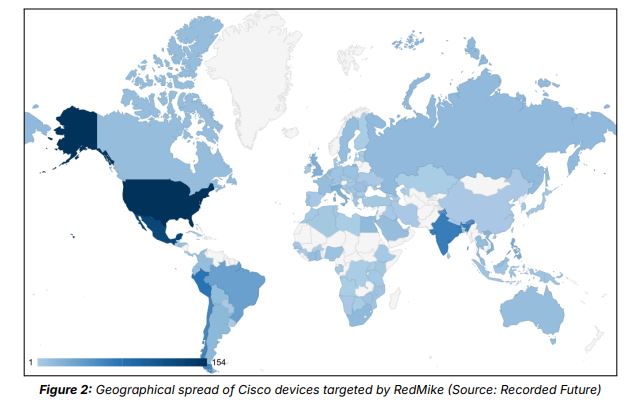
RedMike has targeted over 1,000 Cisco devices worldwide, likely focusing on those linked to telecommunications networks. The Insikt Group noted that RedMike also targeted devices at universities in Argentina, Bangladesh, Indonesia, Malaysia, Mexico, the Netherlands, Thailand, the US, and Vietnam.
RedMike may have targeted universities like UCLA and TU Delft to access research in telecommunications and technology. Additionally, in mid-December 2024, RedMike conducted reconnaissance on various IP addresses of the Myanmar-based telecommunications provider Mytel.
Unpatched public-facing devices are direct access points into an organization’s infrastructure. Over the past five years, advanced Chinese threat groups have increasingly targeted these devices for initial access. RedMike’s exploitation of telecommunications infrastructure highlights a strategic intelligence threat. Continuous access to critical communication networks allows state-backed actors to monitor confidential discussions, manipulate data, and disrupt services during geopolitical conflicts.
RedMike’s focus on lawful intercept programs and US political figures reveals strategic intelligence goals and national security risks. Telecommunications organizations must prioritize fixing exposed network devices, as unpatched systems are a primary entry point for state-sponsored Chinese threat groups.
Network administrators must enforce strict access controls, limit web UI exposure, and monitor for unauthorized changes. Individuals should use end-to-end encrypted communication for sensitive information, as recommended by the Cybersecurity and Infrastructure Agency (CISA) and the Federal Bureau of Investigation (FBI), to reduce eavesdropping risks.
Governments and cybersecurity organizations should enhance threat intelligence sharing and enforce stricter network security regulations. The US sanctions on Sichuan Juxinhe Network Technology, linked to RedMike, reflect a strong approach against state-sponsored cyber espionage. However, effective counteraction requires strong international cooperation.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind