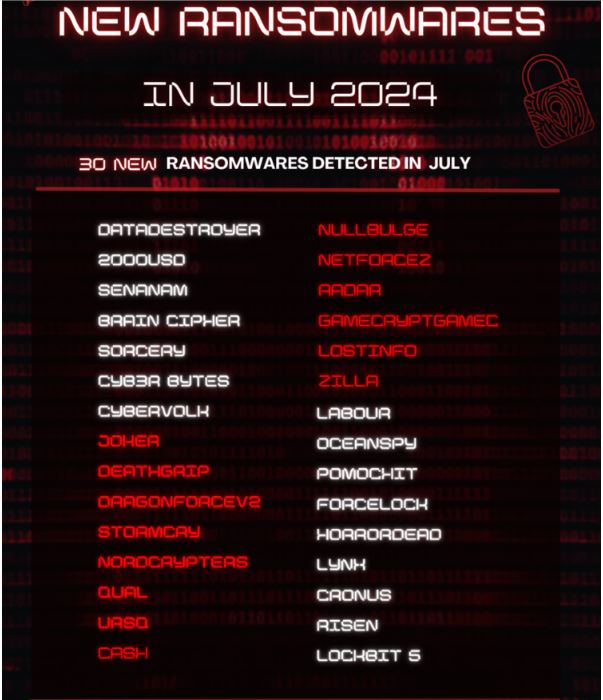
Cybersecurity experts found 30 new types of ransomware in July. These harmful programs are a big threat to people and businesses. Each new variant makes it harder to detect and stop them. Ransomware works by locking important data on infected computers and then asking for a lot of money in exchange for the key to unlock it. This not only puts personal information at risk, but also causes big financial problems for the victims.
DataDestroyer:
SHA-256: 5ad5c8798c20cd57a79375b6846c16dc94dea608140c013e4e686776a76bfc32
Extensions: .destroyer
2000USD
SHA-256: 81423f5454208e958aa183c2850809620676485c63aab07d91a6f85c1d9b4e72
Extensions: .2000USD
Senanam
SHA-256: 7bd9f91c2a196ccbd8363eaba02a4d19f382bacc3daccbae4354bb836a5912ad
Extensions: .senanam
Brain Cipher
SHA-256: 27a3cc834c1cd00ad5378c373d76957998bb54bbcfe67bbf3ae5c7be5a5a66dd
Extensions: .[random_string]
Sorcery
SHA-256: 275d0d15fa3582e848f05daa76d351e10ce3d7072e9c987eee1a1f606c714a97
Extensions: .sorcery
Cyb3r Bytes
SHA-256: 489e921e3f060b15e3825ca53205eddecbe65583b3de90bb3550049d2c278de8
Extensions: .cvenc
CyberVolk
SHA-256: 102276ae1f518745695fe8f291bf6e69856b91723244881561bb1a2338d54b12
Extensions: .cvenc
JOKER
SHA-256: 94b53c5c9177e88cddb4ef9828d70cd554ee6cafb501e68f35336d34f1994dfc
Extensions: .[four random characters]
DeathGrip
SHA-256: 8ae1d9e815abc504d01b48ecf21e4133b34b4b3e4a0e93804f44f8a9b328bd5d
Extensions: .DeathGrip
DragonForceV2
SHA-256: d4de7d7990114c51056afeedb827d880549d5761aac6bdef0f14cb17c25103b3
Extensions: .dragonforce_encrypted
StormCry
SHA-256: 4067b731d895acf92f04f223d3ceeab9924e909536fa207df2d6ff262752c400
Extensions: .stormous
NordCrypters
SHA-256: 359802bb670e2b361d94892a27b218d3580a0c8e49e819a91e36db0310e6d855
Extensions: .enc
Qual
SHA-256: 8440b663a841e89edf0a6a2efe707a27671625096b3d2e8c223fe23a4877b8e4
Extensions: .qual
Ursq
SHA-256: 0c0bae25b98cf13679d6d69be2007c6ace941c672f221bd90ec24961665ee8f0
Extensions: .ursq
Labour
SHA-256: 93fbf52fecb367b2373fefcc8a4bec8ef0762c8f9692719b0ac30ba6fd38fe7c
Extensions: .labour
NullBulge ( NullBulge is based on LockBit )
SHA-256: f28599b06560617bccdfb56acc841f3e642ff51b9956632fcc4204f026711e23
Extensions: Random extension
NetForceZ
SHA-256: 9308ea3ebaf4d39f8cb5f29b015cf0064f73170d61226a5f9b5b7c28173bc402
Extensions: .NetForceZ
RADAR
SHA-256: 9308ea3ebaf4d39f8cb5f29b015cf0064f73170d61226a5f9b5b7c28173bc402
Extensions: .[random character string]
GameCrypt
SHA-256: e202be6a3374a856529200a0984b189de2e4ebb0e3be0324b1eb57070bec7164
Extensions: .GameCrypt
LostInfo
SHA-256: 6718cb66521a678274e5672285bf208eac375827d622edcf1fe7eba7e7aa65e0
Extensions: .lostinfo
ZILLA
SHA-256: a275e4412f7d6a12c3bb628a7a846eb7078cd5ce4a1fc3d4a14bcae53dea6a1a
Extensions: .ZILLA
OceanSpy
SHA-256: fdfafaefbc9aa35dea9698a3f95b7c78977c0e3e5ab24e1728cd01f276a8c666
Extensions: .[four random characters]
Pomochit
SHA-256: 33a8024395c56fab4564b9baef1645e505e00b0b36bff6fad3aedb666022599a
Extensions: .pomochit01
ForceLock
SHA-256: 207eb5d3237c2eab96a0b433779bfe04c8342710b2b30a57b01c4d79d9e078ce
Extensions: .forcelock
HorrorDead
SHA-256: 6e7a64e8d70803263570dfd2eb3d05e9423cfe2c39a596e9109c4408325103f3
Extensions: .encrypted@HorrorDeadBot
Lynx
SHA-256: eaa0e773eb593b0046452f420b6db8a47178c09e6db0fa68f6a2d42c3f48e3bc
Extensions: .LYNX
Cronus
SHA-256: 42551531be1c5abfdd24a3465788c659a038141de61976787b0862664df95aad
Extensions: .[five random characters]
Risen
SHA-256: 31c68009f7ecf347876b80ea5f1cf54c713a5cbe60386d8e08bf47803dfd763f
Extensions: .[ user ID]
Cash
SHA-256: 5525d297a346b80912c4f5ec0ac4875e9d49f96d01e52c10df5c064bd803bd79
Extensions: .CashRansomware
LockBit 5
SHA-256: 3c13ae9a53b29849fd3bb75d3259a23658cd687441f8bdd610487007c51d2eac
Extensions: .[random characters]
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind