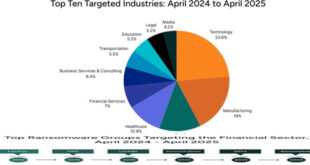
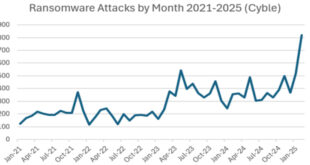
Cybersecurity experts found 28 new types of ransomware in June. These malicious programs are a big threat to individuals and businesses. Cybercriminals are improving their tactics with each new variant, making it harder to detect and stop them. Ransomware encrypts important data, making it impossible for users to access.
Afterward, the attackers ask for very high amounts of money to give back the decryption keys, effectively keeping important information as hostage. This bad practice not only puts personal and sensitive data at risk but also causes victims to have to pay a lot of money reported by Dailydarkweb.
Lexus
SHA-256: 4dddfd8d5d0a097700ec211ed5ff49ae6dc0426f1dcb0c97b13da0acffe09216
Extensions: .Lexus
Chaddad
SHA-256: ae2d15ad55b08ea8f3f3b3f2bf16ac28d12fb3f9fb20399afaaf918f1a34f29f
Extensions: .chaddad
Waqa
SHA-256: 9f7bdfe15f900f4f2f8da79dc35a05832cfcc4bbb07854780df338113f3d5336
Extensions: .waqa,
PartiZAN32
SHA-256: d0a91ad881db15a90e65cb9674978287dc41d895f6fff1d3459280334f831638
Extensions: .xqwertzuioplkjhgfyxcvbnmD
Watz
SHA-256: e832aad5a403e60642fc27593363ebc3b9dc7f81
Extensions: .watz
Anonymous Encryptor
SHA-256: 69d118fb4175ca4c144fd29b8c9c8a0218cb03da947e0136d36b08b2bd2b652c
Extensions: .Anonymous
Xam
SHA-256: 225e299bca1514858a1c31e85c05a2e7375f9f8d7095f5775dffe4d048e78892
Extensions: .xam
Orbit
SHA-256: babcf21571854dc02d7881ba125c3ba0cadf8ef1edc204573bbd73ab918cd8eb
Extensions: .orbit
RansomHubV2
SHA-256: 7539bd88d9bb42d280673b573fc0f5783f32db559c564b95ae33d720d9034f5a
Extensions: .[random characters]
DORRA
SHA-256: 18ba97ec9c00b85d27d9d20c62ef7bd9484ad68a33e2a2121a1bcbed19f2eacd
Extensions: .DORRA
Fog
SHA-256: e67260804526323484f564eebeb6c99ed021b960b899ff788aed85bb7a9d75c3
Extensions: ..FOG – .FLOCKED
Malware Mage
SHA-256: 599c48ddf6f8b7fa4564c26977db3ed931c4b14093674d071a4b77523fb56969
Extensions: .malwaremage
Run
SHA-256: cdc509cd5807b2fadafc1628a9cd4cfc93f0120d60c1b0446327bf65de68b9d9
Extensions: .run10
Trinity
SHA-256: 36696ba25bdc8df0612b638430a70e5ff6c5f9e75517ad401727be03b26d8ec4
Extensions: .trinitylock
El Dorado
SHA-256: 8badf1274da7c2bd1416e2ff8c384348fc42e7d1600bf826c9ad695fb5192c74
Extensions: .00000001
L3MON
SHA-256: 85772b8ab400e26de47ca174d6b85dc9bc8cd936ae5b2a4ba3cc4c1a855fe6de
Extensions: .[random characters]
Dkq
SHA-256: f7b9599f6c3793b43300909e1589654002eb96d0799d731f2507475e48862352
Extensions: .dkq
Lord Bomani
SHA-256: 4252fbc2706e9f8bbcb19be38dd0db73dda870411add5477717b2865fd484242
Extensions: .[[email protected]]
Rapax
SHA-256: 4c0fec496abf0c29ef8358d913781b9d0c00e3e53487b72cfbf42753f0aa5176
Extensions: .rapax
Cebrc
SHA-256: bed22d3be408109f34810e724299d9579f6991345f773ff7b4674827bc4fbc01
Extensions: .cebrc
AzzaSec
SHA-256: 58b45bfd8430d8b24f9142278ff206261ab3d1100b3c98b0fdfcefdddf2fd05d
Extensions: .AzzaSec
GhostHacker
SHA-256: bfad1fc041e176f9335d91cc4480e2c373d29354a33f5039212afe9e6d879978
Extensions: .GhostHacker
Jinwooks
SHA-256: 635adb7c70d41a43be40469bd0a517e8feb8a9ddb3e68f0ead3c2a4b82875213
Extensions: .jinwooksjinwooks
Geometrical
SHA-256: 4e359ae286505974c77f25cd4862138af31ad5fc63b29fc1682a59d996bddc85
Extensions: .geometrical
COBRA
SHA-256: bf0c353bf4f59db1d33b62589cca64d29c915d3073c86cd04e78f1d28bb65d74
Extensions: .COBRA
XFUN
SHA-256: 3c42e4eb06ef1211579d89dd651dafe541a3faf9b9a2bd8273cc61d101f30f5c
Extensions: .XFUN
Anonymous Arabs
SHA-256: 390db2712380d32479d8f0b61397e9cfba7eb084677cd46fc1e72555f5166420
Extensions: .encrypt
ShrinkLocker
SHA-256: e5471fb4827cb570e65c2ebdff5da38e64b6a9fe47a81d11dab2f0937315be30
Extensions: .ShrinkLock
(Media Disclaimer: This report is based on research conducted internally and externally using different ways. The information provided is for reference only, and users are responsible for relying on it. Infosecbulletin is not liable for the accuracy or consequences of using this information by any means)
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind