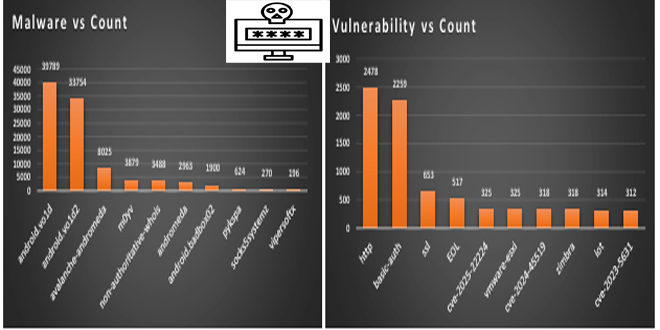
A new ransomware campaign is targeting individuals and organizations in the UK and US. The “Prince Ransomware” attack uses a phishing scam that pretends to be from the British postal service, Royal Mail.
The Attack Methodology:
Researchers at Proofpoint noticed the Prince Ransomware campaign in mid-September. The attack method is sneaky, using contact forms on websites of targeted organizations instead of regular email phishing.
This method lets attackers evade email security and reach many recipients in an organization. Attackers are sending messages that look like they come from a Proton Mail address, pretending to be official communications from Royal Mail.

These messages contain a PDF attachment that directs victims to download a ZIP file from Dropbox. This ZIP file includes a password-protected ZIP file and a text file with the password.
The second ZIP file includes a shortcut (LNK) file that runs JavaScript code to deploy ransomware.

The ransomware encrypts files on the victim’s computer, adding a “.womp” extension, and demands payment in Bitcoin for decryption.
A Destructive Outcome:
This campaign does not have a way to unlock files, unlike typical ransomware attacks, which aim to extort money in exchange for decrypting files. The ransom note inaccurately states that files have been stolen and offers automatic decryption for a payment of 0.007 Bitcoins (about $400).
There is no way to extract data or identify victims, so even if they pay, their files will still be inaccessible.
The attack’s destructive nature raises questions about its motives. It’s unclear if the attackers made a mistake or aimed to disrupt things without seeking financial gain.
The lack of communication instructions supports the theory that decryption was never intended.
Implications and Preventive Measures:
The Prince Ransomware campaign highlights the need for better understanding and readiness in cybersecurity. Organizations should educate employees on how to recognize phishing attempts and suspicious communications, particularly those with unexpected attachments or requests for sensitive information.
Organizations should use strong security measures like multi-factor authentication, regular software updates, and thorough data backup plans. These steps can reduce the impact of ransomware attacks and maintain business continuity.
The availability of Prince Ransomware on platforms like GitHub shows a larger cybersecurity problem: malicious tools are easily accessible for educational use and can be repurposed by threat actors.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind