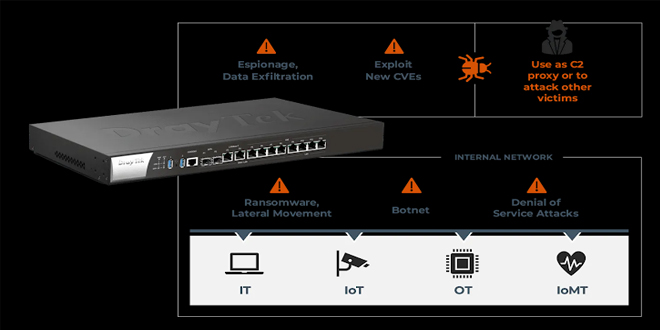
Over 14 new security flaws have been found in DrayTek routers for homes and businesses, which could allow attackers to take control of affected devices.
According to Forescout Vedere Labs,”These vulnerabilities could enable attackers to take control of a router by injecting malicious code, allowing them to persist on the device and use it as a gateway into enterprise networks,”
There are 14 security flaws: 2 are critical, 9 are high, and 3 are medium. The most severe flaw has a CVSS score of 10.0.
Router Vulnerabilities:
It relates to a bug in the “GetCGI()” function that may cause the router to crash or allow an attacker to run harmful code when handling query string inputs.
There is a serious vulnerability due to OS command injection in the “recvCmd” binary, which is used for communication between the host and guest operating systems.
The remaining 12 flaws are listed below :
Use of the same admin credentials across the entire system, resulting in full system compromise (CVSS score: 7.5)
A reflected cross-site scripting (XSS) vulnerability in the Web UI (CVSS score: 7.5)
A stored XSS vulnerability in the Web UI when configuring a custom greeting message after logging in (CVSS score: 4.9)
A stored XSS vulnerability in the Web UI when configuring a custom router name to be displayed to users (CVSS score: 4.9)
A reflected XSS vulnerability in the Web UI’s login page (CVSS score: 4.9)
Buffer overflow vulnerabilities in the Web UI’s CGI pages “/cgi-bin/v2x00.cgi” and “/cgi-bin/cgiwcg.cgi” leading to DoS or RCE (CVSS score: 7.2)
Buffer overflow vulnerabilities in the Web UI’s CGI pages leading to DoS or RCE (CVSS score: 7.2)
A stack buffer overflow vulnerability in the Web UI’s “/cgi-bin/ipfedr.cgi” page leading to DoS or RCE (CVSS score: 7.2)
Multiple buffer overflow vulnerabilities in the Web UI leading to DoS or RCE (CVSS score: 7.2)
A heap-based buffer overflow vulnerability in the Web UI’s ft_payloads_dns() function leading to DoS (CVSS score: 7.2)
An out-of-bounds write vulnerability in the Web UI leading to DoS or RCE (CVSS score: 7.2)
An information disclosure vulnerability in the web server backend for the Web UI that could allow an threat actor to perform an adversary-in-the-middle (AitM) attack (CVSS score: 7.6)
Forescout’s analysis revealed that over 704,000 DrayTek routers have their Web UI exposed to the internet, creating opportunities for attacks. Most of these exposed routers are in the U.S., with others in Vietnam, the Netherlands, Taiwan, and Australia.
DrayTek Routers:
Users are advised to patch for all identified flaws have been released by DrayTek, including the most serious issue fixed in 11 end-of-life (EoL) models.
Forescout said, “Complete protection against the new vulnerabilities requires patching devices running the affected software,”. “If remote access is enabled on your router, disable it if not needed. Use an access control list (ACL) and two-factor authentication (2FA) if possible.”
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind