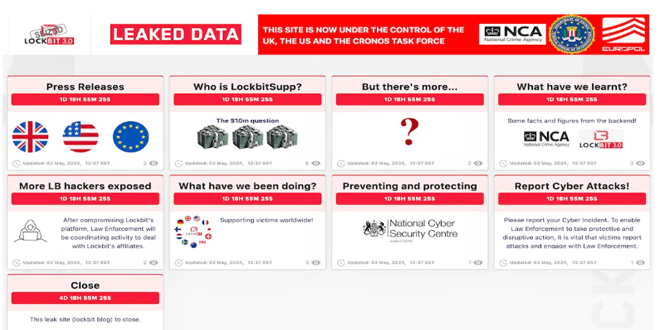
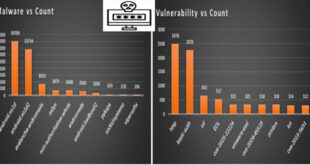
New information about the Lockbit ransomware gang might be coming soon. The gang’s old dark web leak site was taken down by law enforcement in February, but it has now reappeared, hinting at the release of new information in a few days.
Several parts of the site were updated on May 2, all promising more information to be dropped on May 7, including an answer to the “$10m question – who is LockbitSupp”. LockbutSupp is the gang’s apparent leader, and the law enforcement agencies involved in the site takedown have already suggested the individual is based in Russia, and had “engaged with law enforcement”.
By infosecbulletin
/ Wednesday , June 4 2025
IBM has issued a security advisory for vulnerabilities in its QRadar Suite Software and Cloud Pak for Security platforms. These...
Read More
By infosecbulletin
/ Wednesday , June 4 2025
As Bangladesh prepares for the extended Eid-ul-Adha holidays, the BGD e-GOV Computer Incident Response Team (CIRT) has issued an urgent...
Read More
By infosecbulletin
/ Tuesday , June 3 2025
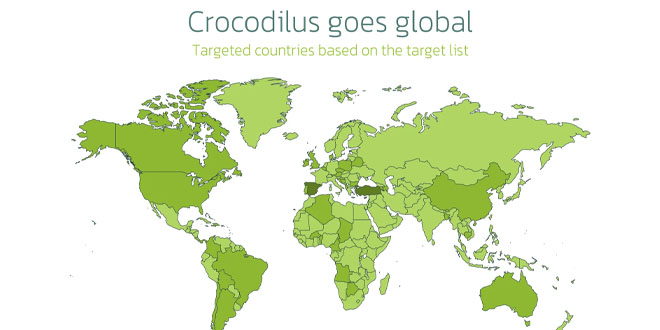
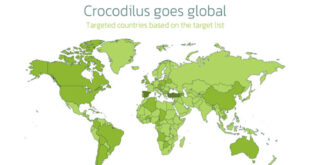
In March 2025, the Threatfabric mobile Threat Intelligence team identified Crocodilus, a new Android banking Trojan designed for device takeover....
Read More
By infosecbulletin
/ Tuesday , June 3 2025
Qualcomm has issued security patches for three zero-day vulnerabilities in the Adreno GPU driver, affecting many chipsets that are being...
Read More
By infosecbulletin
/ Monday , June 2 2025
Roundcube Webmail has fixed a critical security flaw that could enable remote code execution after authentication. Disclosed by security researcher...
Read More
By infosecbulletin
/ Sunday , June 1 2025
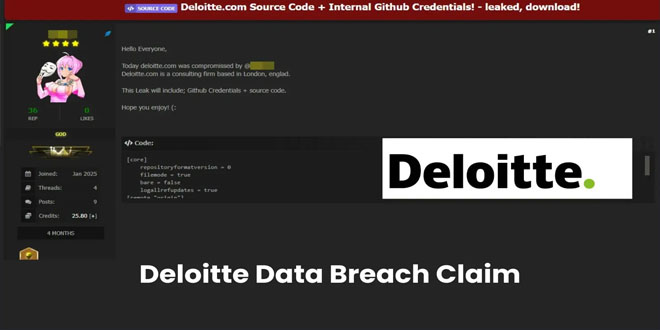
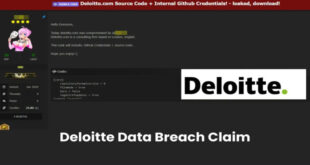
A hacker known as "303" claim to breach the company's systems and leaked sensitive internal data on a dark web...
Read More
By infosecbulletin
/ Sunday , June 1 2025
CISA and ACSC issued new guidance this week on how to procure, implement, and maintain SIEM and SOAR platforms. SIEM...
Read More
By infosecbulletin
/ Saturday , May 31 2025
The Qualys Threat Research Unit (TRU) found two local information-disclosure vulnerabilities in Apport and systemd-coredump. Both issues are race-condition vulnerabilities....
Read More
By infosecbulletin
/ Saturday , May 31 2025
New ransomware payment reporting rules take effect in Australia yesterday (May 30) for all organisations with an annual turnover of...
Read More
By infosecbulletin
/ Saturday , May 31 2025
Global makers of surveillance gear have clashed with Indian regulators in recent weeks over contentious new security rules that require...
Read More
NCA will reveal information about Lockbit’s partners and share details from the gang’s backend systems soon. The seized site reveals more LB hackers.
“What have we learnt?” says another. “Some facts and figures from the backend.” And, again a date of May 7 is given for when these details will be shared.
Prior to that In February, the U.K. National Crime Agency (NCA) confirmed that it got LockBit’s source code and gathered intelligence about its activities and affiliates as part of Operation Cronos.
“Some of the data on LockBit’s systems belonged to victims who had paid a ransom to the threat actors, evidencing that even when a ransom is paid, it does not guarantee that data will be deleted, despite what the criminals have promised,” the agency said that time.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind