Juniper Networks released updates to fix high-severity vulnerabilities in SRX Series and EX Series. These vulnerabilities could be exploited by attackers to gain control of vulnerable systems.
The vulnerabilities, tracked as CVE-2024-21619 and CVE-2024-21620, are rooted in the J-Web component and impact all versions of Junos OS.
By infosecbulletin
/ Saturday , July 27 2024
Malware based threats increased by 30% in the first half of 2024 compared to the same period in 2023, according...
Read More
By infosecbulletin
/ Friday , July 26 2024
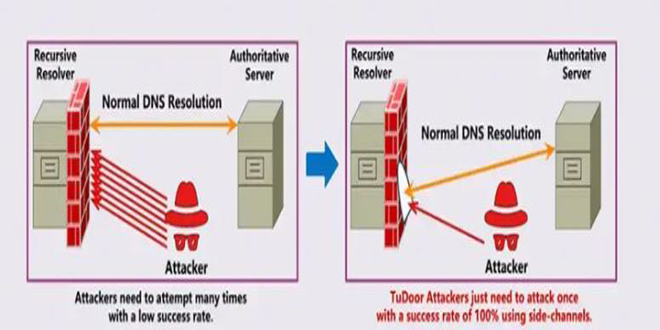
A new critical vulnerability in the Domain Name System (DNS) has been found. This vulnerability allows a specialized attack called...
Read More
By infosecbulletin
/ Friday , July 26 2024
A serious vulnerability, CVE-2023-45249 (CVSS 9.8), has been found in Acronis Cyber Infrastructure (ACI), a widely used software-defined infrastructure solution...
Read More
By infosecbulletin
/ Friday , July 26 2024
OpenAI is testing a new search engine "SearchGPT" using generative artificial intelligence to challenge Google's dominance in the online search...
Read More
By infosecbulletin
/ Thursday , July 25 2024
CISA released two advisories about security issues for Industrial Control Systems (ICS) on July 25, 2024. These advisories offer important...
Read More
By infosecbulletin
/ Thursday , July 25 2024
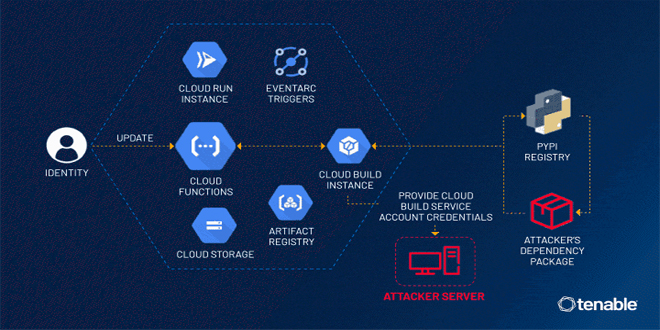
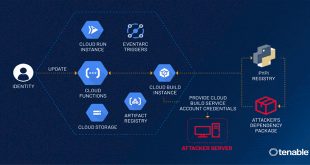
Tenable security researchers found a vulnerability in Google Cloud Platform's Cloud Functions service that could allow an attacker to access...
Read More
By infosecbulletin
/ Thursday , July 25 2024
BDG e-GOV CIRT's Cyber Threat Intelligence Unit has noticed a concerning increase in cyber-attacks against web applications and database servers...
Read More
By infosecbulletin
/ Thursday , July 25 2024
GitLab released a security update today to fix six vulnerabilities in its software. Although none of the flaws are critical,...
Read More
By infosecbulletin
/ Thursday , July 25 2024
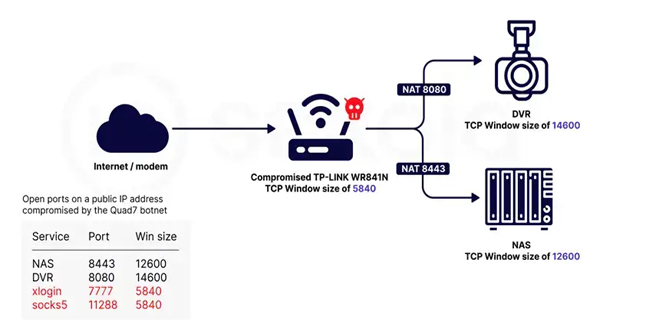
Sekoia.io and Intrinsec analyzed the Quad7 (7777) botnet, which uses TCP port 7777 on infected routers to carry out brute-force...
Read More
By infosecbulletin
/ Wednesday , July 24 2024
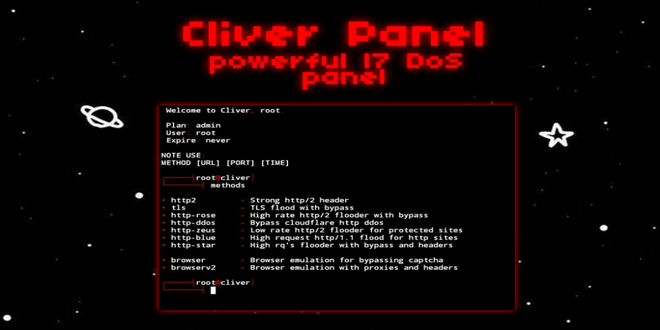
A threat actor has announced a new DDoS tool called Cliver, which offers strong attack methods for disrupting web services,...
Read More
There are vulnerabilities in the J-Web component of Junos OS, identified as CVE-2024-21619 and CVE-2024-21620. These vulnerabilities affect all versions of Junos OS. In addition, two other weaknesses, CVE-2023-36846 and CVE-2023-36851, were disclosed by the company in August 2023.
CVE-2024-21619 (CVSS score: 5.3) – A vulnerability that could expose sensitive configuration information
CVE-2024-21620 (CVSS score: 8.8) – “A vulnerability that could allow attackers to execute arbitrary commands with the target’s permissions”
Cybersecurity company watchTowr Labs found and reported the problems. The issues have been fixed in the latest versions.
CVE-2024-21619 – 20.4R3-S9, 21.2R3-S7, 21.3R3-S5, 21.4R3-S6, 22.1R3-S5, 22.2R3-S3, 22.3R3-S2, 22.4R3, 23.2R1-S2, 23.2R2, 23.4R1, and all subsequent releases
CVE-2024-21620 – 20.4R3-S10, 21.2R3-S8, 21.4R3-S6, 22.1R3-S5, 22.2R3-S3, 22.3R3-S2, 22.4R3-S1, 23.2R2, 23.4R2, and all subsequent releases
Until the fixes are installed, the company suggests either disabling J-Web or limiting access to trusted hosts. Both CVE-2023-36846 and CVE-2023-36851 were added to the Known Exploited Vulnerabilities (KEV) catalog in November 2023 by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) due to evidence of active exploitation.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind