Tenable says, the recent surge in cyber attacks on Indian hospitals is raising alarming concerns about the safety of healthcare and personal data. This pressing issue was brought into the limelight following the recent breach of the CoWIN portal, India’s primary platform for COVID-19 vaccine distribution, according to a report by Tenable.
The breach of the CoWIN portal, the primary platform for COVID-19 vaccine distribution in India, has brought this pressing issue to the forefront. The breach, which occurred through a state-operated chatbot on a popular instant messaging application, resulted in the unauthorized exposure of healthcare and personal data belonging to millions of citizens. Though the Indian gov.t denied the breach. The Union Health Ministry and the Indian Computer Emergency Response Team (CERT-In) have launched investigations into this major data breach.
“Cybercriminals have long been attracted to organizations with high potential yields, such as healthcare and critical infrastructure providers, due to the lucrative profits involved,” warned Kartik Shahani, Country Manager for Tenable India.
“There’s a clear shift towards cybercriminals seeking high-value healthcare data. They are well-aware that healthcare providers have been historically slow to adopt proactive measures to secure their interconnected IT and OT systems.”
The shift of cybercriminals towards targeting healthcare data is a clear indication of the potential harm that can be caused if such sensitive information is compromised. Historically, healthcare providers have been slow in adopting proactive measures to secure their interconnected IT and OT systems, making them attractive targets for cybercriminals seeking lucrative profits. The consequences of these cyber attacks are extensive and include financial losses, disruptions to vital medical services, and compromised patient information and care.
The healthcare sector in India has become the second most targeted industry by cybercriminals, as
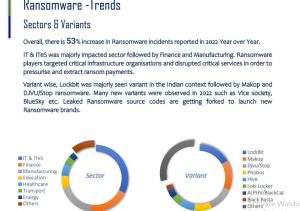
highlighted in the 2022 Threat Landscape Report. Additionally, a study by Cert-In revealed that healthcare ranked as the fifth most-targeted sector by ransomware perpetrators. These alarming statistics emphasize the urgent need for healthcare organizations to thoroughly evaluate their vulnerabilities, identify potential attack pathways, and prioritize the protection of critical assets.
Furthermore, as the Indian government plans to enact stringent data protection laws, the stakes are higher for organizations. The proposed Digital Personal Data Protection Bill imposes strict penalties on organizations that fail to implement cybersecurity measures to safeguard customer data. It is crucial for healthcare organizations to not solely rely on upcoming regulations but to prioritize cybersecurity by taking proactive measures to protect sensitive data.
These proactive measures include conducting regular risk assessments, providing cybersecurity training to employees, and implementing continuous monitoring systems to detect potential threats. By taking these steps, healthcare organizations not only secure data but also maintain public trust, ensure the continuity of crucial services, and prioritize the well-being of individuals.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














