The telecom industry emerged as a prime target for advanced adversaries and state-sponsored actors in 2022, resulting in a significant increase in Talos IR cases focused on this sector.
Telecommunications companies possessing crucial infrastructure assets are particularly attractive targets due to their pivotal role in national networks, making them potential gateways for adversaries.
ALSO READ:
Trend Micro Releases Urgent Fix for Critical Security Vulnerability
Researchers at Cisco Talos have discovered a new malware called “HTTPSnoop” that is specifically designed to target telecom companies in the Middle East. This malware uses innovative techniques to interact with Windows HTTP kernel drivers in order to execute content based on URLs.
The implant cluster, which consists of HTTPSnoop and PipeSnoop, exhibits unique Tactics, Techniques, and Procedures (TTPs). It is associated with a newly discovered intrusion set called “ShroudedSnooper” because its characteristics do not align with any known groups monitored by Talos.
Variants of HTTPSnoop
In total, the attackers built three variants of HTTPSnoop:-
Variant 1:
There are DLL-based HTTPSnoop variants that cleverly utilize DLL hijacking in harmless applications. The initial variant, born on April 17, 2023, expertly connects to HTTP URLs that bear a strikinThe EWS API in Microsoft has a strong resemblance. It allows shellcode to be executed without any issues.
Variant 2:
The second variant of HTTPSnoop, created on April 19, 2023, is similar to the original version but focuses on different HTTP URLs on Ports 80 and 443. This could be for a web server that is not associated with EWS.
Variant 3:
To minimize the risk of detection, they later developed a third variant on April 29, 2023, which included a killswitch URL and another listening URL. This strategic move aimed at confining the URLs to a more restricted range.
HTTPSnoop Malware Interface
HTTPSnoop and PipeSnoop were cleverly disguised as components of Palo Alto Networks’ Cortex XDR app. Their altered compile timestamps indicated that they were active during the v7.8 window, which spanned from August 2022 to April 2023.
HTTPSnoop is a basic but efficient backdoor that does the following things:-
Uses low-level Windows APIs to interact with HTTP devices
Listen for specific URL patterns
Executes decoded shellcode from incoming requests
The analyzed DLL consists of two crucial components, as mentioned below:
Encoded Stage 2 shellcode.
Encoded Stage 2 configuration.
Once the malicious DLL XOR is activated, it proceeds to decode and execute the Stage 2 configuration and shellcode.
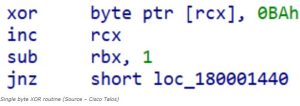
PipeSnoop is an exclusive implant specifically crafted for diverse environments. It is commonly utilized in enterprise settings that possess IPC pipe I/O capabilities. With its creation dating back to May 2023, PipeSnoop stands out as a remarkable tool.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind