Cyber Threat Intelligence Unit of BGD e-GOV CIRT found evidence of compromise linked to the vulnerability in F5 BIG-IP systems used in Bangladesh’s IT infrastructure. Investigators discovered that attackers gained shell access to the system and tried to sell this unauthorized access on the dark web.
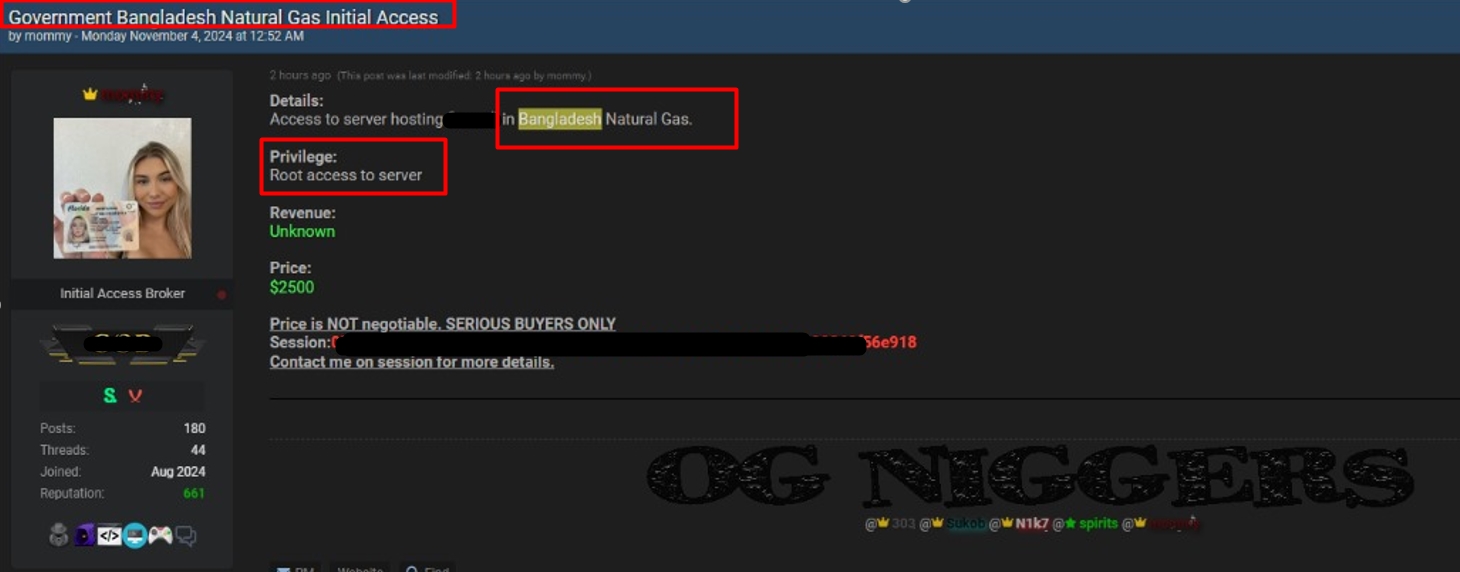
On October 30, one attacker claimed to have root-level access to a server, initially offering it for a fixed price, which increased to $2,500 by November 4.
Analysis confirmed CVE-2023-46747, a authentication bypass vulnerability in F5 BIG-IP systems that allows attackers to execute remote code and access the Traffic Management User Interface (TMUI) without authentication. This vulnerability can give attackers full administrative control and has been exploited alongside CVE-2023-46748, a high-severity SQL injection flaw seen in active attacks reported by F5.
CVE-2023-46747 vulnerability overview:
On October 25, 2023, cybersecurity firm Praetorian announced a critical vulnerability (CVE-2023-46747) in F5 BIG-IP systems, allowing unauthenticated attackers to gain full administrative access due to poor input validation. This vulnerability has a CVSS score of 9.8.
The next day, F5 confirmed this issue and also reported a high-severity SQL injection flaw (CVE-2023-46748) with a CVSS score of 8.8, which is being exploited alongside the first vulnerability, heightening risks for affected systems.
Affected Versions:
BIG-IP Versions Prior to 17.0: All versions preceding 17.0 are vulnerable.
Exposed Management Interfaces: Deployments with publicly accessible management interfaces, particularly those lacking strict access controls or IP restrictions, are at heightened risk.
Patch Deployment: Install the latest security updates from F5 to fix this issue.
Restrict Access: Allow access to the F5 BIG-IP management interface only from internal IPs.
Implement Multi-Factor Authentication (MFA): Require all users to use MFA for accessing the BIG-IP management portal to improve security.
Enhanced Logging and Monitoring: Turn on detailed logging on BIG-IP systems and watch for unusual behavior, especially regarding privileged actions.
Isolate Compromised Systems: Isolate any compromised systems and conduct a thorough investigation.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind