Google launched a new bug bounty program called kvmCTF to enhance the security of its Kernel-based Virtual Machine (KVM) hypervisor. This program offers up to $250,000 as a reward to security researchers who successfully achieve a full virtual machine (VM) escape exploit.
KVM, an open-source hypervisor, is important in consumer and enterprise settings. It has been developed for over 17 years and is used in Android and Google Cloud platform.
By infosecbulletin
/ Tuesday , October 22 2024
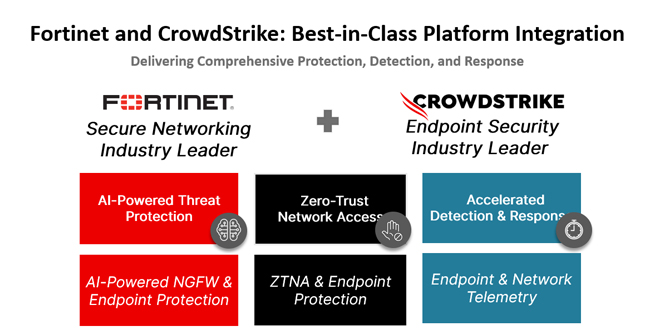
In today's rapidly changing cybersecurity environment, organizations encounter numerous complex threats targeting endpoints and networks. CrowdStrike and Fortinet have partnered...
Read More
By infosecbulletin
/ Tuesday , October 22 2024
Sophos, based in the UK, is to acquire Secureworks, a Nasdaq-listed company, for $859 million in cash from Dell Technologies....
Read More
By infosecbulletin
/ Monday , October 21 2024
The Internet Archive was breached again, this time through their Zendesk email support platform, following warnings that threat actors had...
Read More
By infosecbulletin
/ Sunday , October 20 2024
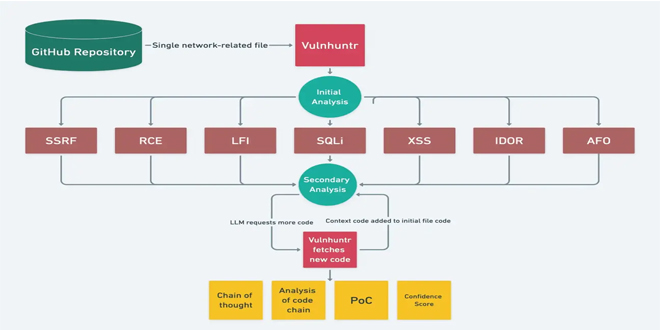
In today's changing cybersecurity environment, it's essential to find vulnerabilities in code. Vulnhuntr, an open-source tool on GitHub, uses Large...
Read More
By infosecbulletin
/ Friday , October 18 2024
Bitdefender said a vulnerability has been identified in Bitdefender Total Security HTTPS scanning functionality where the software fails to properly...
Read More
By infosecbulletin
/ Thursday , October 17 2024
Cybersecurity threats have surged to extraordinary heights, as Microsoft’s latest Digital Defense Report reveals that its customers are confronted with...
Read More
By infosecbulletin
/ Thursday , October 17 2024
VMware has issued a warning about a remote code execution vulnerability, CVE-2024-38814, with a CVSS score of 8.8, in its...
Read More
By infosecbulletin
/ Thursday , October 17 2024
Mandiant researchers found that over 90 zero-day vulnerabilities and more than 40 known vulnerabilities were exploited in the wild. Vulnerabilities...
Read More
By infosecbulletin
/ Wednesday , October 16 2024
Oracle's October 2024 Critical Patch Update has fixed 334 security vulnerabilities in its products. The CPU affects 28 Oracle product...
Read More
By infosecbulletin
/ Wednesday , October 16 2024
Google has released Chrome 130, fixing 17 security vulnerabilities. The update (version 130.0.6723.58/.59 for Windows and Mac, and 130.0.6723.58 for...
Read More
The reward tiers are the following:
Relative memory read: $10,000
Denial of service: $20,000
Arbitrary memory read: $50,000
Relative memory write: $50,000
Arbitrary memory write: $100,000
Full VM escape: $250,000
Like Google’s kernelCTF vulnerability reward program, which targets Linux kernel security flaws, kvmCTF focuses on VM-reachable bugs in the Kernel-based Virtual Machine (KVM) hypervisor.
The objective is to carry out successful attacks from a guest to a host. No rewards will be given for vulnerabilities in QEMU or from the host to KVM.
Researchers in the program can use exploits to capture flags in a controlled lab environment. The focus is on zero-day vulnerabilities, not known ones. The kvmCTF runs on Google’s Bare Metal Solution (BMS) for top security.
“Participants will be able to reserve time slots to access the guest VM and attempt to perform a guest-to-host attack. The goal of the attack must be to exploit a zero day vulnerability in the KVM subsystem of the host kernel,” said Google software engineer Marios Pomonis.
“If successful, the attacker will obtain a flag that proves their accomplishment in exploiting the vulnerability. The severity of the attack will determine the reward amount, which will be based on the reward tier system explained below. All reports will be thoroughly evaluated on a case-by-case basis.”
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind