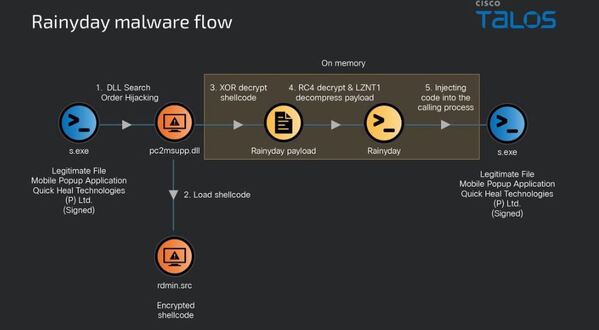
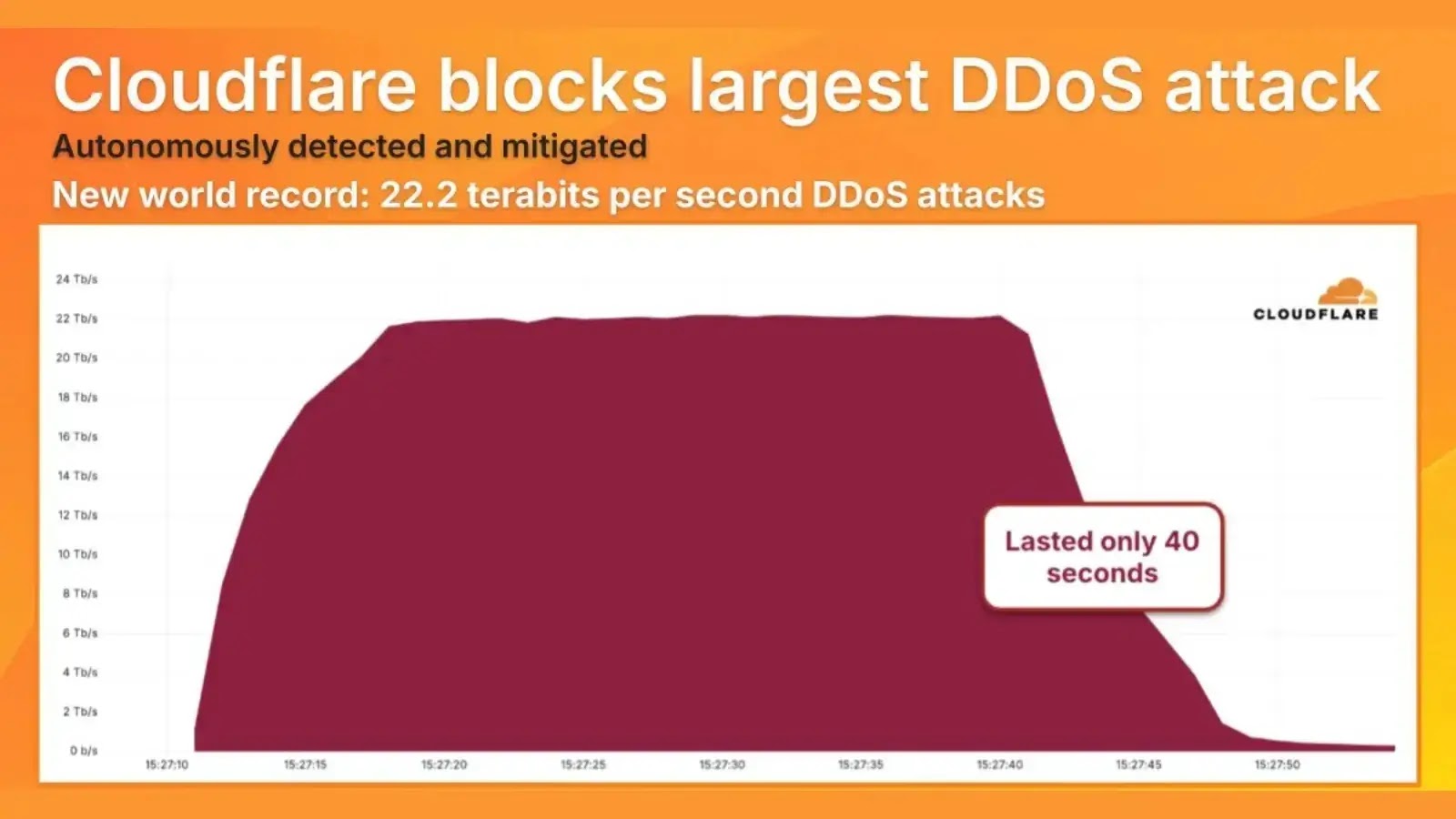
Bangladesh’s use of technology in the digital era brings up a major challenge in cybersecurity. Previous cyberattacks have shown the need for stronger protection.
The incidents in 2014 and 2016 caused significant financial losses in the banking sector, showing the importance of improving cybersecurity.
More recent disruptions, such as ransomware in the national airline and a government website breach in 2023, highlight the urgent need for IT experts to make cybersecurity a top priority. As businesses use more technology, it is crucial for them to integrate strong cybersecurity into their corporate culture to protect against evolving threats.
ALSO READ:
Public private partnership is essential to increase cyber awareness
Bangladesh is a prime target for cyber threats because of its geopolitical position. The cybersecurity challenges have become worse due to regional conflicts and the global pandemic. This has led to more cyberattacks on government, private, and financial institutions.
As a cybersecurity expert, enthusiast, IT professional, and technological leader, it is imperative to address these challenges within the context of Bangladesh’s corporate culture. Here are key guidelines for corporate leaders and directors to improve cybersecurity culture and fortify their organizations:
Raise Awareness and Provide Training:
* Conduct regular cybersecurity awareness programs tailored to the organization’s needs.
* Empower employees with training sessions, making them an integral part of the defense against cyber threats.
Leadership Engagement:
* Secure leadership buy-in to prioritize and set an example for the entire organization.
* Actively involve top-level management in cybersecurity initiatives to demonstrate its importance.
Emphasize Accountability:
* Leverage the existing culture of responsibility by making individuals accountable for their cybersecurity actions.
* Encourage employees to report suspicious activities and reward proactive contributions to organizational security.
Cultural Adaptation:
* Align security policies and practices with the existing corporate culture.
* Strike a balance between security measures and workplace norms for effective implementation.
Invest in Technology and Infrastructure:
* Allocate resources to acquire and implement robust cybersecurity tools and infrastructure.
* Ensure IT professionals have access to the latest security technologies to enhance defense mechanisms.
Develop an Incident Response Plan:
* Establish a well-defined incident response plan for detecting, containing, and recovering from cybersecurity incidents.
* Regularly test and refine these procedures to ensure their effectiveness.
Encourage Collaboration and Information Sharing:
* Foster collaboration between departments and organizations.
* Form alliances or industry-specific cybersecurity forums for sharing threat intelligence and best practices.
By incorporating these guidelines into the fabric of Bangladeshi corporate culture, organizations can fortify their defenses against the ever-evolving landscape of cyber threats, ensuring a secure and resilient digital future.
Writer:
Muhibbul Muktadir Tanim
Senior Manager, IT Infrastructure & Systems Management, icddr,b
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind