Cybersecurity researchers at Trend Micro discovered an exploitation of CVE-2023-36025 leading to the spread of a new type of malware called Phemedrone Stealer.
Phemedrone Stealer is a malware that targets web browsers, cryptocurrency wallets, and messaging apps like Telegram, Steam, and Discord. It not only steals data, but also takes screenshots and collects important system information. The stolen data is sent to the attackers through Telegram or their command-and-control server. What makes it different is that it is an open-source malware written in C#. It is actively maintained on GitHub and Telegram.
Phemedrone Stealer became successful by using a vulnerability in Microsoft Windows Defender SmartScreen called CVE-2023-36025. This vulnerability allows threat actors to create malicious .url files that can avoid detection by Windows Defender SmartScreen. Although Microsoft fixed this issue on November 14, 2023, it was added to the list of Known Exploited Vulnerabilities by the Cybersecurity and Infrastructure Security Agency (CISA) due to its active exploitation.
Phemedrone Stealer infects users by hosting malicious Internet Shortcut files on platforms like Discord or cloud services such as FileTransfer.io. These files are disguised using URL shorteners, which tricks unsuspecting users. When a user opens the malicious .url file, the exploitation of CVE-2023-36025 begins.
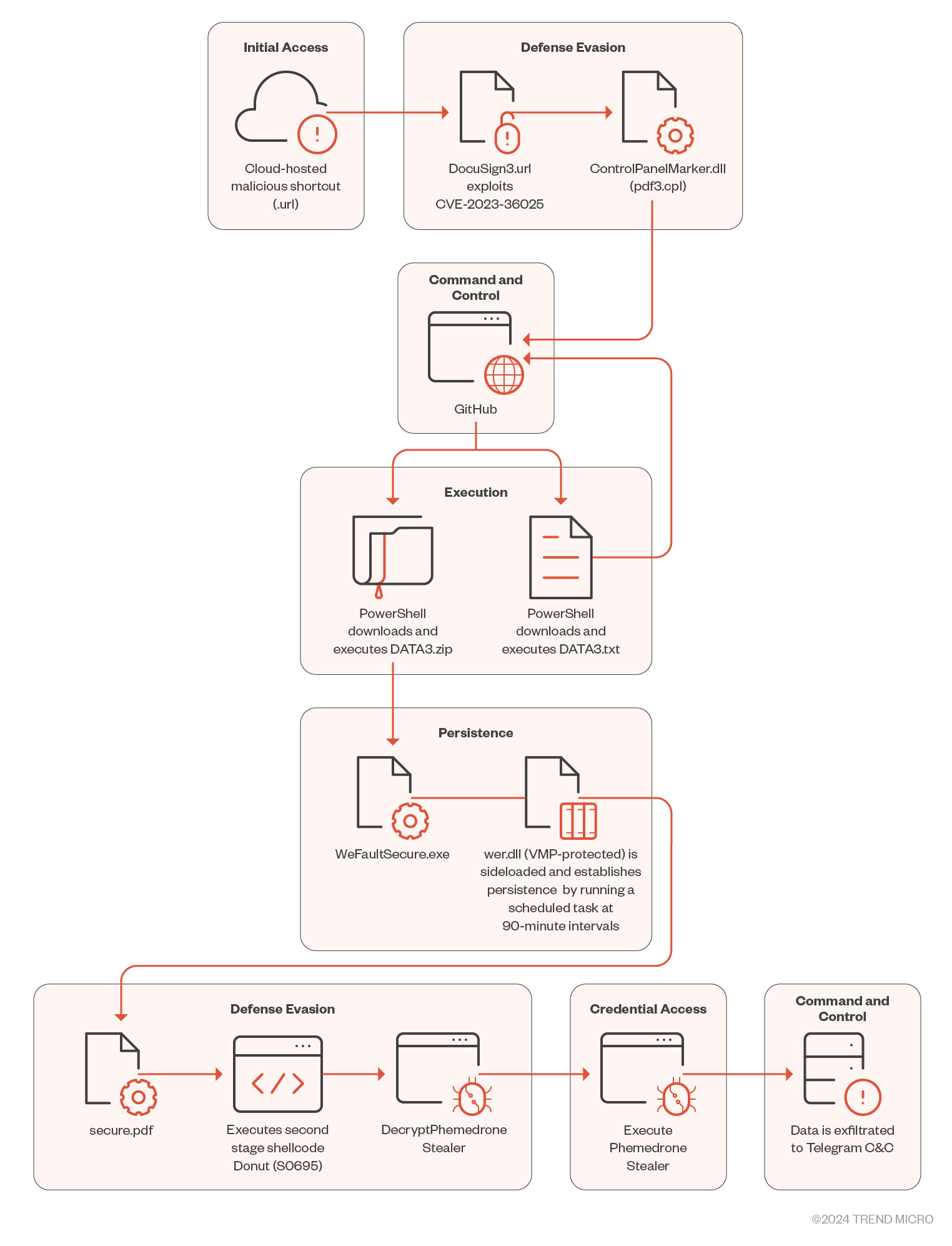
When the harmful .url file is opened, Phemedrone Stealer connects to a server controlled by an attacker to download and run a .cpl file. The attackers use .cpl files to bypass Windows Defender SmartScreen’s security checks. They misuse the Windows Control Panel process to run these .cpl files, which are actually DLL files.
After executing the .cpl file, rundll32.exe is called to run the DLL. This DLL is malicious and serves as a loader, using Windows PowerShell to download and run the next stage of the attack from GitHub. The next stage is another PowerShell loader called DATA3.txt.
The file DATA3.txt uses techniques to hide its purpose, making it hard to understand with static analysis alone. Researchers use both static and dynamic analysis to understand the GitHub-hosted loader. They find a ZIP file on the same GitHub repository containing three files: WerFaultSecure.exe (legitimate), Wer.dll (malicious), and Secure.pdf (which is a second-stage loader encrypted with RC4).
Wer.dll is important for maintaining access by scheduling tasks. The loader tricks the system to load a harmful file instead of the real one, using dynamic API resolving and the CRC-32 hashing algorithm. It also uses XOR-based algorithms for string decryption, making it more complex.
Phemedrone Stealer is well-equipped to harvest a wide array of sensitive information, including browser data, cryptocurrency wallet details, Discord tokens, and much more. It employs a custom method to dynamically locate all subclasses of IService, efficiently processing them. Following data collection, it compresses and exfiltrates the information through network traffic via the Telegram API.
Exploiting CVE-2023-36025 is still a serious threat, as cybercriminals are using it to spread malware like Phemedrone Stealer. This case shows how open-source malware and public proof-of-concept exploits are connected. To reduce the risk, organizations should quickly update their Microsoft Windows systems and be alert to new threats in cybersecurity.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind