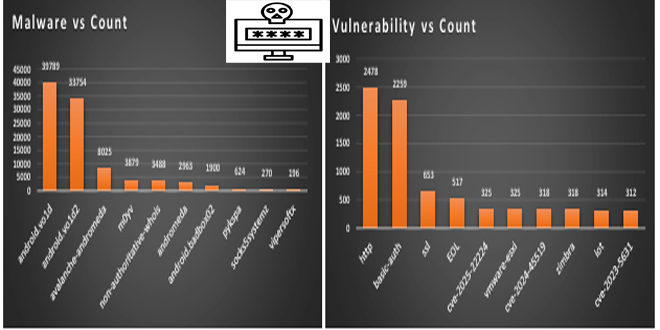
Cisco warned about a serious security issue called “regreSSHion” (CVE-2024-6387) that affects the OpenSSH server in some Cisco products and cloud services. This could let unauthorized attackers run their own code on affected systems, possibly taking full control of the system.
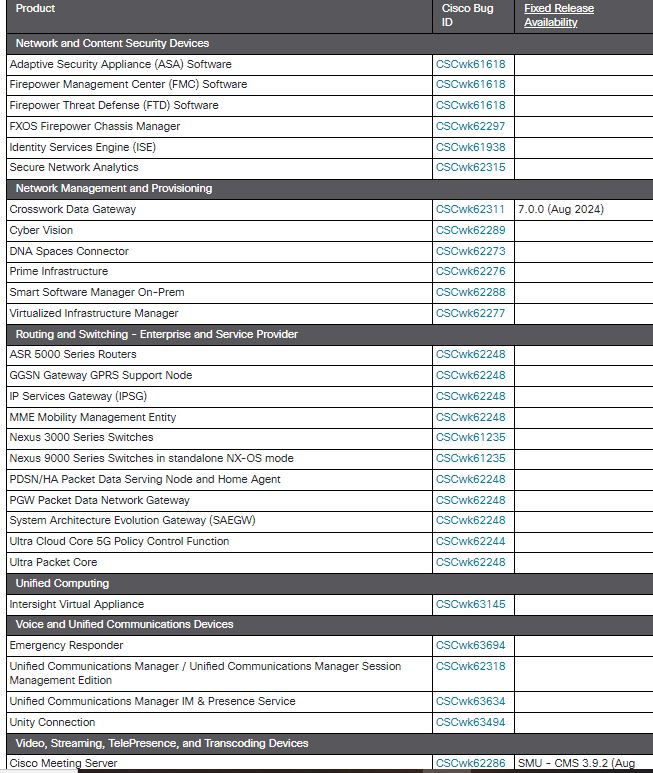
The following table lists Cisco products that are affected by the vulnerability that is described in this advisory. If a future release date is indicated for software, the date provided represents an estimate based on all information known to Cisco as of the Last Updated date at the top of the advisory. Availability dates are subject to change based on a number of factors, including satisfactory testing results and delivery of other priority features and fixes. If no version or date is listed for an affected component (indicated by a blank field and/or an advisory designation of Interim), Cisco is continuing to evaluate the fix and will update the advisory as additional information becomes available. After the advisory is marked Final, customers should refer to the associated Cisco bug(s) for further details.
Cisco’s investigation has identified numerous affected products across various categories, including:
Network and Content Security Devices: Adaptive Security Appliance (ASA) Software, Firepower Management Center (FMC) Software, Firepower Threat Defense (FTD) Software, FXOS Firepower Chassis Manager, Identity Services Engine (ISE), Secure Network Analytics.
Network Management and Provisioning: DNA Spaces Connector, Crosswork Data Gateway, Cyber Vision, Prime Infrastructure.
Routing and Switching: ASR 5000 Series Routers, Nexus 3000 and 9000 Series Switches, GGSN Gateway, and various other networking devices.
Unified Computing: Intersight Virtual Appliance, Virtualized Infrastructure Manager.
Voice and Unified Communications: Emergency Responder, Unified Communications Manager, Unity Connection.
Video and Collaboration: Cisco Meeting Server, Expressway Series, TelePresence Video Communication Server (VCS).
Wireless: Various access points and wireless controllers.
Mitigation and Remediation
Cisco advises users to apply available patches for their affected products as soon as possible to reduce the risk of exploitation. The company has announced release dates for fixes for most products, and is still evaluating others. to read the full report click here.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind