Cyble Analyzes An Active Campaign Exploiting A Microsoft SmartScreen Vulnerability To Deliver Stealers Via Spam Emails.
Key findings:
* Cyble Research and Intelligence Labs (CRIL) recently came across an active campaign exploiting the Microsoft SmartScreen vulnerability (CVE-2024-21412).
* The ongoing campaign targets multiple regions, including Spain, the US, and Australia.
* It uses fake healthcare insurance, transportation, and tax messages to trick people and companies into downloading harmful files onto their computers.
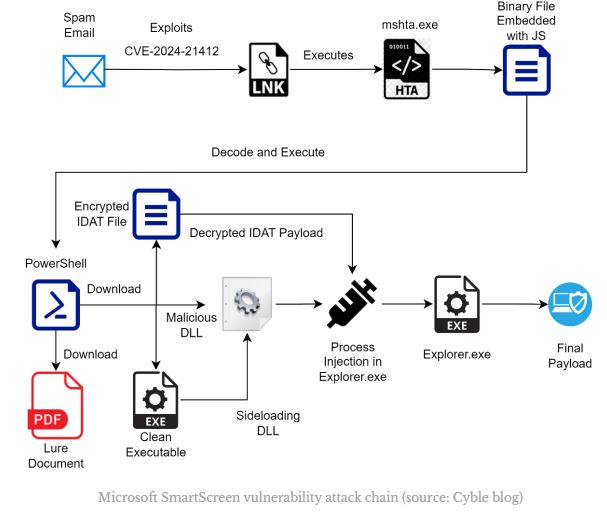
* Users are tricked into opening a spam email and clicking on a link that takes them to a WebDAV share. They are then deceived into running a harmful internet shortcut file, which takes advantage of a vulnerability known as CVE-2024-21412.
The attackers used various legitimate tools like forfiles.exe, PowerShell, mshta, and other trusted files to bypass security measures during their multi-stage attack. The attack chain utilizes DLL sideloading and IDATLoader to inject the final payload into explorer.exe. This campaign delivers Lumma and Meduza Stealer as its final payloads.
In January 2024, a campaign called DarkGate was discovered by the Zero Day Initiative (ZDI). It used fake software installers and took advantage of a vulnerability called CVE-2024-21412. On February 13, 2024, Microsoft released a patch to fix a vulnerability in Microsoft Defender SmartScreen that was exploited by DarkGate. Following this, a group called Water Hydra, also known as an APT group, used the same vulnerability to target financial market traders. They bypassed SmartScreen and distributed a remote access trojan called DarkMe.
CRIL found a campaign that misused internet shortcuts. In this campaign, TAs used a vulnerability to get around Microsoft Defender SmartScreen and install harmful software on victims’ computers.
The infection begins with a deceptive email that looks like it comes from someone you trust. The email is designed to tempt you into clicking a link, which leads you to open an internet shortcut file on a remote WebDAV share. When you open this file, it takes advantage of a vulnerability called CVE-2024-21212 and runs another file on the same WebDAV share, starting the infection process.
Cyble researchers reported that threat actors have been using a vulnerability to bypass Microsoft Defender SmartScreen and install harmful programs on victims’ computers.
The campaign targets Spanish taxpayers, transportation companies, and individuals in Australia using lure documents. These documents mimic emails from the U.S. Department of Transportation and official Medicare enrollment forms. full report here.
Source: Cyble
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind