The US cybersecurity agency, CISA, added a flaw in NextGen Healthcare’s Mirth Connect product to its catalog of Known Exploited Vulnerabilities (KEV).
A vulnerability in the open source product, known as CVE-2023-43208, allows remote code execution without authentication due to a data deserialization problem. A patch was rolled out with the release of version 4.4.1.
By infosecbulletin
/ Tuesday , June 3 2025
In March 2025, the Threatfabric mobile Threat Intelligence team identified Crocodilus, a new Android banking Trojan designed for device takeover....
Read More
By infosecbulletin
/ Tuesday , June 3 2025
Qualcomm has issued security patches for three zero-day vulnerabilities in the Adreno GPU driver, affecting many chipsets that are being...
Read More
By infosecbulletin
/ Monday , June 2 2025
Roundcube Webmail has fixed a critical security flaw that could enable remote code execution after authentication. Disclosed by security researcher...
Read More
By infosecbulletin
/ Sunday , June 1 2025
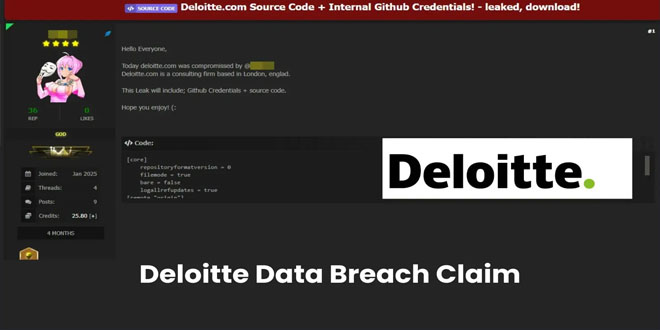
A hacker known as "303" claim to breach the company's systems and leaked sensitive internal data on a dark web...
Read More
By infosecbulletin
/ Sunday , June 1 2025
CISA and ACSC issued new guidance this week on how to procure, implement, and maintain SIEM and SOAR platforms. SIEM...
Read More
By infosecbulletin
/ Saturday , May 31 2025
The Qualys Threat Research Unit (TRU) found two local information-disclosure vulnerabilities in Apport and systemd-coredump. Both issues are race-condition vulnerabilities....
Read More
By infosecbulletin
/ Saturday , May 31 2025
New ransomware payment reporting rules take effect in Australia yesterday (May 30) for all organisations with an annual turnover of...
Read More
By infosecbulletin
/ Saturday , May 31 2025
Global makers of surveillance gear have clashed with Indian regulators in recent weeks over contentious new security rules that require...
Read More
By infosecbulletin
/ Thursday , May 29 2025
GreyNoise has discovered a campaign where attackers have gained unauthorized access to thousands of internet-exposed ASUS routers. This seems to...
Read More
By infosecbulletin
/ Wednesday , May 28 2025
The rise of online gambling in the country is leading to increased crime and societal issues. In response, the central...
Read More
In October 2023, cybersecurity company Horizon3.ai alerted healthcare companies about a flaw called CVE-2023-43208. It is a variation of another flaw called CVE-2023-37679, which was fixed in Mirth Connect version 4.4.0.
Horizon3.ai described the vulnerability as easily exploitable and warned that attackers would likely exploit it to gain access or compromise sensitive healthcare data.
The security firm identified over 1,200 cases of NextGen Mirth Connect exposed on the internet.
Horizon3.ai released technical details and proof-of-concept (PoC) code in mid-January 2024. Shortly after, The Shadowserver Foundation found over 440 internet-exposed instances affected by CVE-2023-43208.
CISA added CVE-2023-43208 to its catalog and told government agencies to fix it by June 10.
The agency has not provided any information about the attacks. Microsoft mentioned the exploitation of CVE-2023-37679 and CVE-2023-43208 in a brief report in April.
Microsoft reported that Mirth Connect and other vulnerabilities were exploited by a China-based threat actor known as Storm-1175, who has used Medusa ransomware.
CISA may know about other attacks, but their KEV catalog does not mention ransomware exploitation. The CVE-2023-37679 flaw has not been added to the catalog yet.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind