India has experienced a 138% rise in cyberattacks on government bodies from 2019 to 2023. This increase has prompted a response from the government, detailed in a recent report to the Rajya Sabha. From 2019 to 2023, cyberattacks on Indian government entities surged from 85,797 to 204,844, indicating a significant …
Read More »Google unveils ‘mindboggling’ quantum computing chip
Google has made a quantum computing chip that can finish tasks in five minutes, which would take conventional computers 10 undecillion (10,000,000,000,000,000,000,000,000 years) to complete. That’s 10 septillion years, a number much larger than the age of our universe, leading scientists behind a recent quantum computing breakthrough to describe it …
Read More »New DroidBot malware to attack 77 banks and CES globally
DroidBot is a sophisticated Android Remote Access Trojan (RAT) that merges traditional hidden VNC and overlay functions with spyware-like features. It includes a keylogger and monitoring tools for intercepting user actions, making it effective for surveillance and stealing credentials. A key feature of DroidBot is its dual-channel communication: it uses …
Read More »Deloitte faces alleged cyber incident, claimed over 1tb stolen
Brain Cipher, a ransomware group that emerged in June 2024, claims to have stolen 1TB of data from Deloitte UK, but this has not been verified. Deloitte, a top professional services firm, is the newest victim listed on Brain Cipher’s dark web site. Hackers claim to have stolen over 1TB …
Read More »Uganda confirms hack of central bank accounts, Refutes $17 Million Claim
Uganda’s finance ministry confirmed media reports that hackers breached the central bank’s systems and stole money, but refuted the claims to steal the money as much as $17 million. Uganda’s Minister of State for Finance, Henry Musasizi, addressed media reports alleging that a Southeast Asian hacker group hacked the Bank …
Read More »CIRT-in flags Critical Flaw in Oracle Agile PLM Framework
CERT-In has flagged a security vulnerability in Oracle’s Agile Product Lifecycle Management (PLM) software, identified as CVE-2024-21287 and cataloged as CIVN-2024-0350. This high-risk threat was detected on November 26, 2024. CVE-2024-21287 affects Oracle Agile PLM Framework version 9.3.6, which is commonly used by organizations for managing product lifecycles and enhancing …
Read More »Microsoft patches four vulnerabilities in its services
On November 26th, Microsoft patched four vulnerabilities detected in Dynamics 365 Sales, the Partner.Microsoft.Com portal, Microsoft Copilot Studio and Azure PolicyWatch. Microsoft Copilot Studio, a platform for developers to create AI agents and speed up coding with automation, had a critical vulnerability rated 9.3 out of 10 (CVE-2024-49038). Microsoft has …
Read More »Cloudflare logs faces major failure, losing 55% of user data
Cloudflare suffered an incident roughly 3.5 hours On November 14, 2024 impacting the majority of customers using Cloudflare Logs. Cloudflare lost about 55% of the logs normally send to customers were not sent and were lost on that incident. Log services are crucial for network operations, helping businesses analyze traffic, …
Read More »RomCom Exploits Firefox and Windows Zero-Day
According to ESET, Russia linked Ramcom exploit the two zero days of Mozilla FireFox and Microsoft Window addressed CVE 2024-9680, and 2024-49039. “In a successful attack, if a victim browses a web page containing the exploit, an adversary can run arbitrary code – without any user interaction required (zero click) …
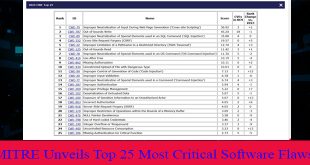
Read More »MITRE discloses 2024 CWE Top 25 critical software flaw
MITRE identified Cross-site scripting as the most critical software flaw in its recent published report of the past year. The nonprofit published its latest ranking of the Top 25 Most Dangerous Software Weaknesses on November 20, highlighting critical flaws from the Common Weakness Enumeration (CWEs) catalog between June 2023 and …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind