LockBit leaked stolen data from Boeing, a major aerospace company that provides services for commercial airplanes and defense systems. LockBit hackers informed Boeing that they would leak data and threatened to release a sample of the latest 4GB files.
Backup data published
LockBit ransomware has leaked more than 43GB of files from Boeing after the company refused to pay a ransom. The hacker group’s leak site has a lot of data backups for different systems. The newest backups have a timestamp of October 22.
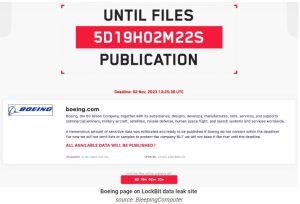
On October 27, the ransomware group posted Boeing on their website. They asked the company to contact them and negotiate before November 2nd. The hackers said at the time they had stolen “a tremendous amount of sensitive.
Boeing was temporarily removed from LockBit’s list of targets, but it was added back on November 7. The hackers stated that their warnings had been disregarded.
When the company continued to be silent, the LockBit ransomware gang decided to show that they had a bargaining chip and threatened to publish “just around 4GB of sample data (most recent).”
The hackers also threatened that they would publish the databases “if we do not see a positive cooperation from Boeing.”

On November 10, LockBit published all the data they obtained from Boeing on their website. This includes backup files for IT management software configurations and logs for monitoring and auditing tools.
The recently disclosed Citrix Bleed vulnerability (CVE-2023-4966) has sparked speculation about LockBit ransomware using it. Proof-of-concept exploit code for this vulnerability was published on October 24.
Boeing acknowledged the cyberattack but did not give any information about how it happened or how the hackers penetrated their network.
LockBit is one of the most resilient ransomware-as-a-service (RaaS) operations, having been active for more than four years and making thousands of victims across various sectors.
The victims include Continental, the UK Royal Mail, the Italian Internal Revenue Service, and the City of Oakland.
In June, the U.S. government reported that a gang extorted approximately $91 million since 2020. They carried out nearly 1,700 attacks on different organizations in the country.
The gang operates globally. In August, the Spanish police warned about a phishing campaign that targeted architecture firms in Spain using LockBit’s locker malware to encrypt systems.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














