Britain’s security officials have ordered that Apple create a so-called ‘back door’ allowing them to retrieve all the content any Apple user worldwide has uploaded to the cloud, The Washington Post reported on Friday citing people familiar with the matter. Rather than break the security promises it made to its …
Read More »
(CVE-2024-21413), (CVE-2025-0411)
Microsoft Outlook and 7 zip Vuln actively exploited; CISA Warns
A critical vulnerability (CVE-2025-0411) in the file archiving tool 7-Zip is being actively exploited, mainly targeting Ukrainian organizations. It has been included in CISA’s database of known exploited vulnerabilities. This flaw lets attackers bypass Windows’ Mark-of-the-Web (MoTW) security, allowing them to run malicious code. CISA has added CVE-2025-0411, a critical …
Read More »Hacker Claims 20 Million OpenAI Logins for sale
A threat actor has reportedly acquired login details, including passwords and email addresses, for 20 million OpenAI accounts. GBHackers report states that an underground forum user claimed to sell a sample of data and the full batch for a low price. The authenticity of these claims is unverified, but the situation …
Read More »Cisco Patches Critical Identity Services Engine (ISE) Vulnerabilities
Cisco has updated its Identity Services Engine (ISE) to fix two critical security flaws that could let remote attackers execute arbitrary commands and gain elevated privileges on affected devices. The vulnerabilities are listed below: CVE-2025-20124 (CVSS score: 9.9): A vulnerability in a Cisco ISE API that allows an authenticated attacker …
Read More »Paragon spyware targeted victims in dozens of European countries: Italy says
WhatsApp revealed that seven Italians, along with victims from over a dozen other European countries, were targeted by spyware in a widespread hacking campaign, according to the Italian government. Italy’s cybersecurity agency, Agenzia per la Cybersicurezza Nazionale (ANC), is investigating alleged hacking attempts by Paragon Solutions, according to a statement …
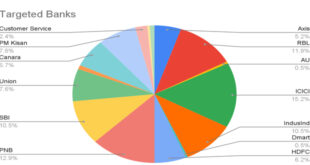
Read More »Sophisticated malware attack on Indian Banks; Exposes 50,000 users
The zLabs research team found a mobile malware campaign with nearly 900 malware samples aimed at Indian bank users. Analysis shows shared code, interfaces, and logos, indicating a single group behind the attacks on Android devices. Zimperium’s detection engine successfully identified these as Trojan Bankers targeting Indian financial institutions. This …
Read More »OPA Gatekeeper Bypass Unveils Risks in Kubernetes Policy Engines
A recent Aqua Security report highlights major security risks in Kubernetes policy enforcement, especially with Open Policy Agent (OPA) Gatekeeper. Although OPA Gatekeeper is commonly used for security policies in Kubernetes, researchers found methods to bypass its controls due to frequent misconfigurations and weak policies. According to the report, “Implementing …
Read More »
(CVE-2025-23419)
F5 Warns of TLS Session Resumption Vulnerability in NGINX
F5 has warned of a vulnerability in NGINX, a widely used web server software. The issue, known as CVE-2025-23419, could let attackers bypass client certificate authentication and gain unauthorized access to sensitive resources. When name-based virtual hosts are configured to share the same IP address and port combination, with TLS …
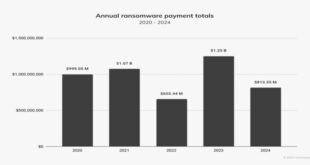
Read More »Ransomware payments statistics for 2024, a drop of 35%
Ransomware payments dropped by 35% last year compared to 2023, despite an increase in the number of attacks, according to a new report from Chainalysis. Despite claims from cybersecurity firms that ransomware activity peaked in 2024, there has been a significant drop in extortion payments. Chainalysis also noted in its …
Read More »CISA Adds 4 Actively Exploited Vuls to KEV Catalog
CISA added four security flaws to its Known Exploited Vulnerabilities (KEV) catalog, noting they are actively being exploited. The list of vulnerabilities is as follows: CVE-2024-45195 (CVSS score: 7.5/9.8) – (A vulnerability in Apache OFBiz that lets a remote attacker gain unauthorized access and run code on the server, fixed …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind