Staff Reporter: Blockchain technology is a promising new technology with the potential to revolutionize the financial sector. However, there are a number of challenges that need to be overcome in order to realize these benefits. By understanding the potential benefits and challenges of blockchain technology, financial institutions can position themselves …
Read More »Samsung Smartphone Users at Risk of Hacking, Update Now to Protect Yourself
Samsung smartphone users have been warned by the vendor and the US Cyber security and Infrastructure Security Agency (CISA) about a vulnerability that is being actively exploited in attacks. The vulnerability, which is tracked as CVE-2023-21492, is a kernel pointer exposure issue related to log files. It can allow a …
Read More »ExtraHop Releases New Tool to Defend Against ChatGPT Data Leaks
In response to the increasing prevalence of ChatGPT and the associated risks of data leaks, ExtraHop has launched Reveal(x), a cutting-edge solution that offers organizations visibility into their network devices and users connecting to OpenAI domains. The popularity of ChatGPT has skyrocketed, with 1 billion customers reached in a mere …
Read More »Hacking competetion held at MIST: Red Rebel secure first place
Ensuring cyber security is one of the most challenging issues for any country in the modern world. The Ministry of Posts, Telecommunications and Information Technology of the Government of the People’s Republic of Bangladesh has taken various contemporary programs related to cyber security, realizing the importance of the issue with …
Read More »World CyberCon, Middle East-2023, 30 August, Riyadh, Saudi Arabia
As we progress into an era of dynamic global connectivity, the need for cyber security is more evident now than ever before. With the level of sophistication and complexity of cyber-crimes evolving rapidly, it is no longer just a concern but a necessity to be aware of the destructive ability …
Read More »Cloudflare Unveils New Secrets Management Solution
Cloudflare on Thursday announced Secrets Store, a new solution designed to help developers and organizations securely store and manage secrets across the Cloudflare platform. Any variable that needs to be stored securely and accessed by authorized users only is considered a secret, including credentials, cryptographic keys, tokens, and more. Failure …
Read More »Apple Patches 3 Exploited WebKit Zero-Day Vulnerabilities
Apple on Thursday released security updates for its operating systems to patch dozens of vulnerabilities that could expose iPhones and Macs to hacker attacks, including three zero-days affecting the WebKit browser engine. Two of the actively exploited vulnerabilities, CVE-2023-28204 and CVE-2023-32373, have been reported to the tech giant by an …
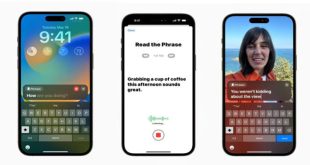
Read More »just 15 minutes new iPhone feature will clone your voice
The new feature, which will allow iPhone and iPad users to generate synthetic versions of their voices, is part of a larger update aimed at making sure people with disabilities get the most from their Apple devices. Personal Voice will allow users at risk of losing their ability to speak, …
Read More »Daily Cybersecurity Roundup, May 18, 2023
Ransomware actors have been running rampant targeting every sector left, right, and center. In today’s edition, a technology provider fell prey to one, locking customers out of portals and websites. In other news, the threat actor linked to the Triada trojan infected millions of phones – thanks to a preinstalled …
Read More »OpenAI, creator of ChatGPT, teaches prompt engineering for FREE
Generative AI and conversational AI chatbots are growing in popularity. ChatGPT has shown just how powerful artificial intelligence-based chatbots can be right after they hit the market. And with the increasing popularity of ChatGPT, the career that is now being sought after is prompt engineering. Just last month, a job …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind