The Forum of Incident Response and Security Teams (FIRST) has recently announced the release of CVSS v4.0, the latest version of the Common Vulnerability Scoring System (CVSS) standard. This update comes more than eight years after the release of CVSS v3.0 in June 2015.
Version 4.0 of CVSS aims to improve vulnerability assessment for both industry and the public, according to FIRST.
By infosecbulletin
/ Monday , May 12 2025
Google will pay about $1.4 billion to Texas to settle two lawsuits regarding location tracking and biometric data storage without...
Read More
By infosecbulletin
/ Friday , May 9 2025
YouTube has restricted access to at least four Bangladeshi television channels in India following a takedown request from the Indian...
Read More
By infosecbulletin
/ Friday , May 9 2025
Microsoft has fixed critical vulnerabilities in its core cloud services, including Azure Automation, Azure Storage, Azure DevOps, and Microsoft Power...
Read More
By infosecbulletin
/ Thursday , May 8 2025
The cyber threat landscape is rapidly changing, with a notable increase in ransomware activity in April 2025, driven by the...
Read More
By infosecbulletin
/ Thursday , May 8 2025
SonicWall has released patches for three security flaws in SMA 100 Secure Mobile Access appliances that could allow remote code...
Read More
By infosecbulletin
/ Thursday , May 8 2025
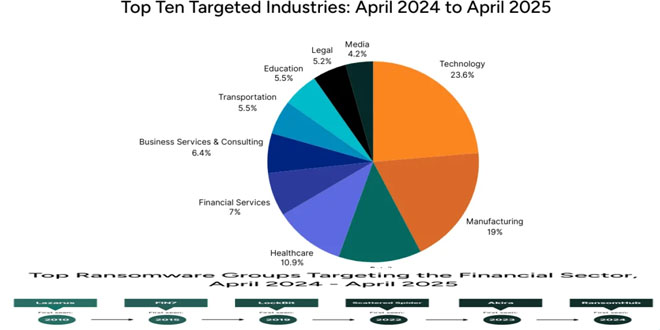
From April 2024 to April 2025, Flashpoint analysts noted that the financial sector was a major target for threat actors,...
Read More
By infosecbulletin
/ Thursday , May 8 2025
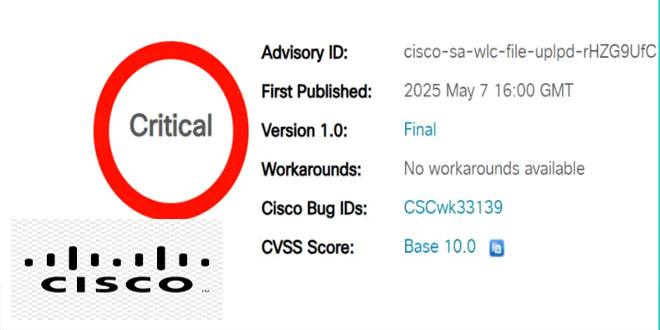
Cisco has issued a security advisory for a critical vulnerability in its IOS XE Software for Wireless LAN Controllers (WLCs)....
Read More
By infosecbulletin
/ Wednesday , May 7 2025
Attackers linked to the Play ransomware operation deployed a zero-day privilege escalation exploit during an attempted attack against an organization...
Read More
By infosecbulletin
/ Wednesday , May 7 2025
Hackers are exploiting an unauthenticated remote code execution vulnerability in the Samsung MagicINFO 9 Server to take control of devices...
Read More
By infosecbulletin
/ Tuesday , May 6 2025
CISA added the Langflow vulnerability, CVE-2025-3248 (CVSS score 9.8), to its Known Exploited Vulnerabilities catalog. Langflow is a popular tool...
Read More
CVSS is used to measure the severity of security vulnerabilities. It assigns a numerical score to each vulnerability, which can be translated into levels like low, medium, high, and critical. This helps organizations prioritize their vulnerability management.
In July 2019, an important update was made to CVSS v3.1. It highlighted that CVSS is meant to gauge the seriousness of a vulnerability and should not be the sole factor in evaluating risk.
CVSS v3.1 has received criticism for its scoring scale and for not properly representing health, human safety, and industrial control systems.
The new standard has added extra metrics to assess vulnerabilities. These metrics include Safety (S), Automatable (A), Recovery (R), Value Density (V), Vulnerability Response Effort (RE), and Provider Urgency (U).
It introduces new names for scoring CVSS. The new names are Base (CVSS-B), Base + Threat (CVSS-BT), Base + Environmental (CVSS-BE), and Base + Threat + Environmental (CVSS-BTE).
“The recommended approach is to emphasize that CVSS encompasses more than just the Base score, and this terminology should be employed whenever a numerical CVSS value is presented or conveyed.”
“The CVSS Base Score should be considered in conjunction with the analysis of the environment and attributes that may change over time.”
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind