Group-IB, a global cybersecurity leader headquartered in Singapore, has identified 101,134 stealer-infected devices with saved ChatGPT credentials. Group-IB’s Threat Intelligence platform found these compromised credentials within the logs of info-stealing malware traded on illicit dark web marketplaces over the past year. The number of available logs containing compromised ChatGPT accounts reached a peak of 26,802 in May 2023. According to Group-IB’s findings, the Asia-Pacific region has experienced the highest concentration of ChatGPT credentials being offered for sale over the past year.
Group-IB’s experts highlight that more and more employees are taking advantage of the Chatbot to optimize their work, be it software development or business communications. By default, ChatGPT stores the history of user queries and AI responses. Consequently, unauthorized access to ChatGPT accounts may expose confidential or sensitive information, which can be exploited for targeted attacks against companies and their employees. According to Group-IB’s latest findings, ChatGPT accounts have already gained significant popularity within underground communities.
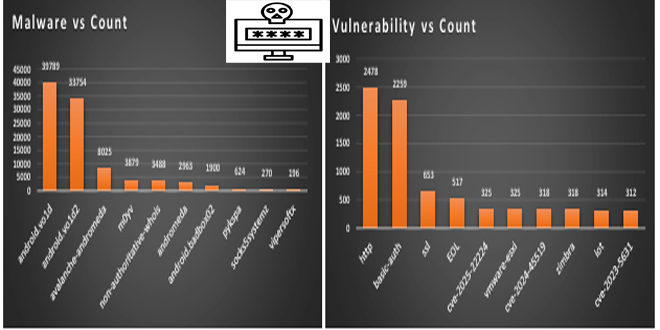
Group-IB’s Threat Intelligence platform stores the industry’s largest library of dark web data, monitors cybercriminal forums, marketplaces, and closed communities in real time to identify compromised credentials, stolen credit cards, fresh malware samples, access to corporate networks, and other critical intelligence that enables companies to identify and mitigate cyber risks before further damage is done. Group-IB’s analysis of underground marketplaces revealed that the majority of logs containing ChatGPT accounts have been breached by the infamous Raccoon info stealer. The growing popularity of the AI-powered chatbot is evident in the consistent increase of compromised ChatGPT accounts observed by the Group-IB Threat Intelligence team throughout the past year.

Info stealers are a type of malware that collects credentials saved in browsers, bank card details, crypto wallet information, cookies, browsing history, and other information from browsers installed on infected computers, and then sends all this data to the malware operator. Stealers can also collect data from instant messengers and emails, along with detailed information about the victim’s device. Stealers work non-selectively. This type of malware infects as many computers as possible through phishing or other means in order to collect as much data as possible. Info stealers have emerged as a major source of compromised personal data due to their simplicity and effectiveness. Logs containing compromised information harvested by info stealers are actively traded on dark web marketplaces. Additional information about logs available on such markets includes the lists of domains found in the log as well as the information about the IP address of the compromised host.
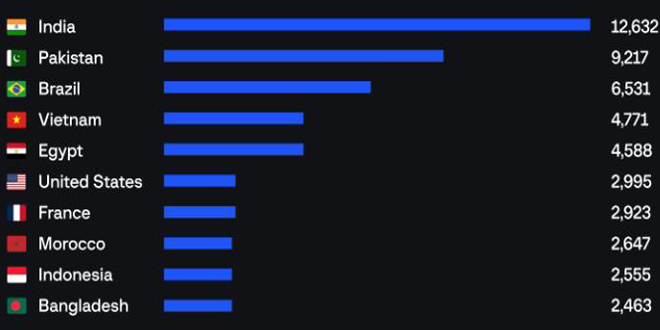
By analyzing this information, Group-IB’s Threat Intelligence unit identified the countries and regions with the highest concentration of stealer-infected devices with saved ChatGPT credentials. The Asia-Pacific region saw the largest number of ChatGPT accounts stolen by info stealers (40.5%) between June 2022 and May 2023.

“Many enterprises are integrating ChatGPT into their operational flow. Employees enter classified correspondences or use the bot to optimize proprietary code. Given that ChatGPT’s standard configuration retains all conversations, this could inadvertently offer a trove of sensitive intelligence to threat actors if they obtain account credentials. At Group-IB, we are continuously monitoring underground communities to promptly identify such accounts.”
To mitigate the risks associated with compromised ChatGPT accounts, Group-IB advises users to update their passwords regularly and implement two-factor authentication. By enabling 2FA, users are required to provide an additional verification code, typically sent to their mobile devices, before accessing their ChatGPT accounts.
Having visibility into dark web communities allows organizations to identify if their sensitive data or customer information is being leaked or sold. Real-time Threat Intelligence enables them to take proactive action to mitigate the impact, notify affected individuals, and strengthen their security posture to prevent further damage. Using real-time threat intelligence, companies can better understand the threat landscape, proactively protect their assets, and make informed decisions to strengthen their overall cybersecurity posture.
Source: Group IB
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind